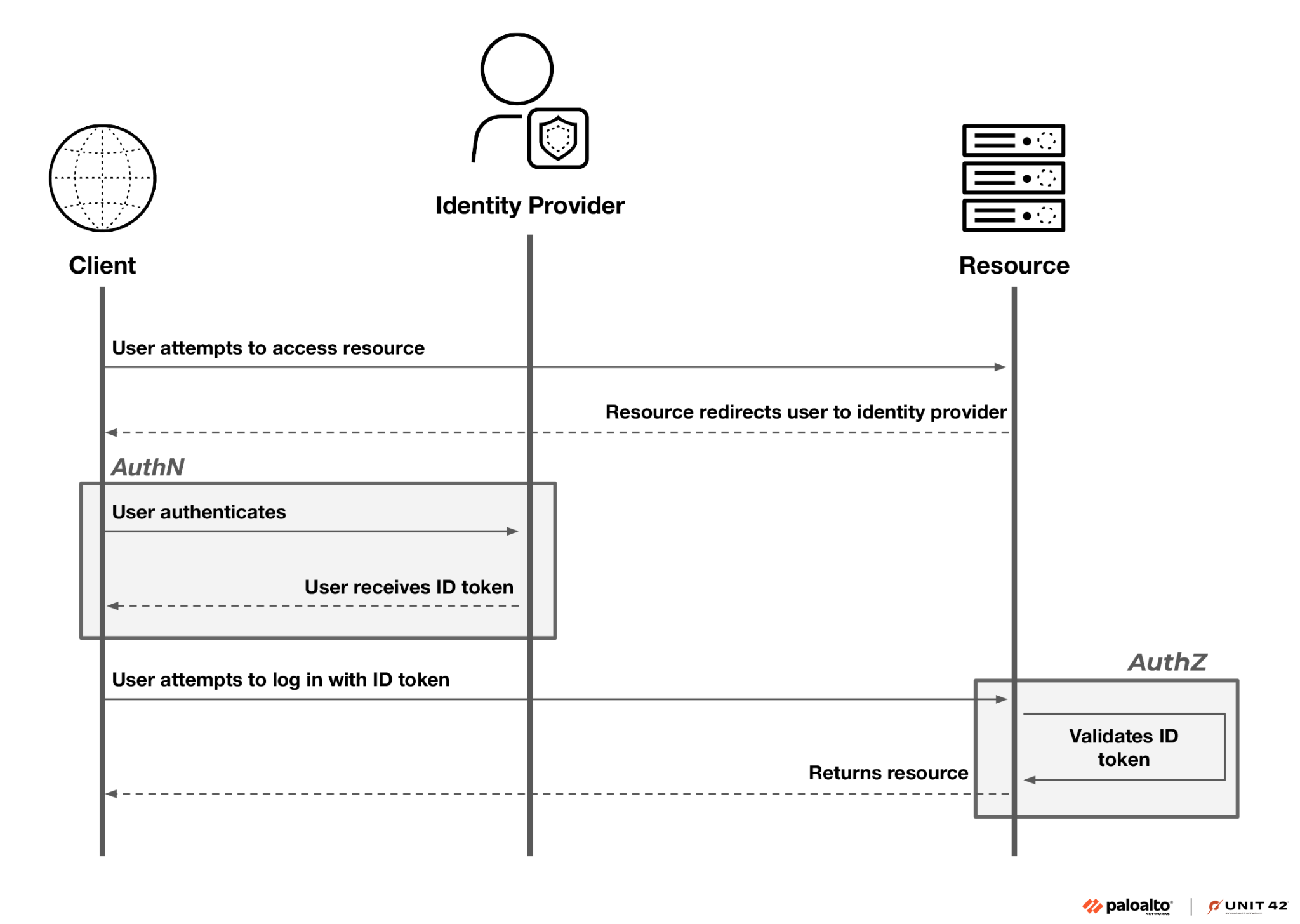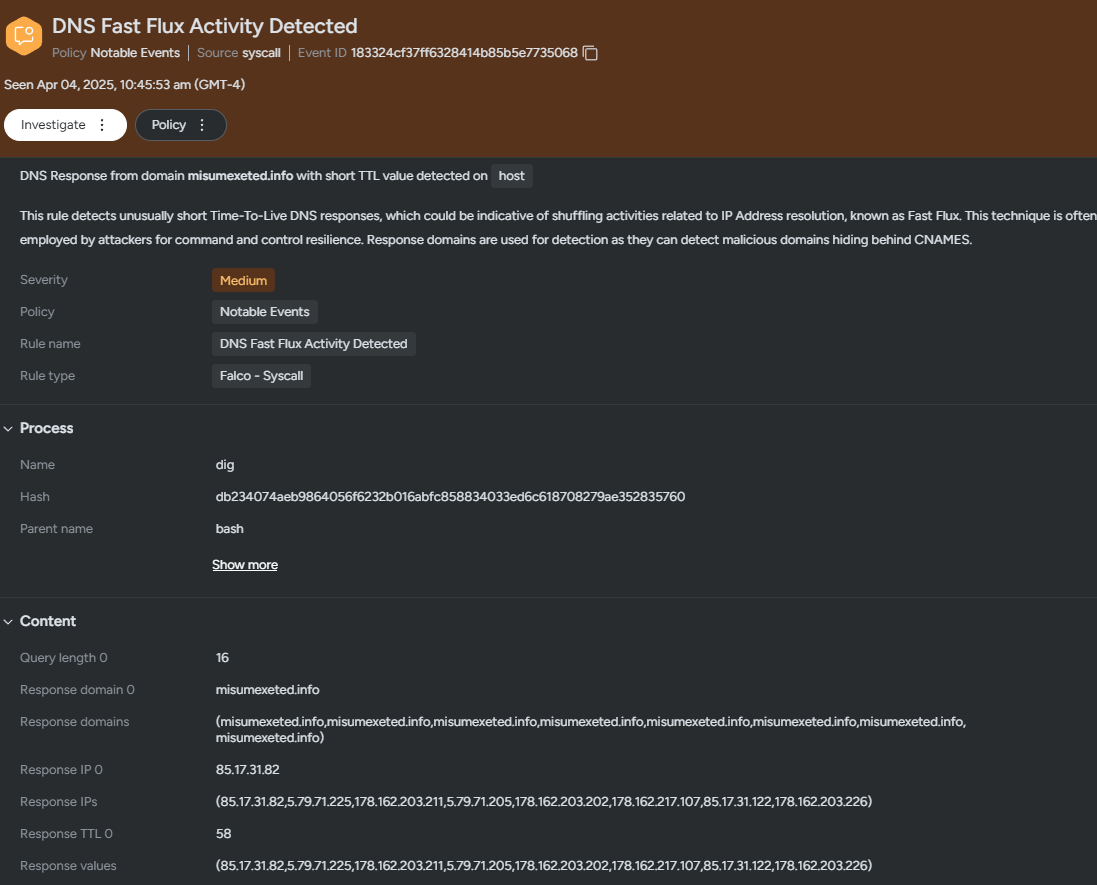
The article discusses Fast Flux, a technique used by attackers to obfuscate their infrastructure by rapidly changing the IP addresses associated with a domain name. It explains the implications of this attack method, outlines how Sysdig Secure detects it, and emphasizes the need for a layered defense strategy using tools like Sysdig.…
Read More