Victim: GARANIMALS.COM
Country : US
Actor: clop
Source: http://santat7kpllt6iyvqbr7q4amdv6dzrh6paatvyrzl7ry3zm72zigf4ad.onion//companys-part4/garan-manufacturing
Discovered: 2025-03-14 09:43:53.910956
Published: 2025-03-14 09:42:43.851768
Description :Garanimals.com is a well-known children’s clothing brand based in the US.
The brand promotes mix-and-match clothing to encourage kids to dress themselves.
Offers a vast collection from newborn apparel to toddler and school-age clothing.…
Read More Tag: COLLECTION

The Lookout Threat Lab has uncovered a new Android surveillance tool named KoSpy, linked to the North Korean APT group ScarCruft. This spyware targets Korean and English-speaking users, utilizing fake utility applications to infect devices. It has been distributed via Google Play Store and Firebase Firestore, now secured by Google.…
Read More 
Organizations often fail to investigate after patching zero-day vulnerabilities, leading to undetected compromises. A proactive approach involving compromise assessments is critical to uncover potential breaches. Affected: VMware ESXi, cybersecurity sector
Read More Keypoints :
Patching alone does not confirm if systems have been breached. Recent zero-day vulnerabilities in VMware ESXi (CVE-2025-22224, CVE-2025-22225, CVE-2025-22226) have been exploited.…
The article discusses the activities of an Indonesian hacktivist group called INDOHAXSEC, which has been conducting cyberattacks, including DDoS and ransomware attacks, motivated largely by political beliefs, particularly targeting entities associated with Israel and Malaysia. They utilize custom tools and social media for coordination and propaganda.…
Read More 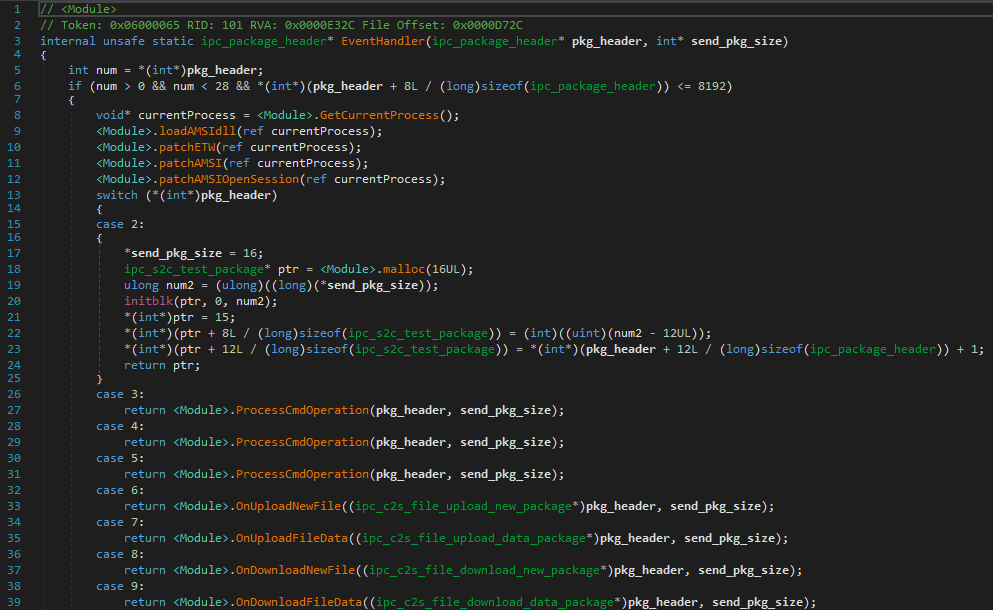
This article discusses three unique malware samples discovered recently: a C++/CLI IIS backdoor, a bootkit that installs a GRUB 2 bootloader, and a post-exploitation framework known as ProjectGeass. Each sample demonstrates unconventional techniques and complexities, highlighting the evolving threat landscape. Affected: IIS, Windows, system environments
Read More Keypoints :
Three unique malware samples discovered exhibiting novel characteristics.…
Summary: This week’s cybersecurity news roundup highlights significant stories including a cryptocurrency heist linked to a LastPass hack, mandatory reporting of cyberattacks in Switzerland, and vulnerabilities discovered in various systems. The roundup also discusses the rise of phishing threats and the arrest of a cryptocurrency exchange co-founder.…
Read More 
This report highlights recent cyber threats targeting the financial sector, specifically focusing on malware and phishing incidents, credit card information leaks, database breaches, and ransomware attacks. Notable cases include the sale of Indian credit card details on forums, a significant database leak from Union**** bank, and ransomware infections affecting fintech companies.…
Read More 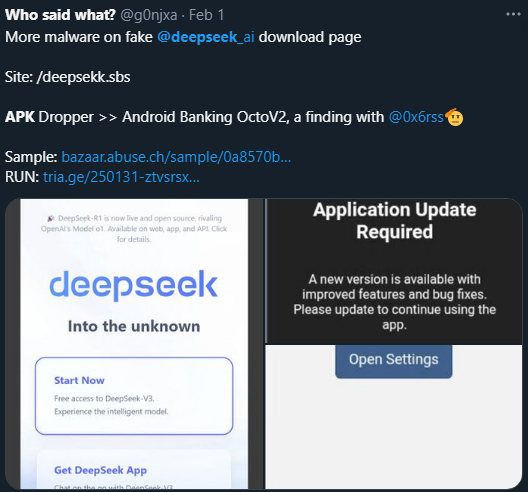
This article discusses the emergence of Deepseek, an AI-based application, and the subsequent rise in malware targeting its users through deceptive phishing tactics. It highlights how malicious actors create counterfeit websites and applications that mimic Deepseek, deceiving users into downloading malware. Affected: mobile users, cybersecurity sector
Read More Keypoints :
Deepseek is an advanced AI developed in China, with its first chatbot application due for release in January 2025.…Victim: Intelligence Bureau of the Joint Staff Department of the Central Military Commission China
Country : CN
Actor: babuk2
Source: http:/bxwu33iefqfc3rxigynn3ghvq4gdw3gxgxna5m4aa3o4vscdeeqhiqad.onion/blog/39b1b6646b2110e79ac532e169720824c3d842d02ce0c61e95658835ac24d084/
Discovered: 2025-03-14 07:56:32.049126
Published: 2025-03-14 07:55:27.110559
Description :Intelligence Bureau operates under the Joint Staff Department of China’s Central Military Commission.
Responsible for gathering and analyzing military intelligence.…
Read More 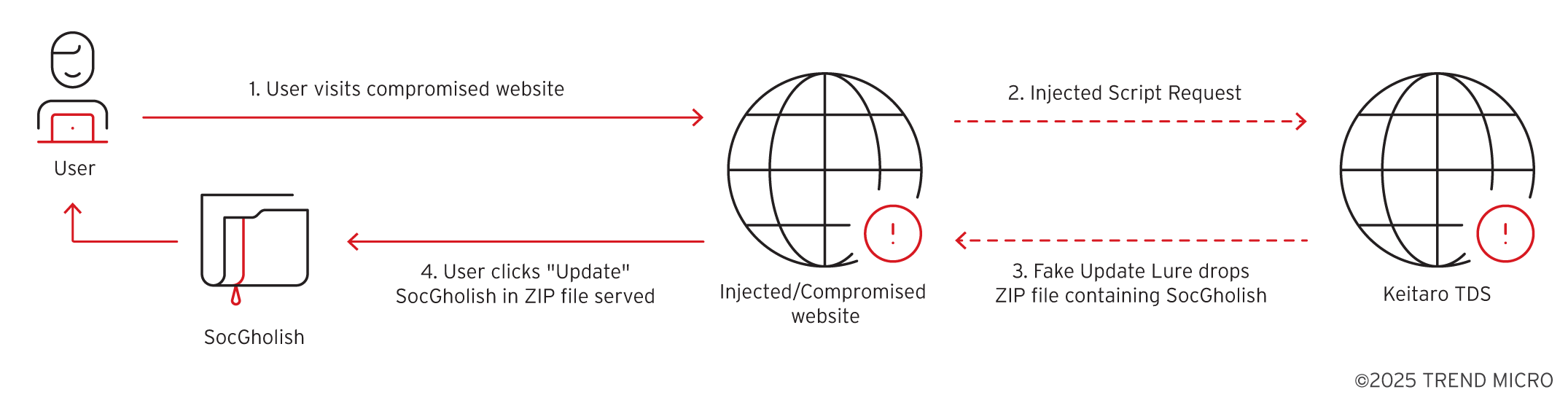
Trend Research’s analysis of SocGholish’s MaaS framework highlights its critical role in delivering RansomHub ransomware via compromised websites. Utilizing highly obfuscated JavaScript loaders, SocGholish evades detection and successfully executes malicious tasks. Notably, the framework propels initial access for ransomware attacks, mainly affecting government entities in the United States.…
Read More 
In early December 2024, Microsoft Threat Intelligence detected a large-scale malvertising campaign that affected nearly one million devices globally. The attack exploited illegal streaming websites and employed a multi-stage payload delivery system using platforms like GitHub, Discord, and Dropbox to deliver malware aimed at information theft.…
Read More 
Summary: A European commissioner alleviated concerns regarding the future of the Transatlantic Data Privacy Framework (TDPF), emphasizing continued commitment to the agreement that facilitates cross-border data flows between Europe and the U.S. Following significant political changes, there were worries about the board overseeing data privacy, but the commissioner expressed optimism about ongoing cooperation from both sides.…
Read More 
The finance industry is facing an increasing number of cyberattacks, with significant recent incidents exposing vast amounts of sensitive data. Notable breaches have involved major financial institutions and data theft, highlighting vulnerabilities and the need for robust cybersecurity measures. The financial sector must adapt to evolving threats, including ransomware attacks and Dark Web exploitation, to safeguard personal and financial information.…
Read More 
Summary: In the UK, there are calls from politicians and civil society groups for a secret court hearing regarding the government’s encryption demands on Apple to be made public. Experts warn that the government’s attempts to access encrypted communications should be more transparent, especially after Apple’s recent decision to disable end-to-end encryption for British users.…
Read More 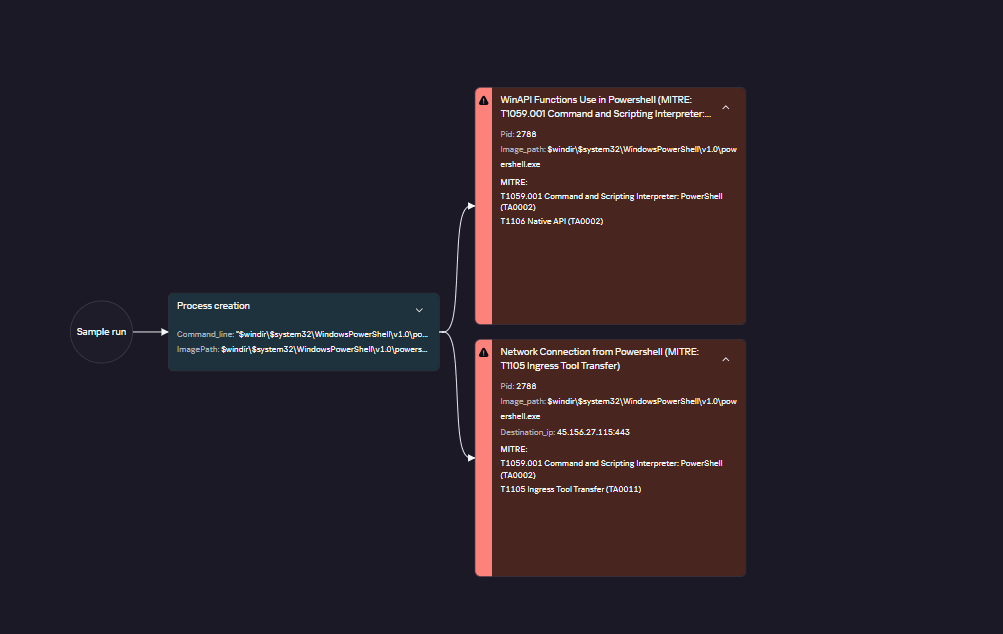
In September 2024, Russian companies faced a series of coordinated attacks linked to two hacktivist groups, Head Mare and Twelve. The investigation revealed a blend of new and familiar tactics, techniques, and procedures (TTPs) employed in these attacks, with indications of collaboration and tool-sharing between the groups.…
Read More
The recent VMware zero-day vulnerability (CVE-2023–20867) has made numerous organizations—including cloud providers and financial institutions—vulnerable to serious attacks such as data theft and ransomware. This incident highlights the importance of cybersecurity frameworks like the Cyber Kill Chain and Diamond Model for developing effective defenses against increasingly sophisticated threats.…
Read More 
This article discusses a series of data breaches involving large language models (LLMs) that occurred between January and February 2025. These incidents highlighted vulnerabilities in the deployment of LLMs across enterprises, resulting in extensive data leaks including API keys, user credentials, and sensitive information. The incidents serve as a wake-up call regarding “AI-driven risks” and underscore the need for improved security practices.…
Read More 
This report discusses the statistics, trends, and methodologies of distributing Infostealer malware, particularly focusing on techniques such as SEO-Poisoning and disguising malware as illegal programs. Threat actors have adapted their strategies to utilize various distribution platforms, which has been analyzed by AhnLab Security Intelligence Center. The report outlines notable trends in the distribution of specific variants and highlights the importance of recognizing these threats.…
Read More 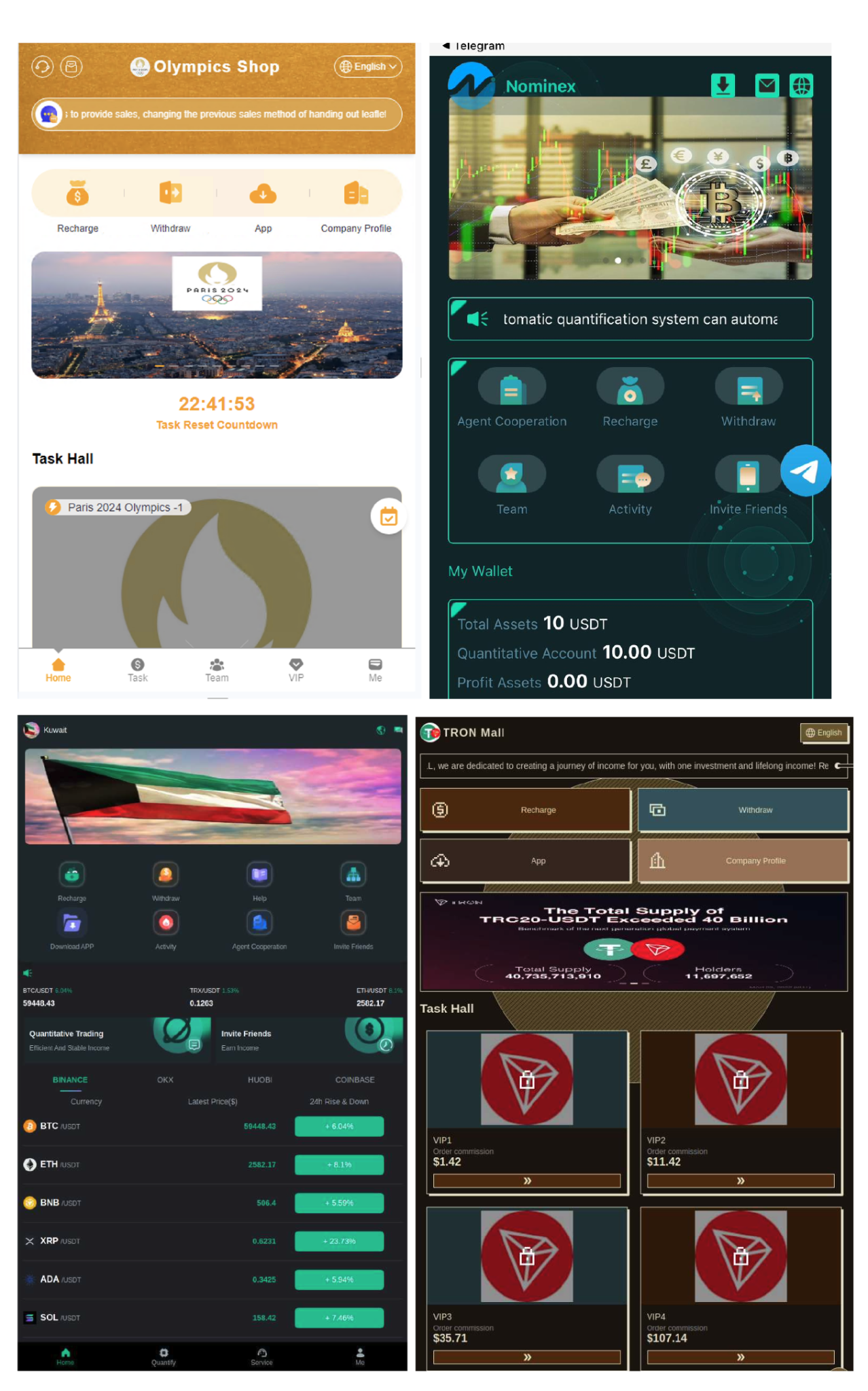
Unit 42 researchers have uncovered a widespread campaign distributing fraudulent cryptocurrency investment platforms through websites and mobile applications. The operation employs deceptive practices, impersonating well-known brands to lure victims, particularly in East Africa and Asia. By leveraging multi-level affiliate programs and unrealistic promises of high returns, the campaign closely resembles Ponzi schemes.…
Read More 
Summary: A North Korean APT group, ScarCruft, has been distributing a surveillance tool known as KoSpy via Google Play, targeting primarily Korean and English-speaking users. The spyware, disguised as utility applications, enables extensive data collection from infected devices, including SMS, call logs, and location data. Lookout, a cybersecurity firm, has identified multiple instances of this malware and noted its active use since March 2022.…
Read More