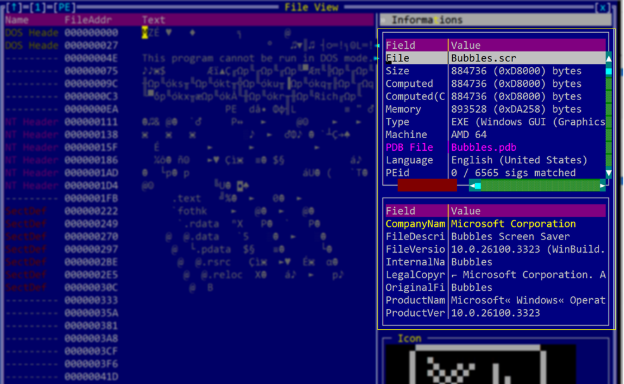
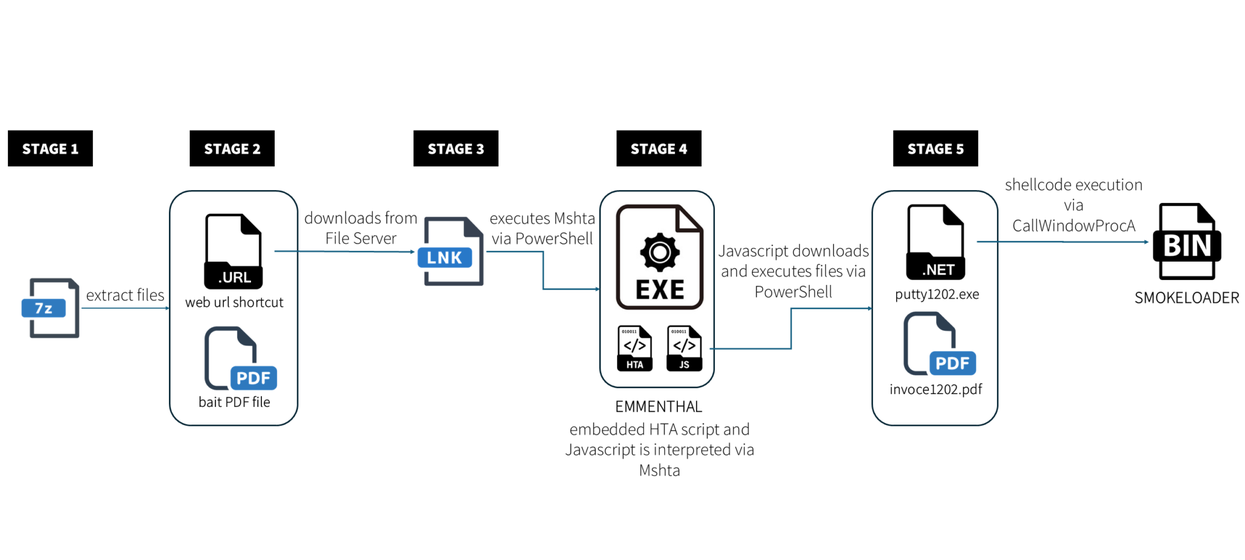
Keypoints :
April 3, 2025 advisory published by CISA, NSA, FBI, and other partners.…
This advisory from multiple cybersecurity agencies highlights the ongoing threat of fast flux techniques used by malicious actors, particularly ransomware groups like Hive and Nefilim. These methods complicate detection and disruption, necessitating improved collaboration and enhanced detection mechanisms among organizations. Affected: organizations, Internet service providers, cybersecurity service providers, financial sector, manufacturing sector, transportation sector
Read More