Keypoints :
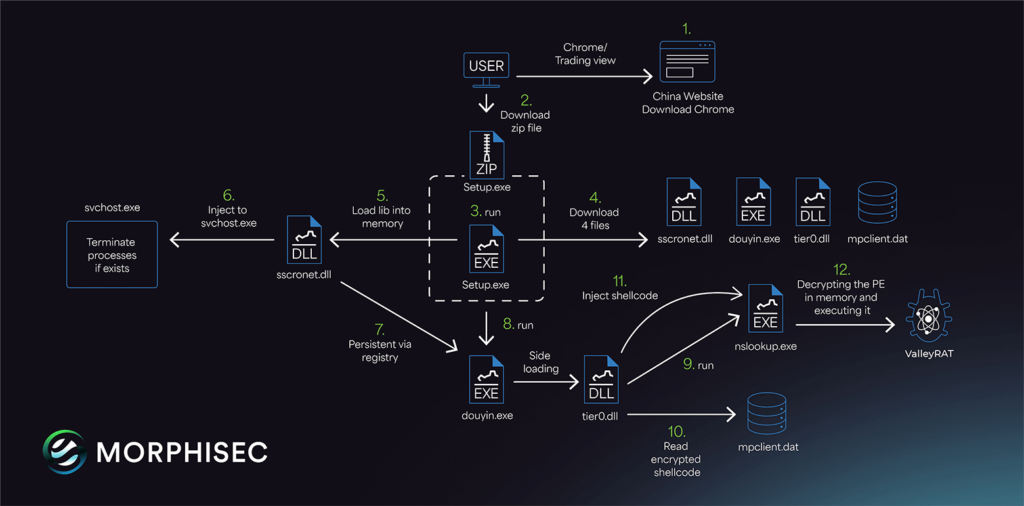
ResolverRAT employs advanced in-memory execution and dynamic resource handling to evade detection.…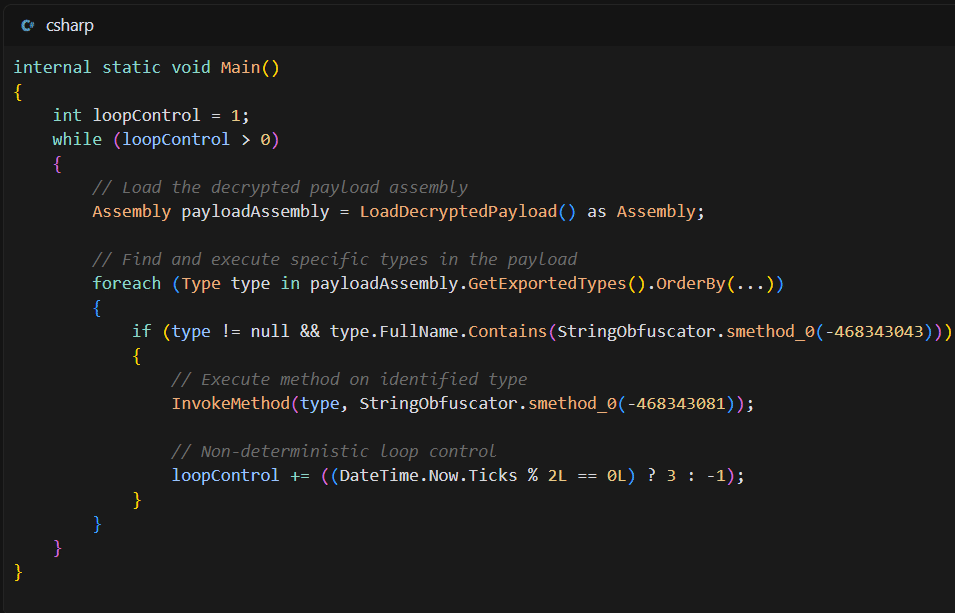
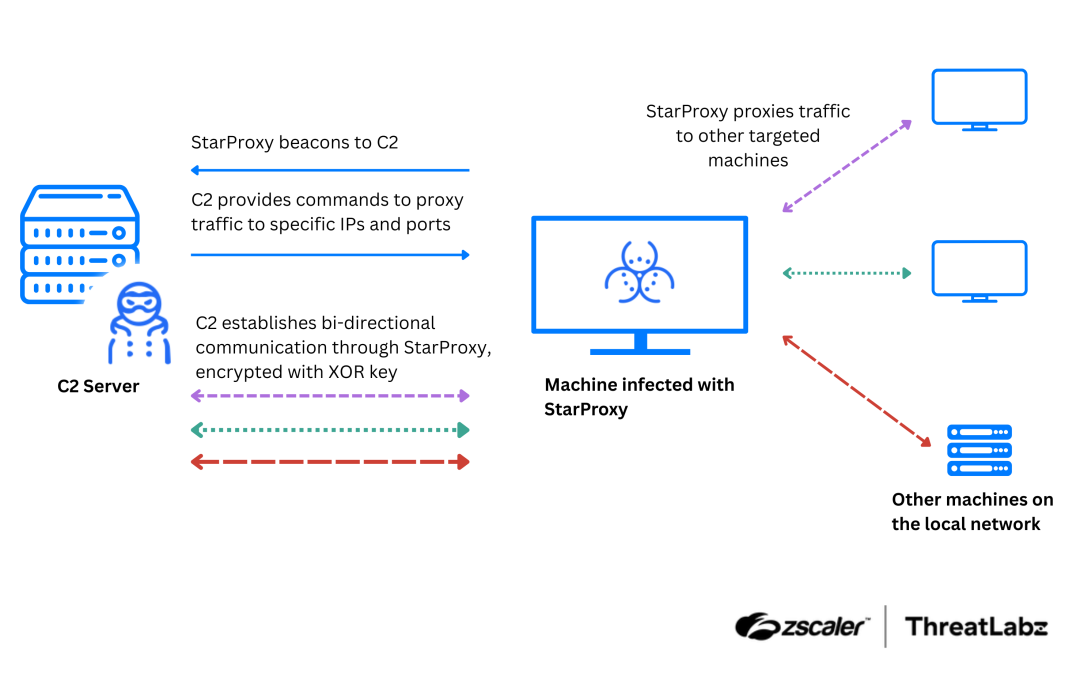
ResolverRAT is a newly discovered remote access trojan (RAT) that utilizes advanced evasion techniques and runtime resource resolution to avoid detection. This malware primarily targets employees in the healthcare and pharmaceutical sectors via localized phishing campaigns, employing significant social engineering tactics. Affected: healthcare sector, pharmaceutical sector
Read More