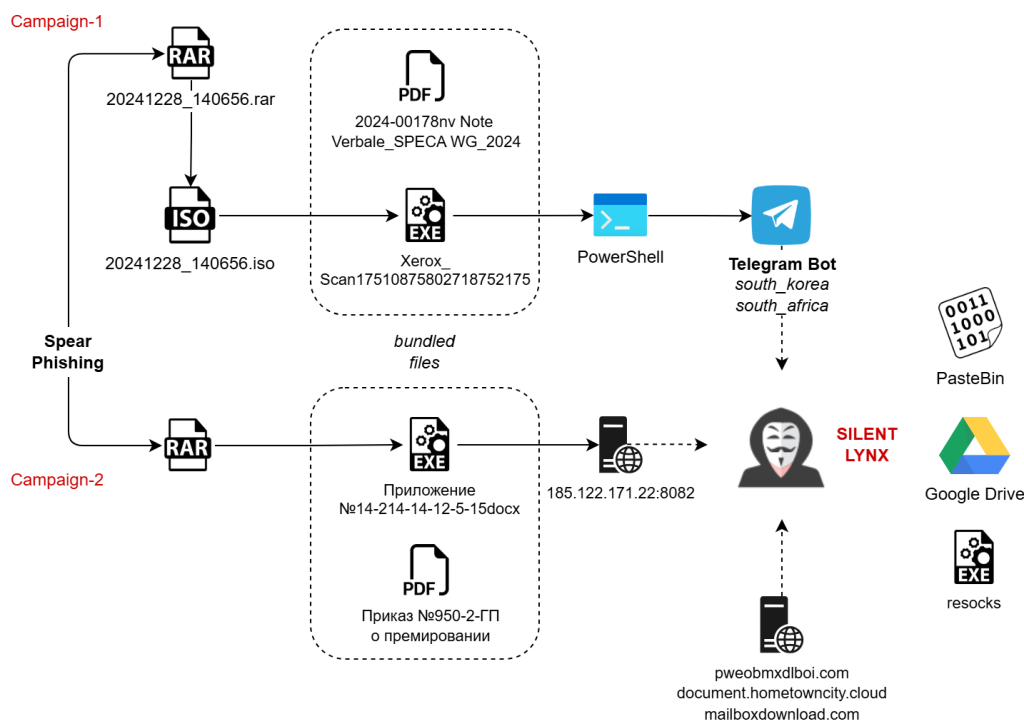
Summary: A recent agreement between Iran and Russia aims to enhance military, security, and technological cooperation, particularly in cybersecurity and internet regulation. The deal, signed by leaders of both nations, seeks to formalize their close ties and establish stronger control over the digital space. Both countries, known for their restrictive internet policies, plan to collaborate on countering cybercrime and managing national internet segments.…
Read More