Keypoints :
Wi-Fi security is critical for protecting against cyber threats.…
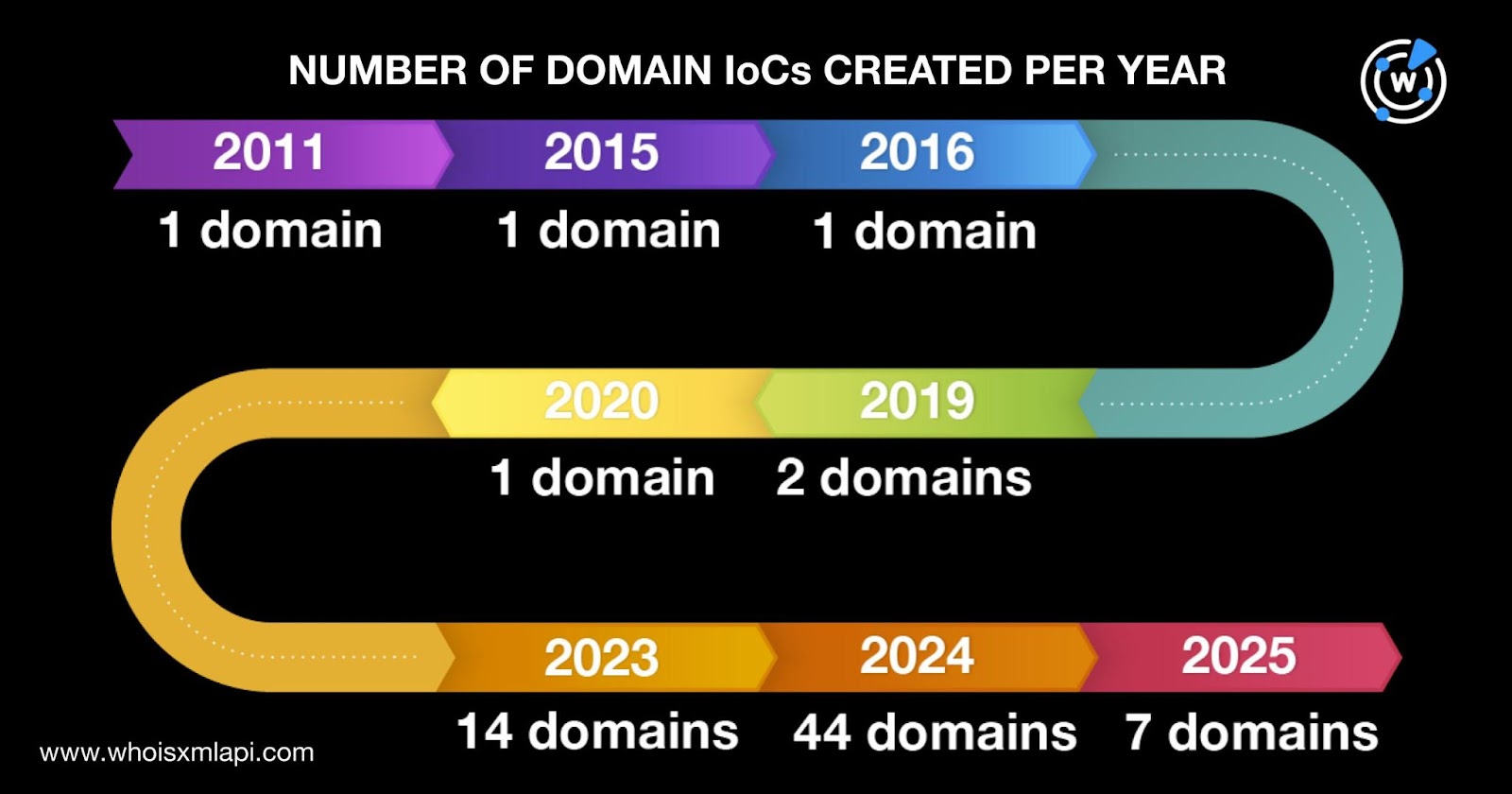
This article provides a comprehensive guide on hacking and securing Wi-Fi networks using Aircrack-ng, detailing practical attack techniques and encryption vulnerabilities, as well as prevention strategies. The focus is on educating users about Wi-Fi security to help them protect their networks from potential attacks. Affected: Wi-Fi networks, cybersecurity sector
Read More