Keypoints :
A vulnerability (CVE-2025-30066) was discovered in tj-actions/changed-files on March 14, 2025.…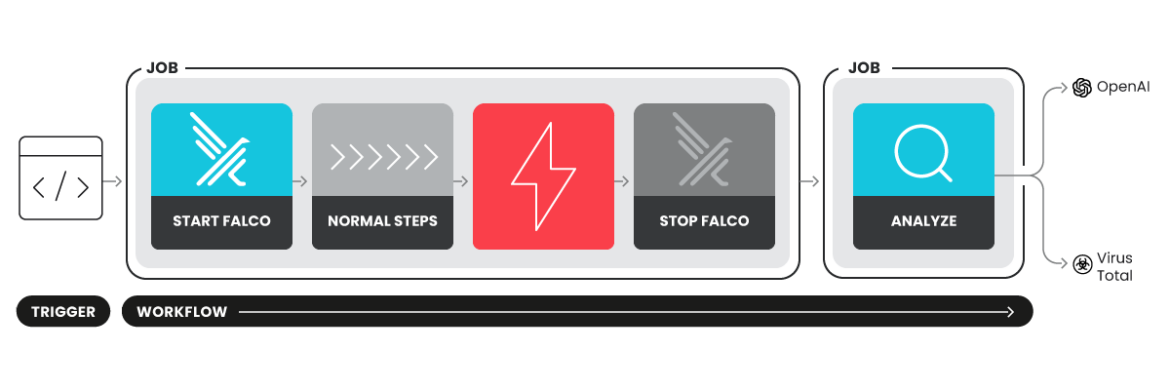
A vulnerability (CVE-2025-30066) was identified in the GitHub Action tj-actions/changed-files, affecting numerous repositories. This article discusses how Falco Actions can be integrated into CI/CD workflows to detect and respond to attacks like this one, providing enhanced visibility and security against potential threats. Affected: GitHub Actions, CI/CD environments, software repositories
Read More