Keypoints :
Akira ransomware has been active since March 2023.…
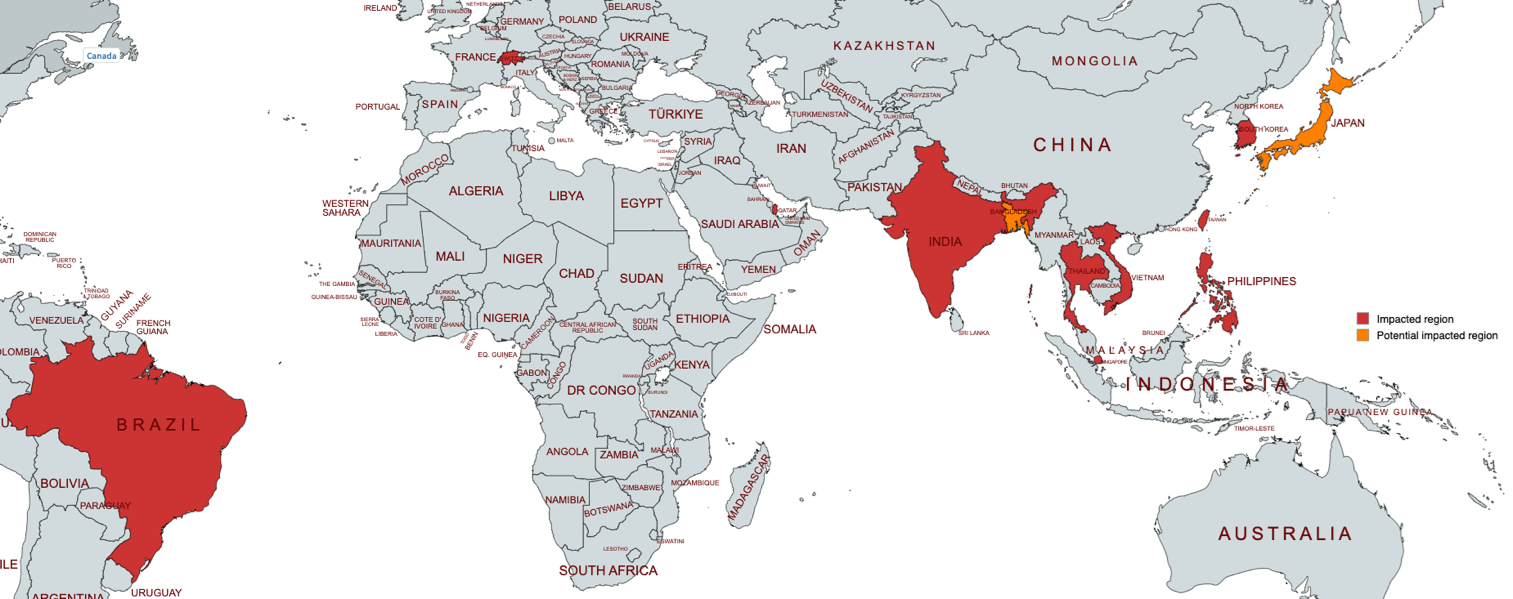
Akira is a relatively new ransomware actor active since March 2023, known for infiltrating organizations, encrypting files, and stealing sensitive information for negotiation purposes. The ransomware attacks have significantly impacted numerous sectors, as demonstrated by statistics from 2024. Affected: organizations, information technology, cybersecurity
Read More