The Cofense Phishing Defense Center has reported an increase in phishing emails masquerading as communications from US Customs and Border Protection regarding the Electronic System for Travel Authorization (ESTA). These emails create urgency and fear to trick users into providing personal information through a fraudulent website.…
Read More Tag: CREDENTIAL

Summary: A new phishing-as-a-service platform, Lucid, has emerged, targeting 169 entities across 88 countries through advanced smishing techniques. Utilizing Apple iMessage and RCS, Lucid bypasses traditional anti-phishing measures, enabling significant increases in phishing success rates. This sophisticated model threatens financial security as it focuses primarily on harvesting credit card information and personally identifiable information (PII).…
Read More 
The Democratic People’s Republic of Korea (DPRK) IT workers have expanded their operations internationally, particularly in Europe, targeting sectors such as defense and government. These workers utilize sophisticated tactics, including deception and extortion, to infiltrate companies. Their activities pose significant risks, including data theft and espionage, emphasizing the need for increased vigilance by affected organizations.…
Read More 
The report discusses Salvador Stealer, a new Android malware posing as a banking application to steal sensitive user data, such as banking credentials and personal information. The malware employs phishing techniques and has multiple methods for exfiltrating data, including SMS interception and real-time communication with a Command and Control (C2) server via Telegram.…
Read More 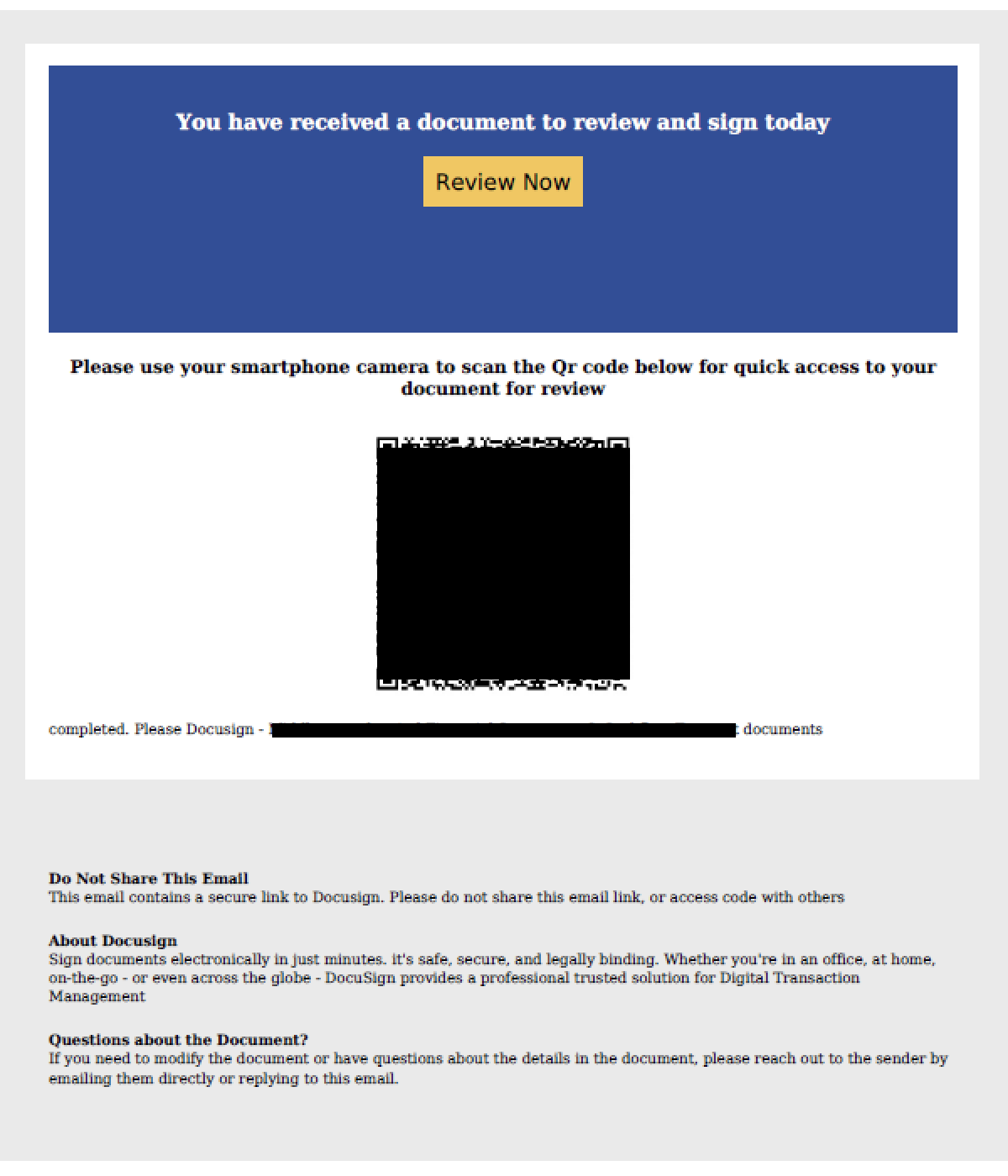
Researchers from Unit 42 have identified a rise in sophisticated phishing tactics that leverage QR codes and URL redirection to compromise user credentials. These methods obscure the true destination of phishing links, making it easier for attackers to deceive victims, particularly in sectors such as medical, automotive, education, energy, and finance.…
Read More 
Summary: Apple has released security updates for older and latest versions of its operating systems, backporting fixes for actively exploited zero-day vulnerabilities. These updates address critical flaws discovered by researchers, enhancing the security of iOS, iPadOS, macOS, and Safari. Users are urged to apply these updates promptly to protect against potential attacks.…
Read More 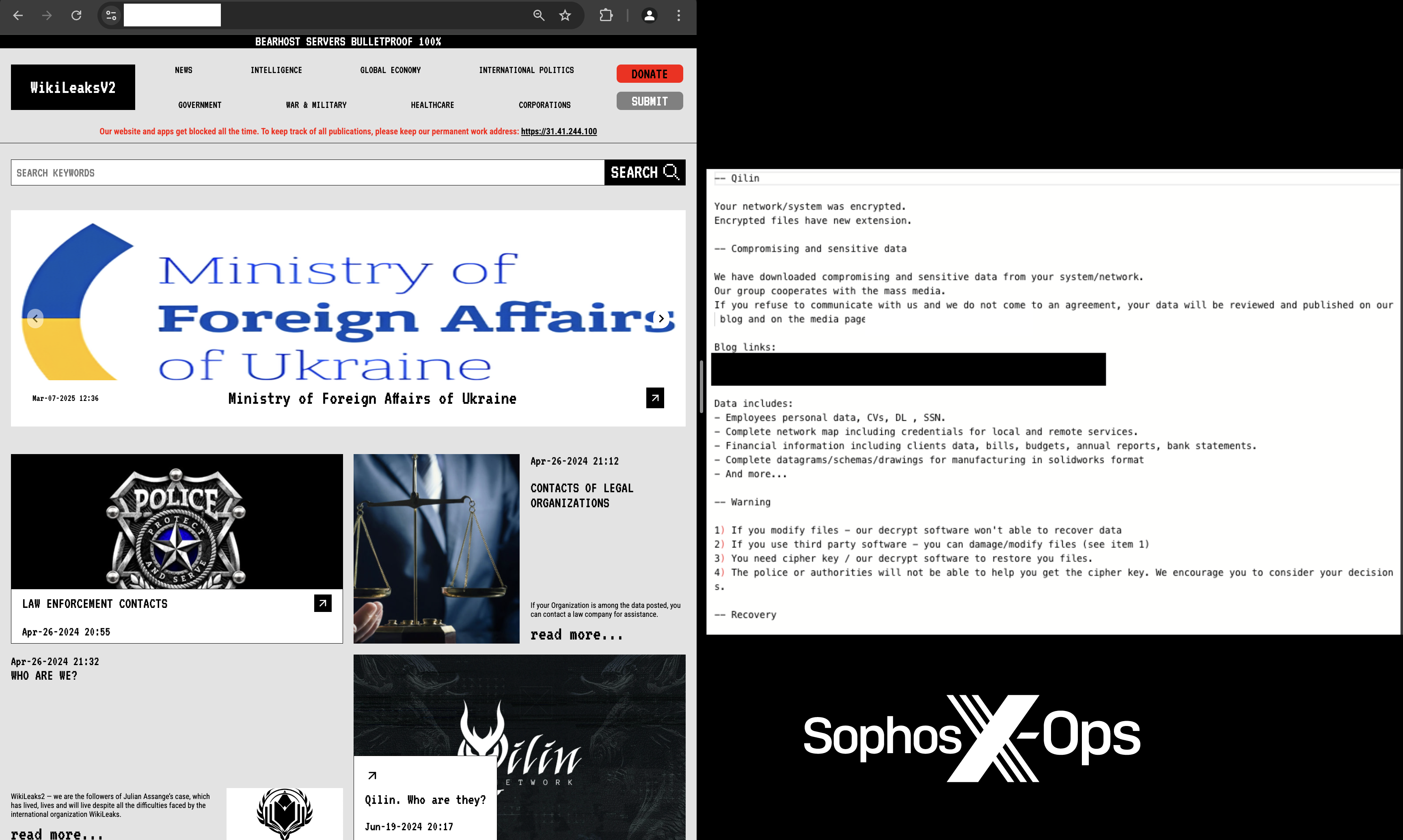
In late January 2025, an MSP administrator fell victim to a sophisticated phishing email that mimicked an authentication alert for a remote management tool, leading to a ransomware attack by Qilin actors. This incident emphasizes the vulnerabilities faced by MSPs and their clients to phishing campaigns.…
Read More 
GreenSpot APT phishing campaigns target 163.com users, attempting to steal credentials through fake login pages without embedding malicious attachments. While currently not direct threats, future modifications could introduce risks. Affected: 163.com, users of GreenSpot phishing campaigns
Read More Keypoints :
GreenSpot APT is conducting phishing campaigns. Fake login pages prompt users to enter credentials twice.…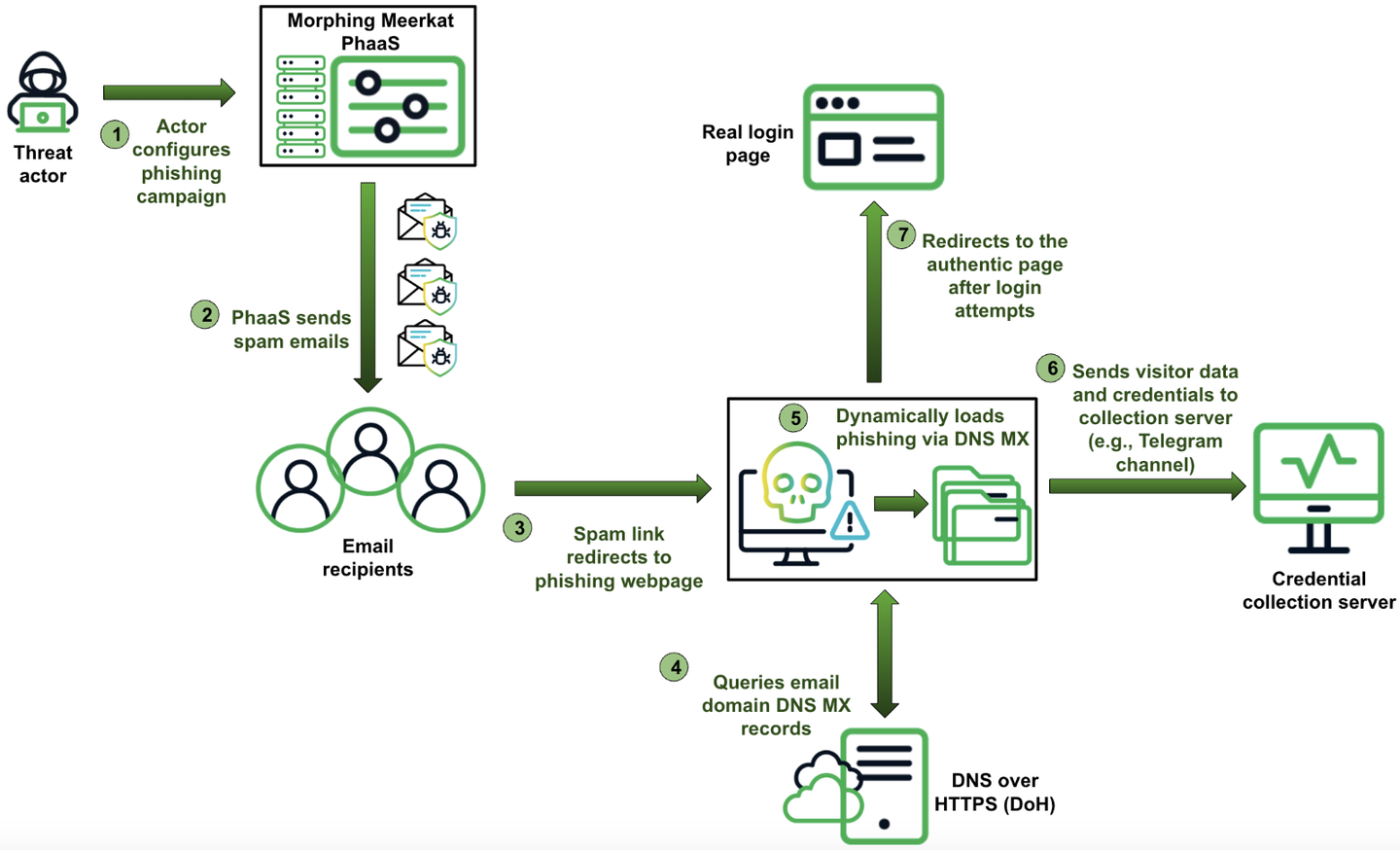
Summary: A recent report by Infoblox Threat Intelligence details a sophisticated phishing operation named Morphing Meerkat, which utilizes DNS techniques to create tailored phishing content for victims. The operation dynamically serves fake login pages mimicking over 100 brands, employing advanced methods to evade detection and enhance effectiveness.…
Read More 
Summary: This report analyzes a Python-based Remote Access Trojan (RAT) that utilizes Discord’s API for malicious activities, including command execution and credential theft. It provides a detailed examination of the RAT’s code and behavior, revealing its capabilities for remote machine control and espionage. Recommendations for combating this cyber threat emphasize the importance of enhanced security measures and user education.…
Read More 
Summary: Hackers are increasingly leveraging WordPress’s mu-plugins directory to execute malicious code undetected on every page load. This method, which was first identified in February 2025, enables various harmful activities, including credential theft and redirection to malware-laden sites. Security analysts recommend that WordPress site administrators enhance their security measures to safeguard against these threats.…
Read More 
Summary: A hacker known as ‘GHNA’ has leaked around 270,000 customer records from Samsung Germany’s ticketing system, sourced via compromised credentials from Spectos GmbH. The data breach stems from an incident in 2021 and includes sensitive personal and transaction information. Experts warn that the leaked data could facilitate various cyber threats, including phishing and account takeovers.…
Read More 
Summary: This week’s cybersecurity insights highlight vulnerabilities in widely used systems like Chrome and Kubernetes, as well as emerging threats from phishing-as-a-service operations. The coverage includes data leaks, ransomware trends, and the importance of vigilance against common oversights that can lead to security breaches. Additionally, the impact of recent legal cases and developments in AI-driven cyber threats are discussed.…
Read More 
This week’s threat intelligence report reveals an analysis of multiple cyber threat reports. Key highlights include espionage tactics from APT groups, sophisticated malware deployments, and various Indicators of Compromise (IoCs) detected across platforms. The ongoing evolution of cyber threats emphasizes adaptive techniques utilized by attackers to infiltrate critical sectors.…
Read More 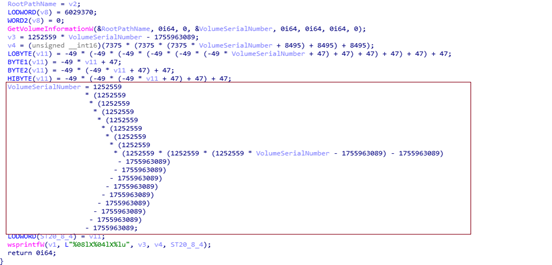
SvcStealer 2025 is a sophisticated information-stealing malware delivered through spear phishing emails. It captures sensitive data from victims, including credentials and cryptocurrency wallet information, and sends it to a command and control (C2) server. With a focus on evading detection, it deletes traces of its activities and can potentially download additional malware.…
Read More 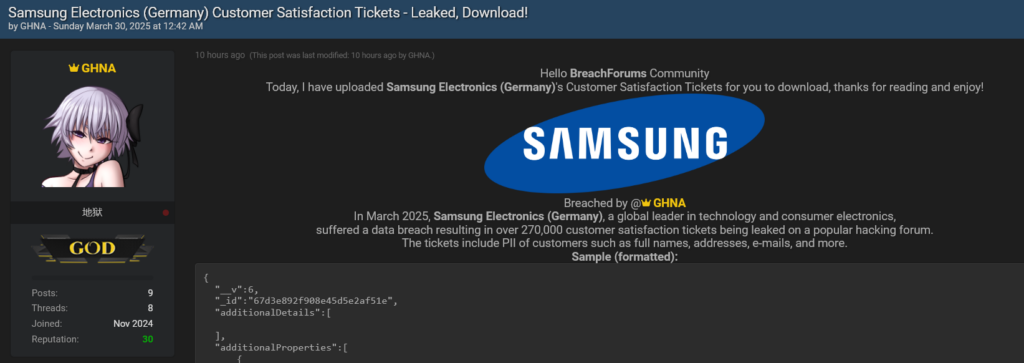
This article discusses a massive data breach impacting Samsung Germany, where a hacker known as “GHNA” leaked approximately 270,000 customer tickets due to credentials stolen by infostealer malware back in 2021. The breach highlights the dangers of unmonitored and unrotated credentials, leading to potential exploitation and privacy violations for thousands of customers.…
Read More 
Summary: The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has disclosed the presence of a new malware, RESURGE, targeting vulnerabilities in Ivanti Connect Secure appliances. This malware exploits a recently patched security flaw (CVE-2025-0282) and has capabilities enhancing its evasion and operational effectiveness. It is linked to espionage activities potentially conducted by state-sponsored threat actors.…
Read More 
Summary: Cybersecurity researchers have identified a new Android banking malware named Crocodilus that specifically targets users in Spain and Turkey. This sophisticated malware employs advanced techniques for device takeover and credential theft, masquerading as a legitimate application. It showcases the growing complexity and danger of modern mobile threats, especially within the banking sector.…
Read More 
The transportation and logistics industry is increasingly targeted by cybercriminals as they exploit vulnerabilities to disrupt operations and steal sensitive data. Major incidents include ransomware attacks affecting ports and airports, along with data breaches that raise severe concerns about data security within the sector. Affected: transportation and logistics industry, public infrastructure, cybersecurity sector
Read More Keypoints :
Transportation and logistics sector is a major target for cybercriminals due to valuable data.…
Summary: The Cybersecurity and Infrastructure Security Agency (CISA) has issued a Malware Analysis Report on a new malware variant called RESURGE, which has sophisticated persistence and manipulation capabilities, particularly linked to a known vulnerability in Ivanti products. The report highlights detailed mitigation measures in response to RESURGE’s exploitation of the CVE-2025-0282 vulnerability.…
Read More  Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More
Weekly Recap: Chrome 0-Day, IngressNightmare, Solar Bugs, DNS Tactics, and More