Summary: A recent dark web post claims that PT Bosowa Berlian Motor has suffered a significant data breach, involving the compromise of its database and website source code. The exposed data reportedly exceeds 5 GB, including SQL database files and a large number of tables. This incident raises concerns about the security of sensitive information related to one of Indonesia’s major automotive companies.…
Read More 

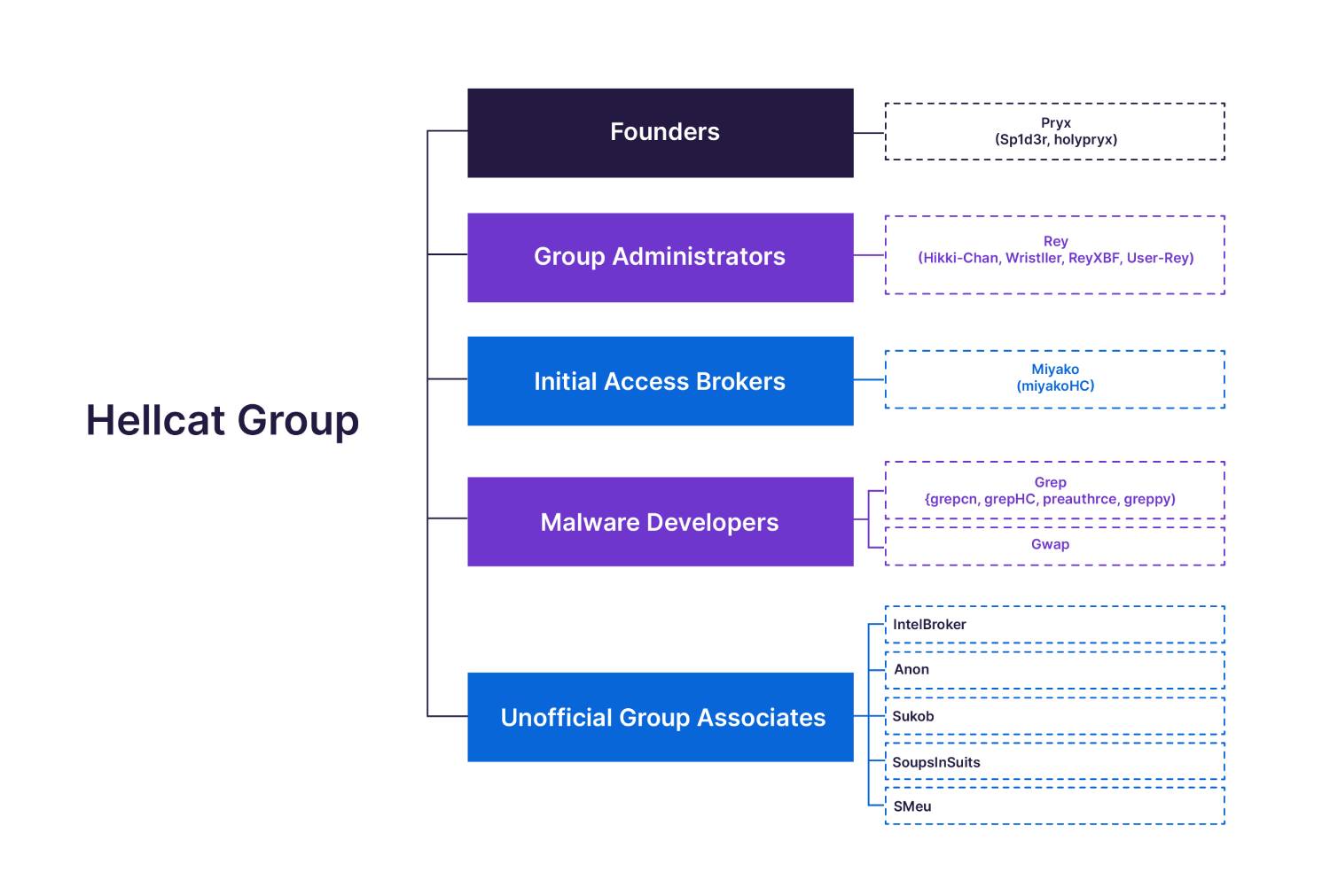

![[Law] The US sanctions Iranian man behind the Nemesis Dark Web marketplace [Law] The US sanctions Iranian man behind the Nemesis Dark Web marketplace](https://www.hendryadrian.com/tweet/image/cybersecuritynews.png)