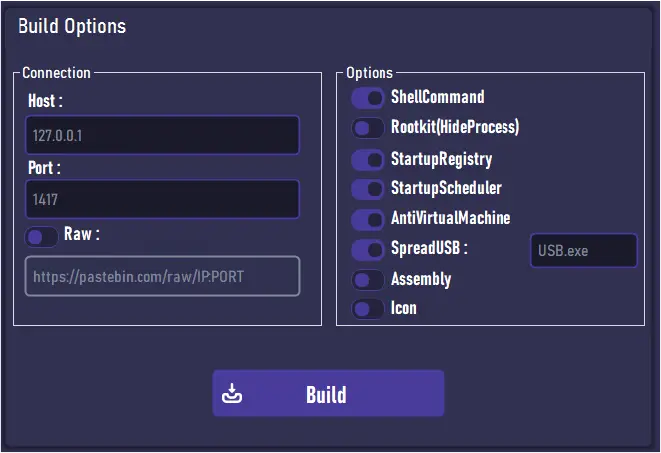
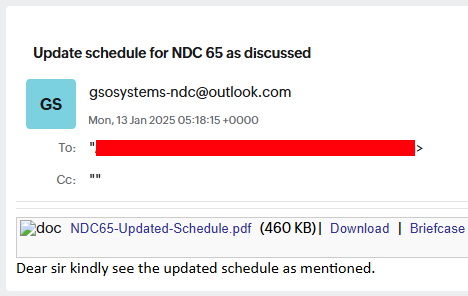
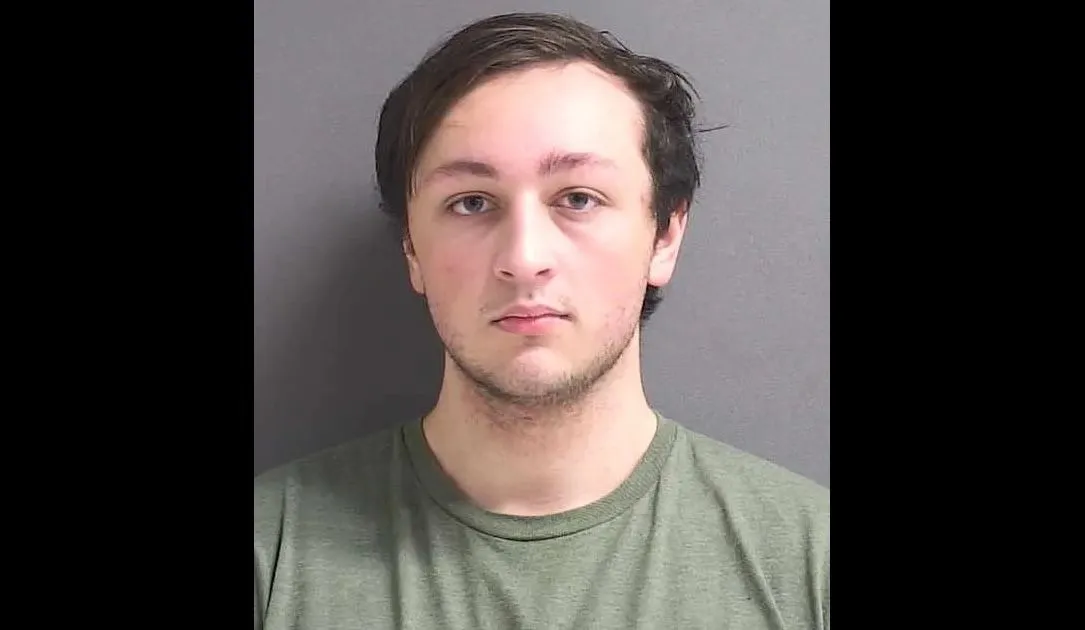
Summary: The US Treasury’s Office of the Comptroller of the Currency (OCC) experienced a significant email breach lasting over a year, involving unauthorized access to sensitive financial information through a compromised administrative account. The breach was confirmed on February 12, 2025, and has triggered a thorough review and analysis of impacted accounts.…
Read More