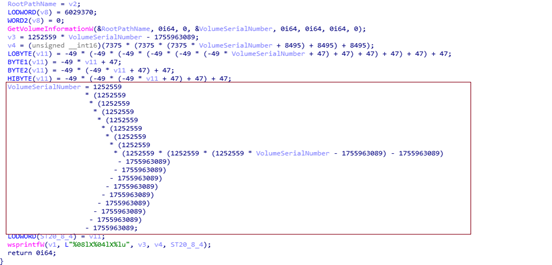
The Socket research team uncovered a malicious Python package named disgrasya on PyPI, designed to automate carding attacks against WooCommerce stores using CyberSource as a payment gateway. This openly malicious tool facilitates the testing of stolen credit card numbers, allowing low-skilled fraudsters to simulate transactions without raising fraud detection alarms.…
Read More 


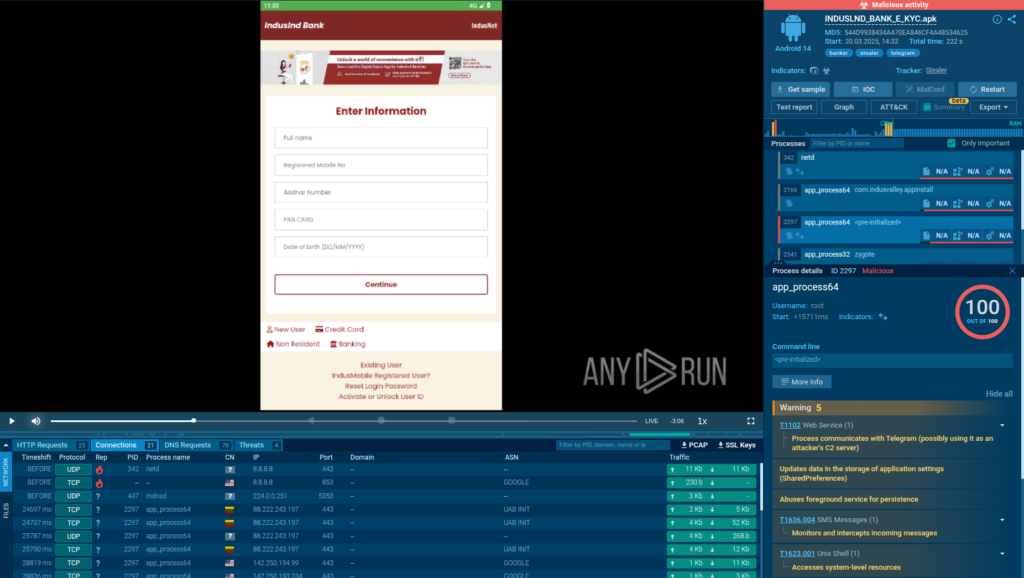


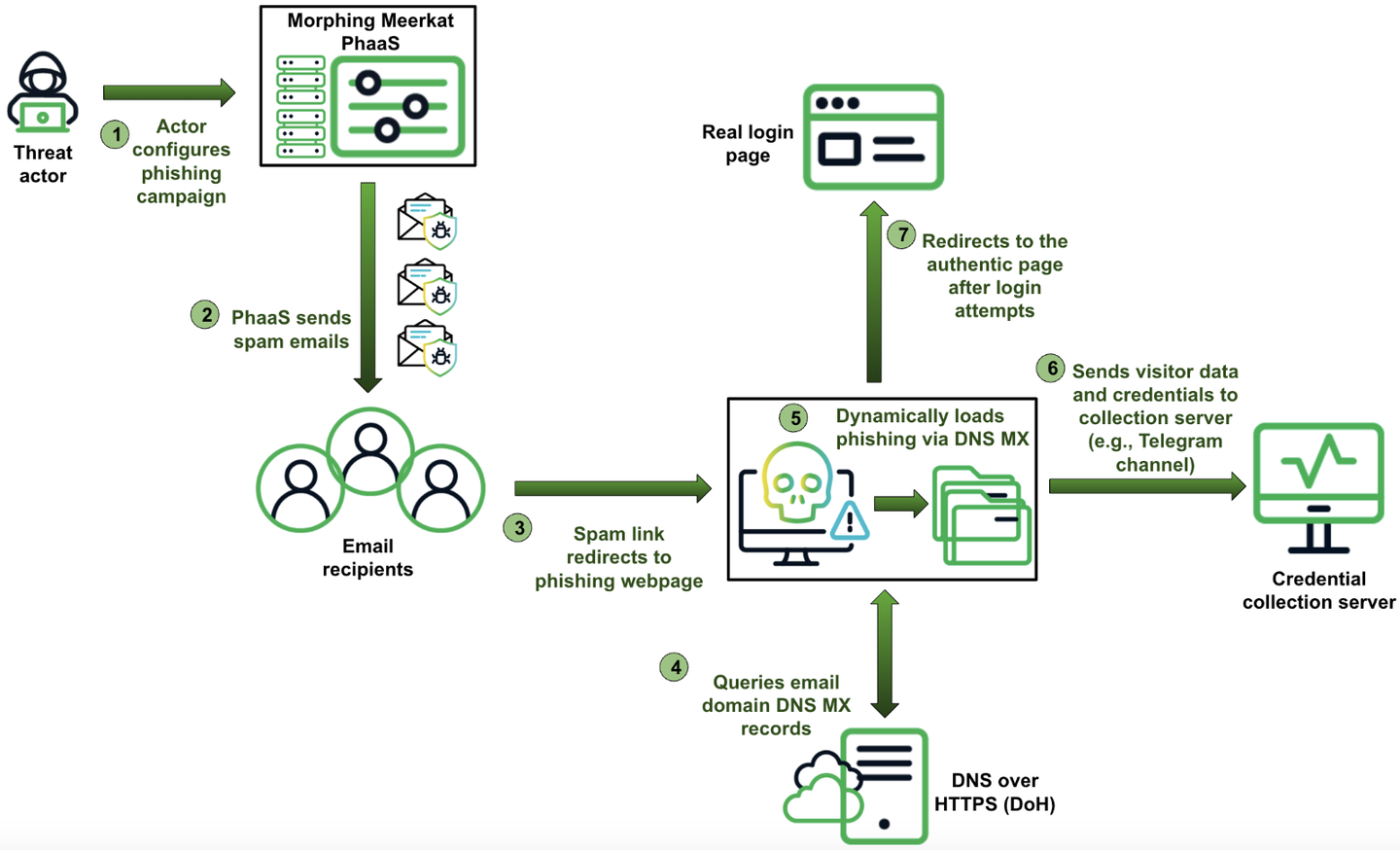




 Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More
Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More