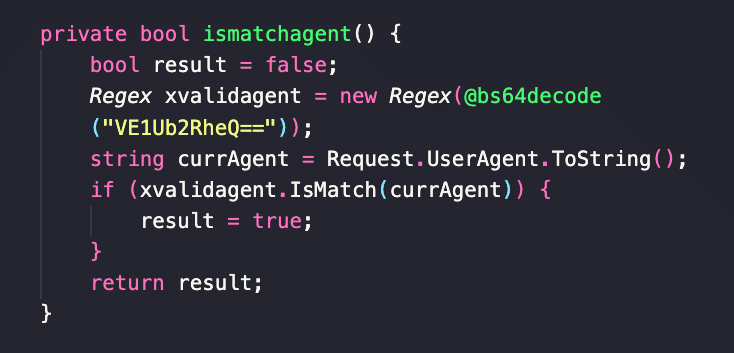
The article discusses the various threats posed by mining trojans that infiltrate victims’ computers, utilizing their resources for illegal cryptocurrency mining without their consent. It highlights the negative impacts on system performance, increased risk of failure, and potential for creating backdoors leading to further cyberattacks. The trend towards the use of sophisticated techniques like BYOVD attacks and the rise of dark web mining pools is emphasized.…
Read More