
Recent leaks from Black Basta’s internal chat logs highlight the gang’s strategy to leverage open source ecosystems, specifically npm and PyPI, to execute dependency confusion attacks. This research uncovers the threat posed by ransomware attacks and extortionware within these ecosystems, along with examples of historical attacks.…
Read More 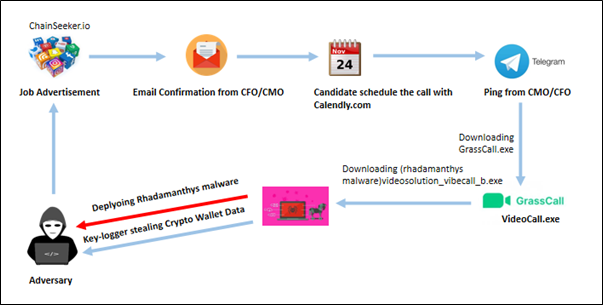










 THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More

