Keypoints :
PE32 Ransomware is gaining traction online as a recent ransomware strain.…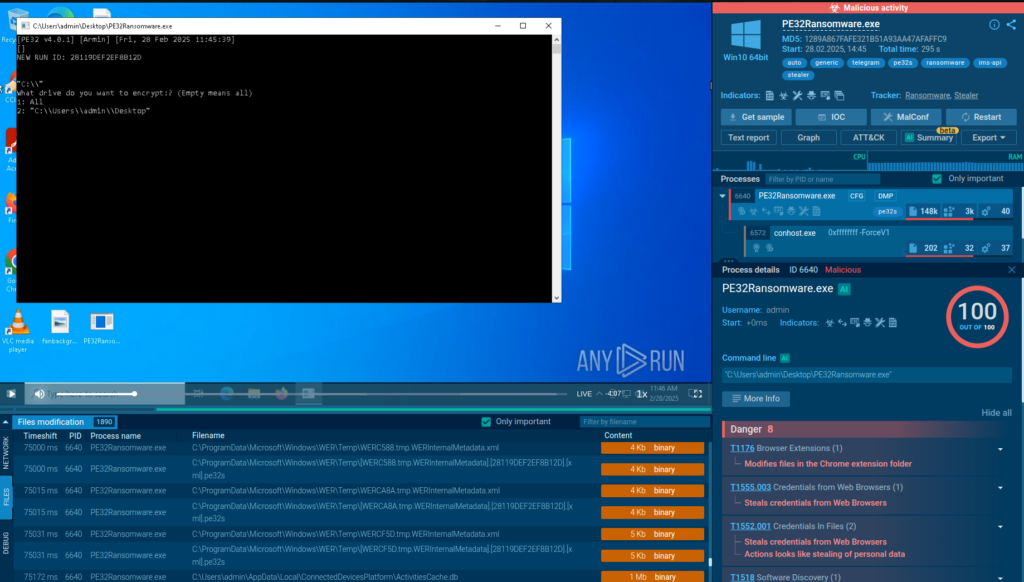
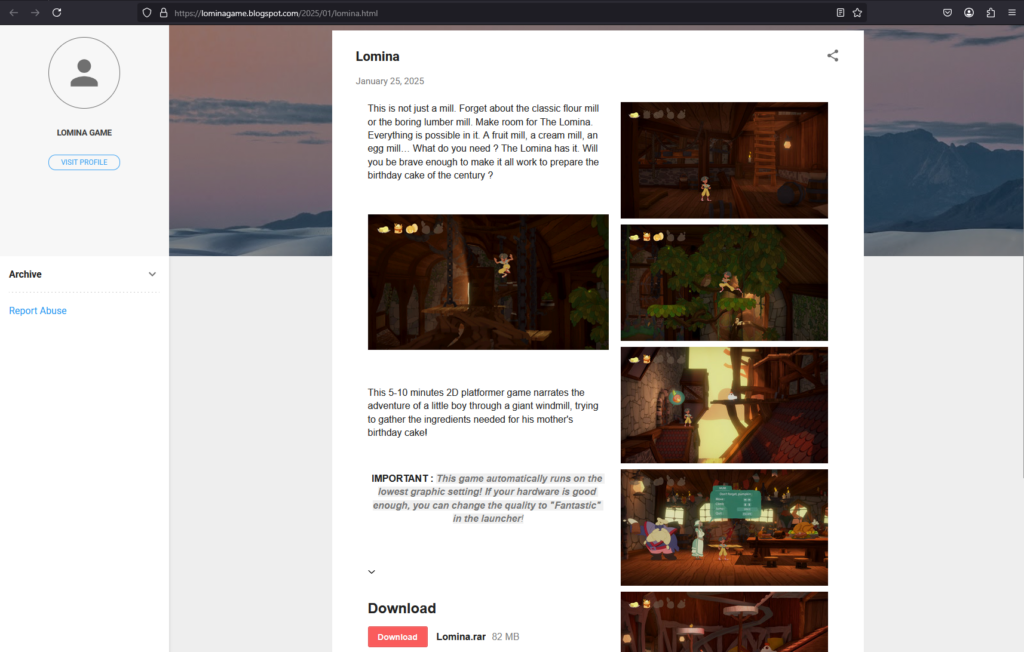
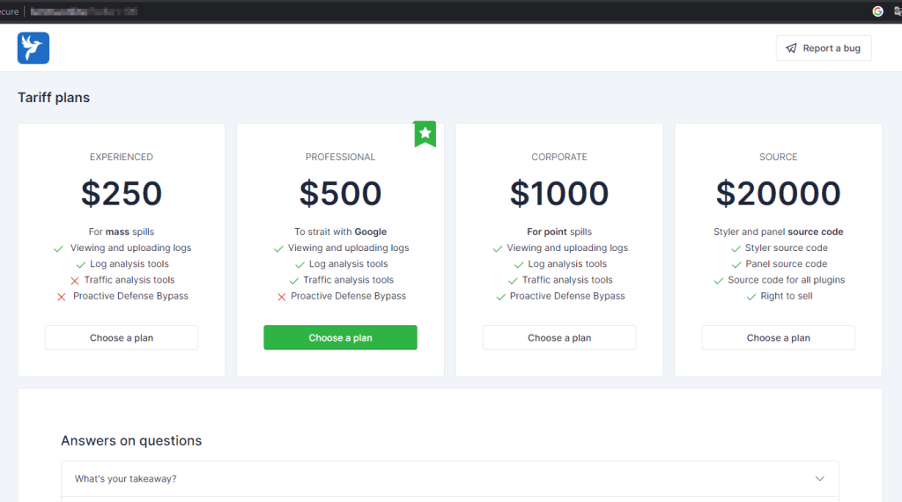
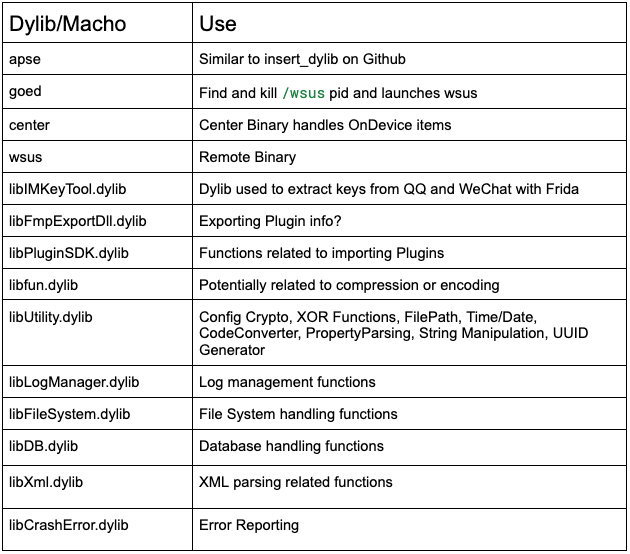
PE32 Ransomware is a newly emerging threat exploiting Telegram for its operations, utilizing a chaotic and noisy encryption method. Its simple design poses significant risks to users and organizations, especially with its dual ransom model that pressures victims. Affected: individuals, organizations, cybersecurity teams
Read More