The Cofense Phishing Defense Center has reported an increase in phishing emails masquerading as communications from US Customs and Border Protection regarding the Electronic System for Travel Authorization (ESTA). These emails create urgency and fear to trick users into providing personal information through a fraudulent website.…
Read More Tag: EMAIL

Summary: Cybersecurity researchers have identified enhanced malware loaders, including Hijack Loader and SHELBY, that use advanced evasion tactics and innovative command-and-control methods. Hijack Loader introduces call stack spoofing and anti-VM checks, while SHELBY operates through GitHub for remote control and data exfiltration. Meanwhile, Emmenhtal loader has been distributing SmokeLoader via phishing emails using .NET…
Read More 
Summary: Google has announced a significant update to Gmail, introducing end-to-end encryption (E2EE) for enterprise users that simplifies the encryption process. This feature enables users to send E2EE emails not only within an organization but eventually to any email inbox, eliminating the need for custom software or certificate exchanges.…
Read More 
Summary: The Acronis Threat Research Unit (TRU) analyzed a complex malware delivery chain demonstrating the use of multiple scripting languages and obfuscation techniques, leading to the deployment of high-profile malware such as DCRat. The infection starts with a deceptive email attachment, escalating through a multi-stage process involving Visual Basic Script, batch files, and PowerShell.…
Read More
Summary: TRUeSentire’s Threat Response Unit has identified an advanced KoiLoader malware intrusion attempting to compromise systems through a phishing email. The attack leverages misleading file formats, manipulates PowerShell commands, and employs multiple anti-detection techniques to deploy the Koi Stealer for extensive data theft. KoiLoader exemplifies sophisticated malware engineering, utilizing custom cryptographic channels for Command and Control (C&C) operations.…
Read More 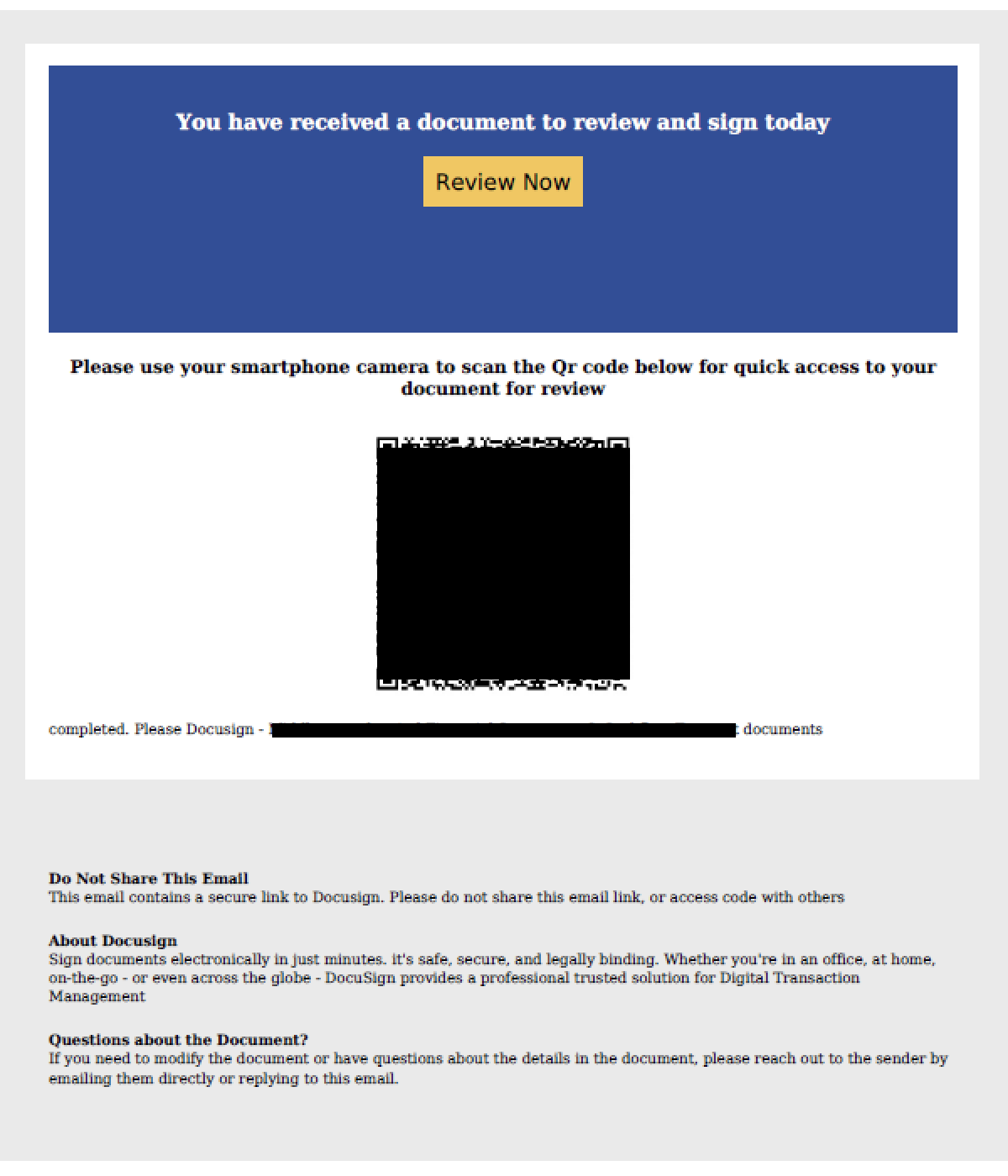
Researchers from Unit 42 have identified a rise in sophisticated phishing tactics that leverage QR codes and URL redirection to compromise user credentials. These methods obscure the true destination of phishing links, making it easier for attackers to deceive victims, particularly in sectors such as medical, automotive, education, energy, and finance.…
Read More 
Summary: Attackers are exploiting a critical authentication bypass vulnerability in CrushFTP, which can enable remote access for unauthenticated users on unpatched versions of the software. Users have been urged to apply patches to protect their systems, while existing exposed servers are being targeted by various exploitation attempts.…
Read More 
Summary: Google is rolling out a new end-to-end encryption (E2EE) model for Gmail enterprise users, simplifying the process of sending encrypted emails without complex certificate requirements. This new capability will allow encrypted emails to be sent to any user on any email platform, enhancing data privacy and security.…
Read More 
Summary: Russia’s state-owned railway, RZD, experienced a cyberattack that temporarily disrupted its website and mobile application, following a similar incident with Moscow’s subway system. The attack was identified as a distributed denial-of-service (DDoS) event, though ticket sales continued at physical locations. The perpetrator remains unknown, and RZD is working to restore its online services promptly.…
Read More 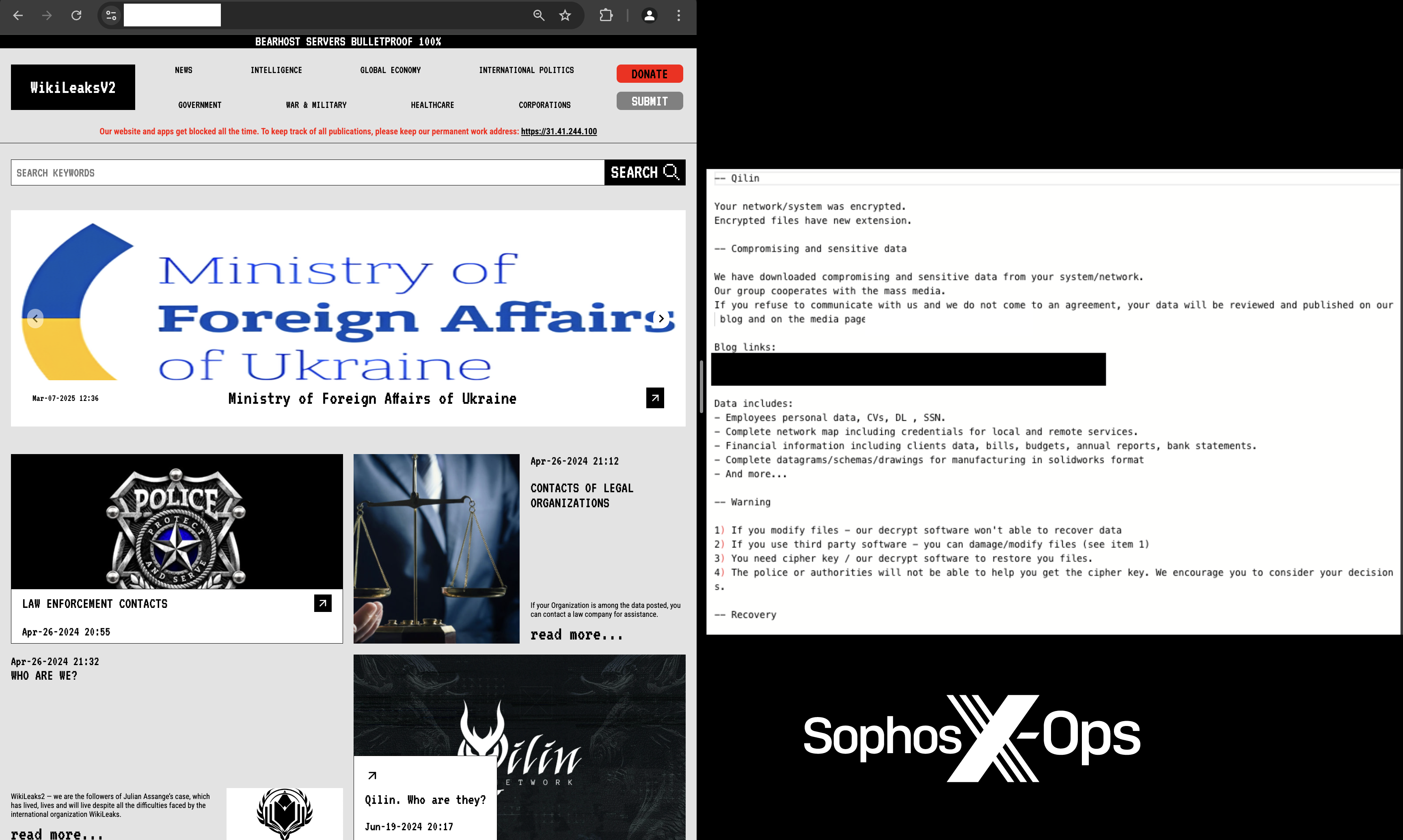
In late January 2025, an MSP administrator fell victim to a sophisticated phishing email that mimicked an authentication alert for a remote management tool, leading to a ransomware attack by Qilin actors. This incident emphasizes the vulnerabilities faced by MSPs and their clients to phishing campaigns.…
Read More 
Summary: The Shadowserver Foundation reported a surge in exploitation attempts targeting a recently patched vulnerability in CrushFTP, a file transfer solution. Despite ongoing updates and mitigations from CrushFTP, vulnerability intelligence firms have created CVE identifiers, leading to confusion in the cybersecurity community. As unpatched instances remain, CrushFTP has urged users to promptly apply available patches.…
Read More 
Summary: Xiaofeng Wang, a prominent computer scientist from Indiana University, and his wife Nianli Ma have mysteriously disappeared, raising concerns following the removal of their online profiles and an FBI raid on their homes. Their sudden absence has sparked widespread speculation among colleagues, with law enforcement providing minimal information.…
Read More 
Summary: Israeli cybersecurity firm Check Point responded to claims by a hacker named CoreInjection, who alleged the theft of sensitive data and was offering it for sale. Check Point refuted the claims, stating the data came from a prior incident in December 2024 and was not tied to any active breach.…
Read More 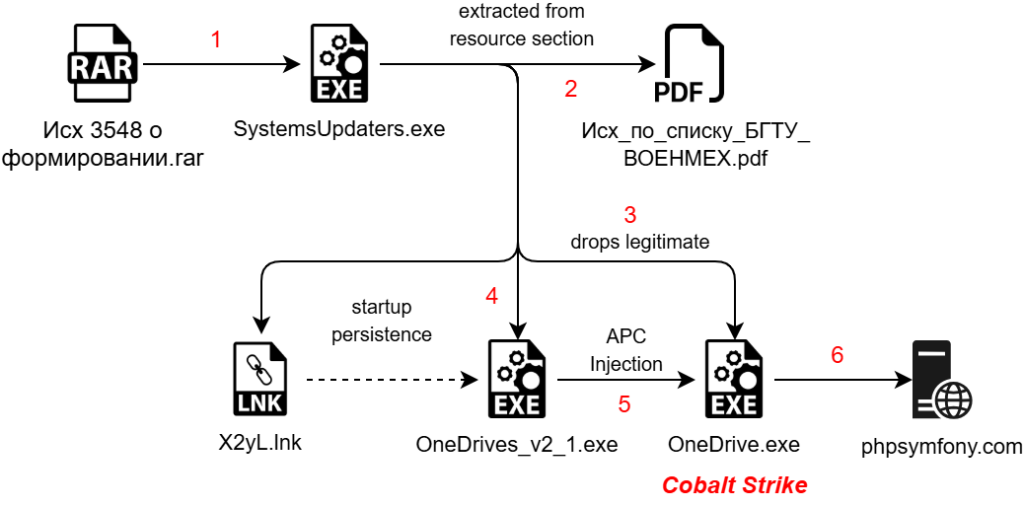
The article discusses Operation HollowQuill, a targeted cyber campaign against the Baltic State Technical University, designed to infiltrate academic and defense networks through weaponized decoy documents. The attack utilizes a multi-stage infection chain, including a malicious RAR file, a .NET malware dropper, Golang shellcode, and a Cobalt Strike payload.…
Read More 
AhnLab Security Intelligence Center (ASEC) uncovered Remcos malware camouflaged as a shipping waybill. The article outlines the distribution process involving HTML, JavaScript, and AutoIt scripts, ultimately leading to the execution of the Remcos malware. It emphasizes the importance of vigilance when handling emails from unfamiliar sources to prevent malware infection.…
Read More 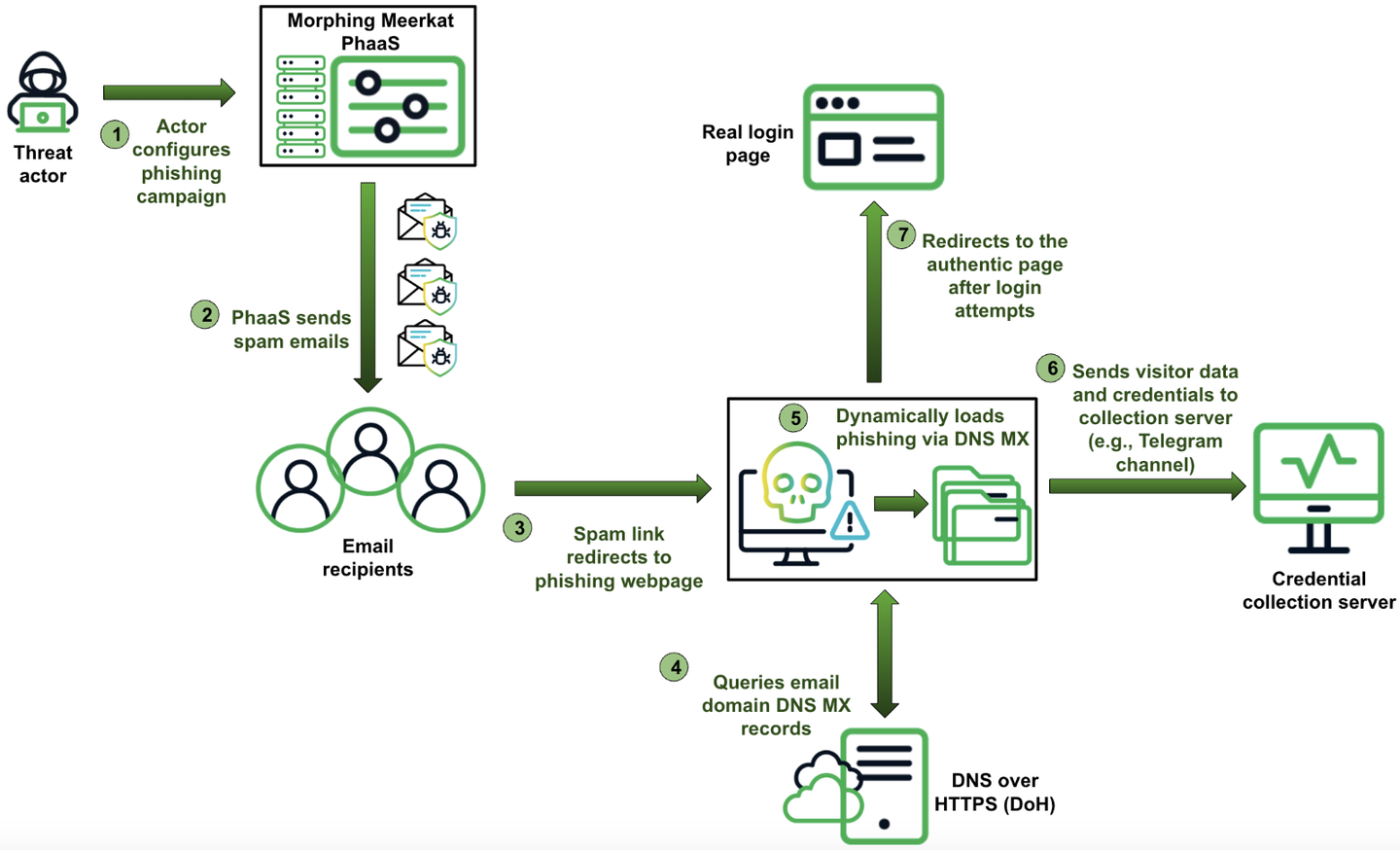
Summary: A recent report by Infoblox Threat Intelligence details a sophisticated phishing operation named Morphing Meerkat, which utilizes DNS techniques to create tailored phishing content for victims. The operation dynamically serves fake login pages mimicking over 100 brands, employing advanced methods to evade detection and enhance effectiveness.…
Read More 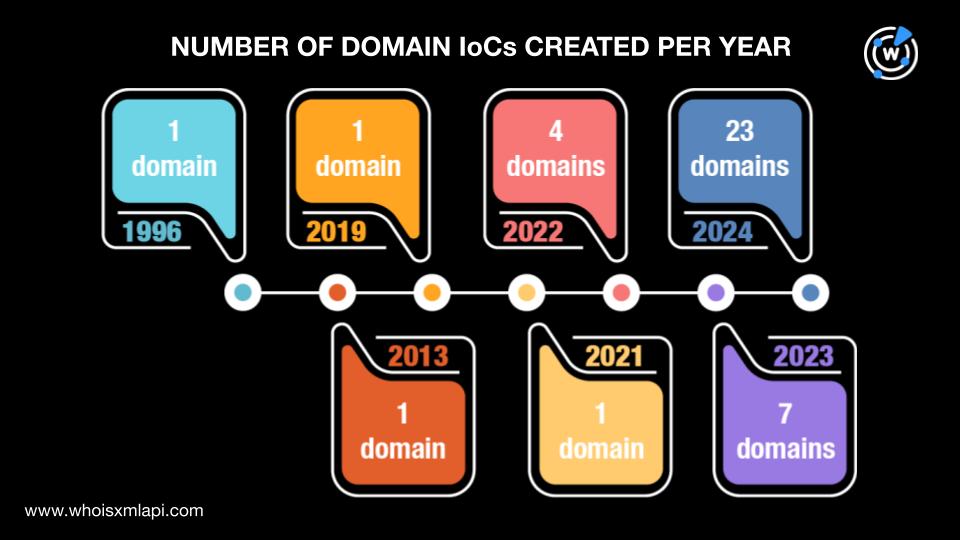
A recent investigation by Trend Micro researchers revealed a search engine optimization (SEO) manipulation campaign named BadIIS targeting users of Internet Information Services (IIS). This financially motivated campaign redirects victims to illegal gambling websites and has notably affected Asian countries such as India, Thailand, and Vietnam, with potential global repercussions.…
Read More 
Summary: A phishing-as-a-service (PhaaS) platform named ‘Lucid’ has emerged, targeting 169 entities across 88 countries through sophisticated phishing messages sent via iMessage and RCS. Operated by the XinXin group, this platform enables other cybercriminals to access over 1,000 phishing domains and tools through a subscription model.…
Read More 
Summary: A hacker known as ‘GHNA’ has leaked around 270,000 customer records from Samsung Germany’s ticketing system, sourced via compromised credentials from Spectos GmbH. The data breach stems from an incident in 2021 and includes sensitive personal and transaction information. Experts warn that the leaked data could facilitate various cyber threats, including phishing and account takeovers.…
Read More 
Summary: A recent phishing campaign targeting Ukrainian entities has been identified, utilizing social engineering techniques to distribute the Remcos RAT trojan. This campaign, attributed to the Russian hacking group Gamaredon, uses deceptive files related to military movements to trick victims. The campaign highlights ongoing cyber espionage efforts associated with Russian Intelligence Services against Ukraine.…
Read More