Summary: The video discusses significant security vulnerabilities discovered in major software frameworks and tools, including a serious issue in the Nex.js JavaScript library, the acquisition of Whiz by Google, and critical vulnerabilities in the Ingress EngineX controller for Kubernetes, as well as a compromise of a popular GitHub action.…
Read More Tag: CVE
Summary: The video discusses the discovery of five critical vulnerabilities, collectively termed “Ingress Nightmare,” affecting the Ingress NGINX controller for Kubernetes. These vulnerabilities, which allow unauthenticated remote code execution, were revealed by a company called Whiz but did not have patches available at the time of the report.…
Read More 
Summary: Broadcom has released security updates for a severe authentication bypass vulnerability (CVE-2025-22230) affecting VMware Tools for Windows, allowing low-privileged attackers to escalate privileges. This flaw, caused by improper access control, affects VMware Tools versions 12.x.x and 11.x.x. Affected organizations are urged to update urgently, as exploitation in the wild may pose significant risks.…
Read More 
Summary: A high-severity privilege escalation vulnerability (CVE-2025-26512) has been identified in NetApp SnapCenter, impacting versions prior to 6.0.1P1 and 6.1P1. NetApp is urging users to update their systems immediately to prevent unauthorized access and potential exploitation. Software fixes are available via the NetApp Support website.
Read More Affected: NetApp SnapCenter users
Keypoints :
Vulnerability CVE-2025-26512 has a CVSS score of 9.9, indicating its severity.…
Summary: Apache VCL is facing critical security vulnerabilities, including an SQL injection flaw and a cross-site scripting (XSS) vulnerability. These flaws could lead to unauthorized data manipulation and system compromises. Immediate upgrading to version 2.5.2 is recommended to address these issues.
Read More Affected: Apache VCL versions 2.1 through 2.5.1
Keypoints :
Critical SQL injection vulnerability identified in the New Block Allocation form (CVE-2024-53678).…
Summary: A hacker named ‘rose87168’ has claimed to have breached Oracle Cloud, allegedly stealing data related to 6 million users, despite Oracle’s adamant denial of any breach. Multiple companies have confirmed the authenticity of the leaked data samples, including personal and account information. Evidence suggests that the threat actor had access to Oracle’s servers, raising serious questions about the security of the cloud platform.…
Read More 
Summary: The EncryptHub threat actor has exploited a zero-day vulnerability in Microsoft Windows (CVE-2025-26633) to deploy various malware, including Rhadamanthys and StealC. This attack leverages the Microsoft Management Console (MMC) to execute malicious payloads while maintaining persistence and stealing sensitive information from compromised systems. Trend Micro has identified this attack as MSC EvilTwin and is monitoring related Russian cyber activities.…
Read More 
Summary: Security researchers from Trend Micro have identified a zero-day vulnerability (CVE-2025-26633) that was exploited by the EncryptHub ransomware gang. This exploit targets the Microsoft Management Console (MMC) framework, allowing attackers to execute malicious code and exfiltrate data. The report indicates that the attack technique involves manipulating .msc…
Read More 
Summary: This article draws a parallel between the necessity of regular sparring in boxing and continuous penetration testing in cybersecurity. It emphasizes how infrequent testing can lead to the erosion of defenses and undetected vulnerabilities. To maintain a robust security posture, organizations must adopt continuous, automated testing methodologies akin to a boxer’s constant sparring.…
Read More 
Summary: Google has released a critical security update for Chrome to address the high-severity vulnerability CVE-2025-2783 affecting the Windows version of the browser. The update, made available on March 25, 2025, fixes an issue within the Mojo component that could lead to potential system compromises. Users are advised to manually check for updates and exercise caution while browsing to avoid falling victim to exploits.…
Read More 
Summary: Google has issued urgent patches for a high-severity vulnerability (CVE-2025-2783) affecting its Chrome browser on Windows, which has been exploited in attacks, particularly against Russian organizations. The flaw is linked to Mojo, Google’s IPC library, and poses risks such as sandbox escapes and privilege escalation.…
Read More 
Summary: Tiny Technologies has issued a security advisory regarding a critical remote code execution (RCE) vulnerability (CVE-2025-30091) in MoxieManager, a widely used file and media management solution. This flaw allows unauthenticated attackers to inject and execute arbitrary code, posing a significant risk to systems utilizing MoxieManager.…
Read More 
Summary: Google has addressed a high-severity zero-day vulnerability, CVE-2025-2783, in Chrome that was being exploited to escape the browser’s sandbox for espionage attacks targeting Russian organizations. The flaw allows attackers to deploy sophisticated malware through phishing campaigns. The patch is being rolled out for users globally, with further details on the attacks yet to be fully disclosed by Google.…
Read More 
Summary: Broadcom has issued critical security patches for VMware Tools for Windows to fix an authentication bypass vulnerability, tracked as CVE-2025-22230, rated 7.8 on the CVSS scale. The flaw affects versions 11.x.x and 12.x.x, allowing non-administrative users to perform high-privilege operations. Furthermore, CrushFTP has reported a separate unauthenticated HTTP(S) port access vulnerability in versions 10 and 11, still awaiting a CVE identifier.…
Read More 
Summary: Google has released urgent fixes for a high-severity vulnerability in Chrome for Windows, known as CVE-2025-2783, which has been actively exploited to target organizations in Russia. The flaw involves an incorrect handle in Mojo, allowing attackers to bypass browser protections through phishing emails. This marks the first actively exploited Chrome zero-day of the year, with attacks linked to a sophisticated APT campaign called Operation ForumTroll.…
Read More 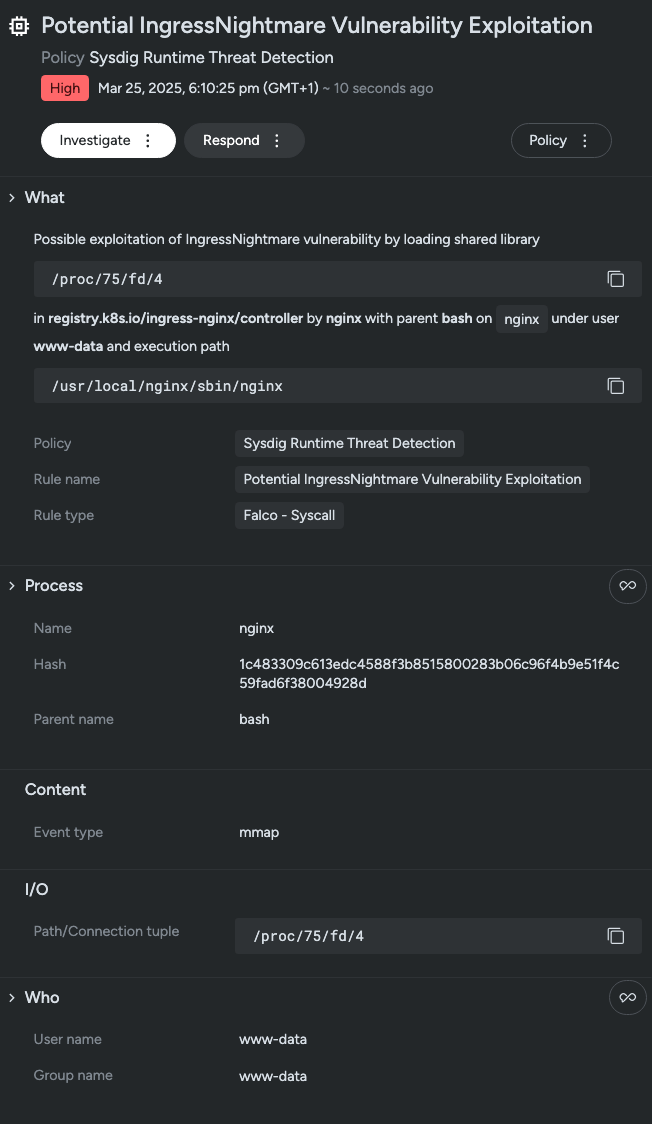
A set of critical vulnerabilities, including CVE-2025-1974, affecting the Ingress NGINX Controller in Kubernetes was disclosed, posing severe threats such as remote code execution. Organizations are encouraged to mitigate these risks by promptly upgrading to the latest versions of the NGINX Controller and securing admission webhook endpoints.…
Read More 
Kaspersky technologies identified a sophisticated wave of malware infections targeting various organizations through phishing emails leading to malicious links. A critical zero-day vulnerability in Google Chrome, identified as CVE-2025-2783, allowed attackers to bypass the browser’s sandbox. The malware campaign, dubbed Operation ForumTroll, aimed at espionage targeting media outlets and government entities in Russia.…
Read More 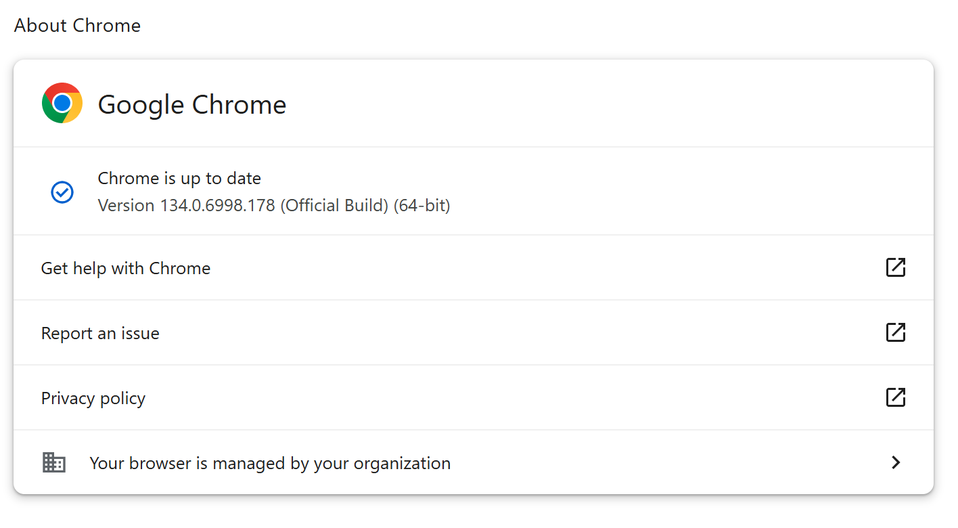
Summary: Kaspersky Labs has identified a complex cyber-espionage campaign named Operation ForumTroll, utilizing a new Google Chrome zero-day exploit (CVE-2025-2783) initiated through spear-phishing emails. The attack required no additional action from victims once they accessed the malicious link, with the exploit bypassing Chrome’s sandbox protections. This operation is believed to be conducted by a state-sponsored APT group targeting Russian media, educational institutions, and government organizations.…
Read More 
Summary: Google has released a patch for a critical vulnerability (CVE-2025-2783) in its Chrome browser that was exploited in a state-sponsored cyberespionage campaign. Kaspersky identified this vulnerability as part of a sophisticated attack targeting Russian organizations, utilizing drive-by downloads through phishing techniques. The patch was expedited following the discovery of a sandbox escape flaw that compromised Chrome’s security measures.…
Read More 
Summary: CrushFTP has issued a warning about an unauthenticated HTTP(S) port access vulnerability affecting versions 10 and 11, urging customers to patch their servers immediately. The flaw allows attackers to gain unauthorized access to exposed servers, with over 3,400 instances currently exposed online. As a temporary measure, users can enable the DMZ feature to protect their systems until they can apply updates.…
Read More