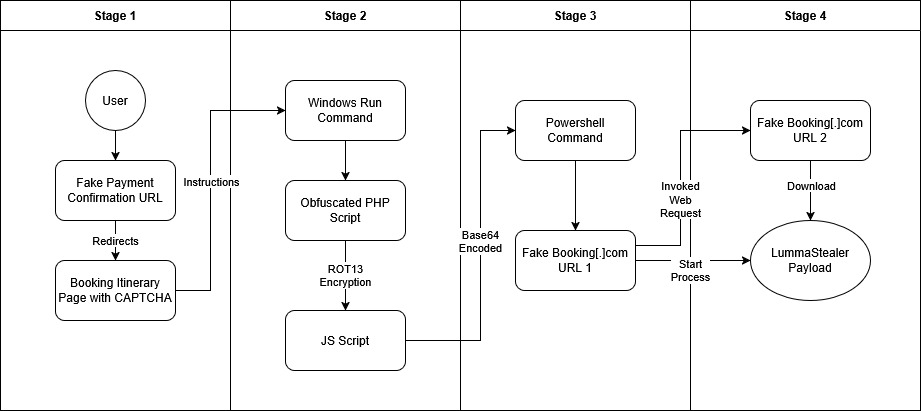
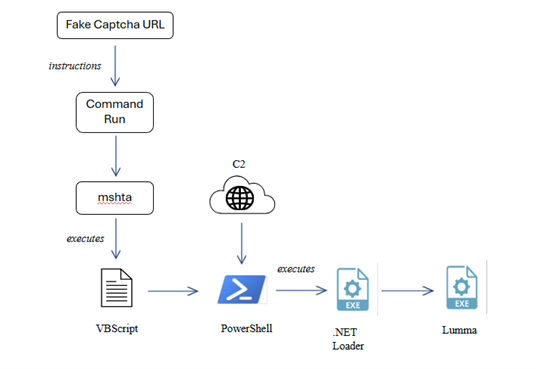
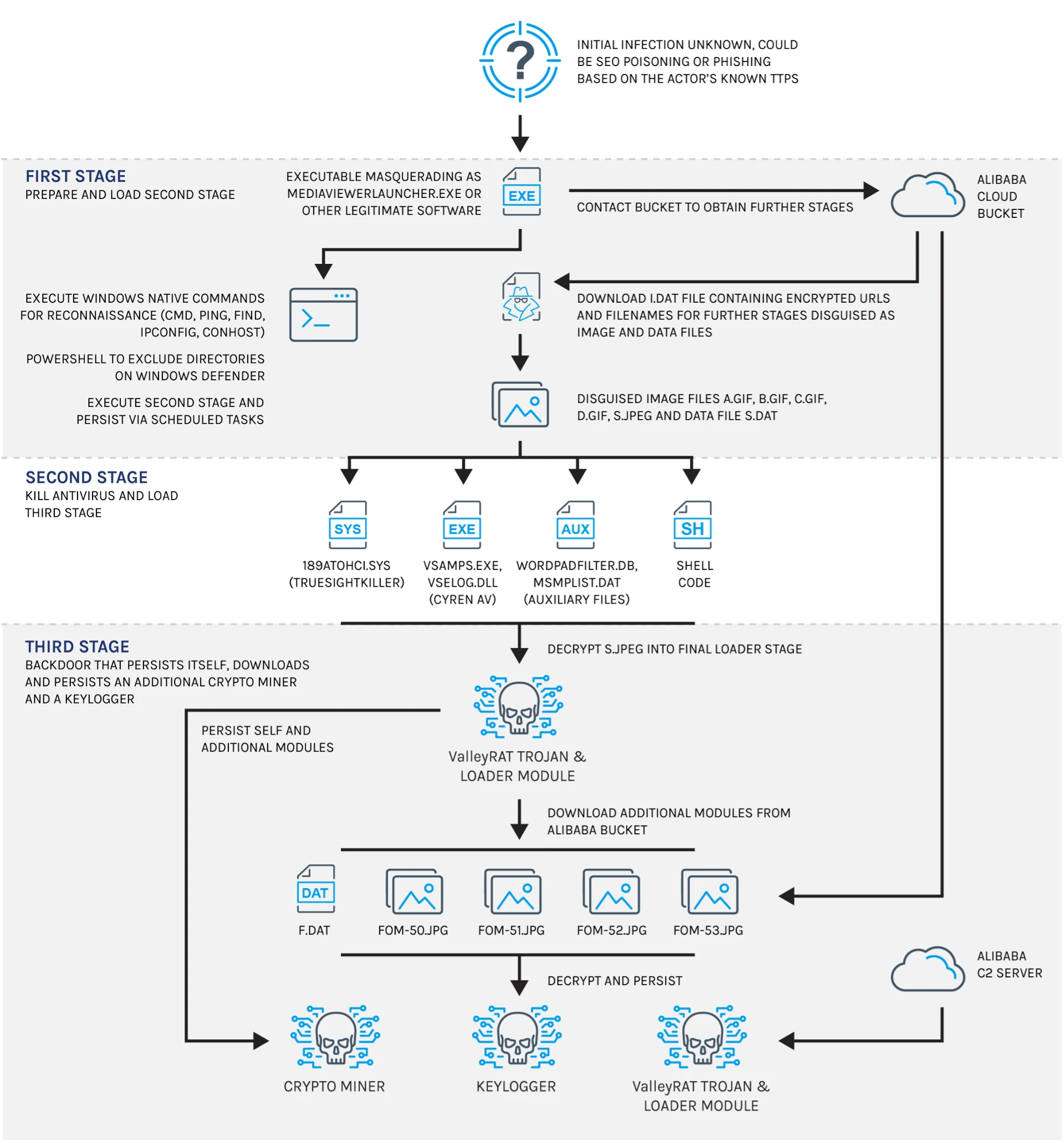
Sandworm, a threat actor linked to Russia’s GRU, has been conducting cyber espionage against Ukrainian Windows users by exploiting pirated software to distribute malware, notably the BACKORDER loader and Dark Crystal RAT. This activity has been ongoing since late 2023, coinciding with the Russian invasion of Ukraine, and highlights the vulnerabilities created by the country’s high rates of software piracy.…
Read More