
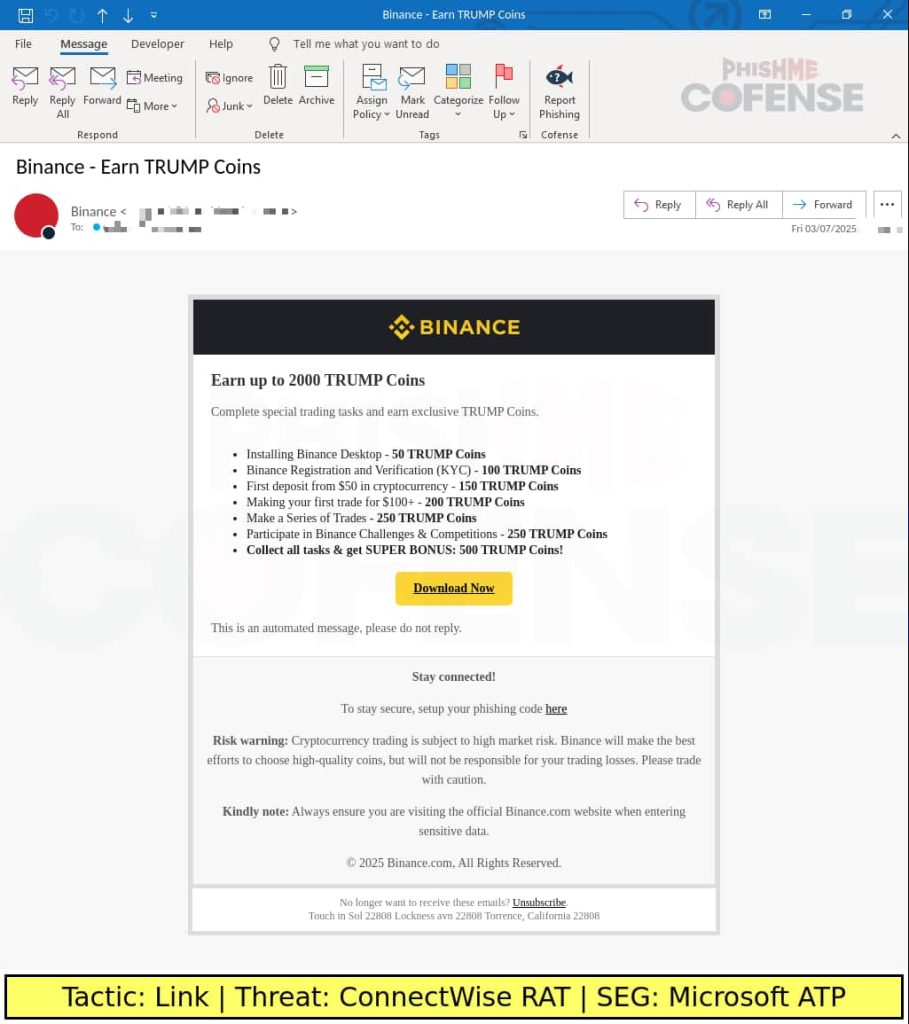
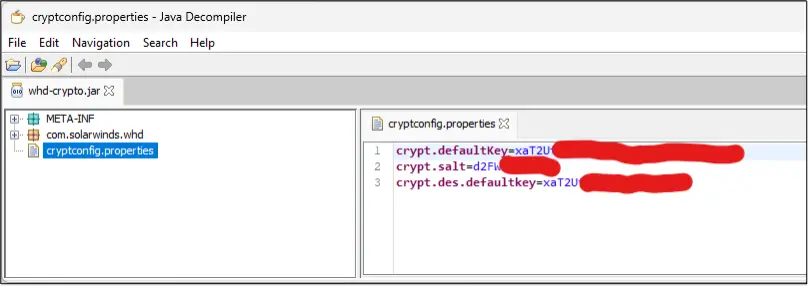
A recent security report highlights multiple cyber threats, including the discovery of six malicious npm packages linked to the Lazarus hacker group, which are designed to steal sensitive credentials and deploy malware. Additionally, a serious vulnerability in SolarWinds’ web help desk has been uncovered, allowing attackers to decrypt sensitive credentials.…
Read More 




 THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact
THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact





![[Law] Illegal crypto ATM operator jailed in the UK [Law] Illegal crypto ATM operator jailed in the UK](https://www.hendryadrian.com/tweet/image/cybersecuritynews.png)




