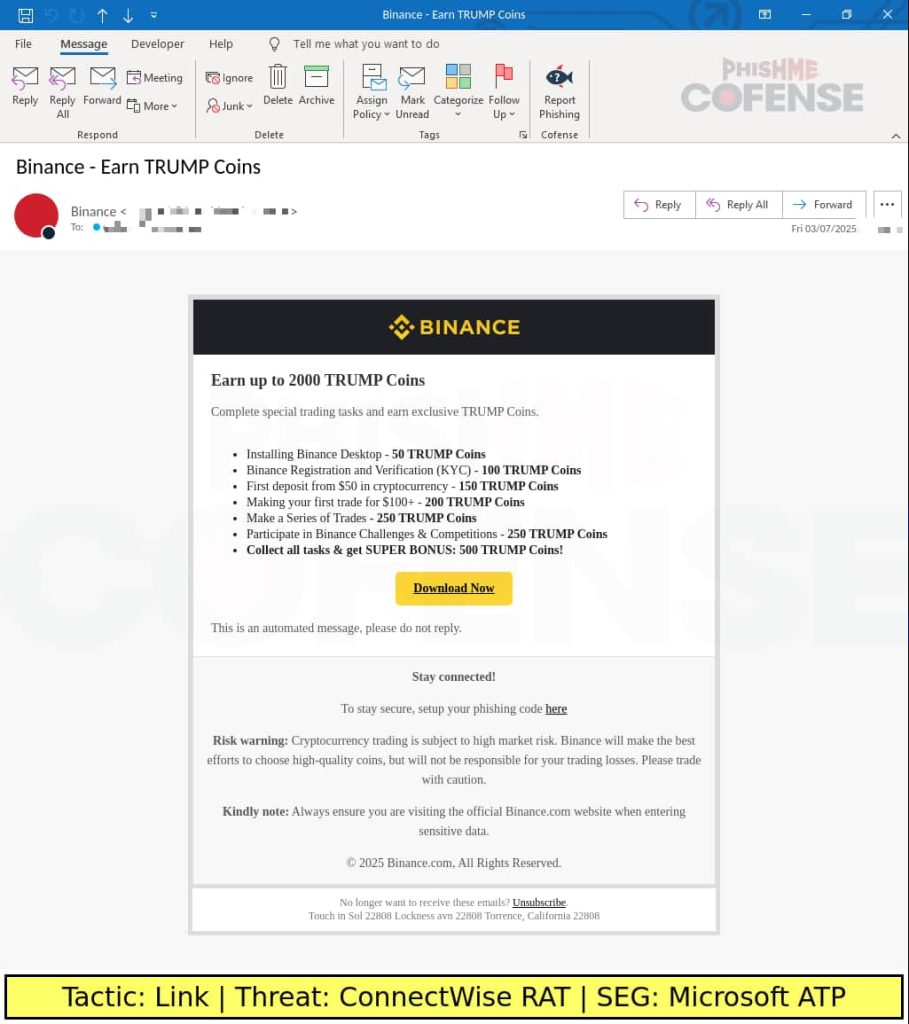
Summary: Microsoft has detected a new remote access trojan (RAT) named StilachiRAT that utilizes advanced techniques for avoiding detection and extracting sensitive information. Although its distribution is currently limited, Microsoft has released indicators of compromise and mitigation strategies to aid network defenders in identifying the threat.…
Read More 

 THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More