Summary: Organizations are increasingly facing cyber threats that outpace traditional security measures, leading to the evolution of Security Operations Centers (SOCs) through three distinct phases: SOC 1.0, SOC 2.0, and SOC 3.0. The latest iteration, SOC 3.0, integrates AI to automate alert triage and detection, significantly enhancing operational efficiency while allowing security professionals to focus more on strategic initiatives.…
Read More Tag: CISO

Summary: Dispersive Stealth Networking has announced the appointment of Greg Akers as Advisor and Chief Information Security Officer (CISO). Akers brings extensive experience from Cisco, where he was the Senior Vice President & CTO of Advanced Security Research & Government. His previous roles also include positions at Procter & Gamble and Fechheimer Brothers.…
Read More 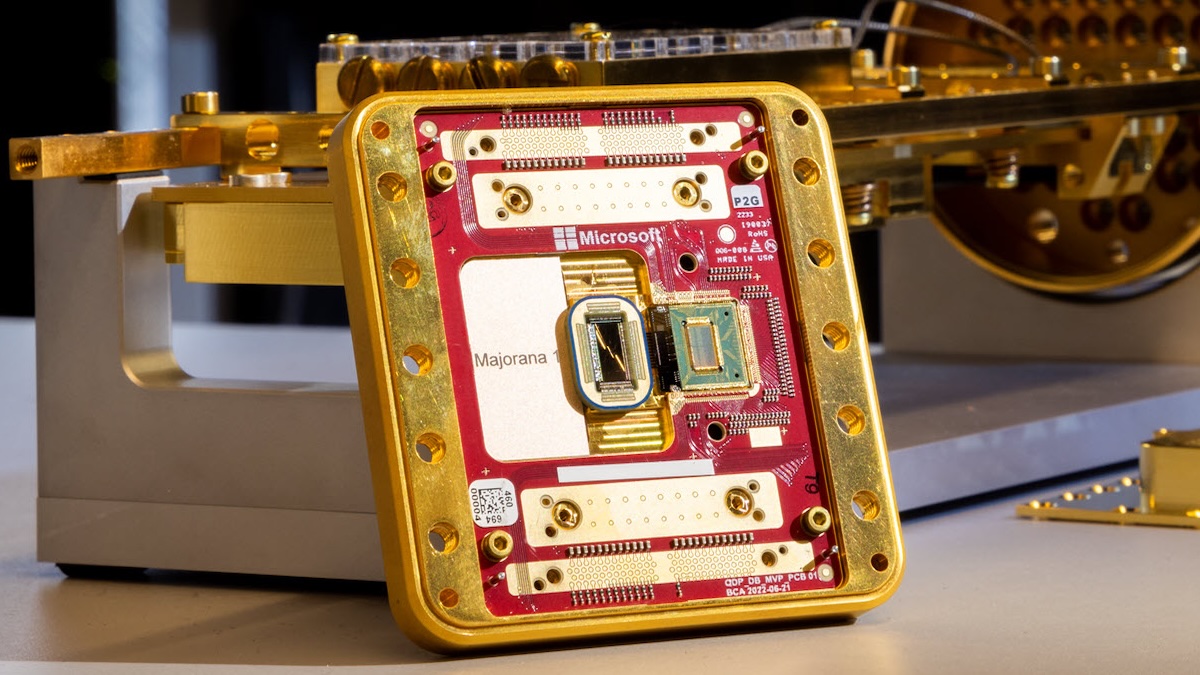
Summary: Microsoft has unveiled the Majorana 1, a groundbreaking quantum processing unit featuring topological qubits designed to greatly enhance stability and scalability in quantum computing. This development promises potential advancements in various fields, from medicine to AI, while posing significant cybersecurity challenges. However, uncertainty remains about the timeline for achieving practical quantum decryption capabilities.…
Read More 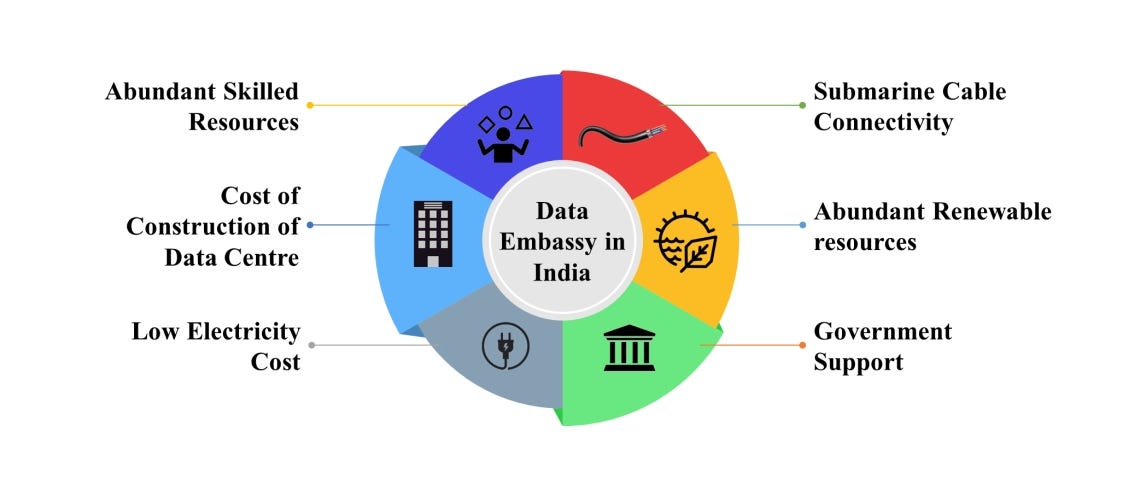
Summary: A growing number of smaller nations are utilizing “data embassies” to store citizens’ information abroad while retaining legal control, thereby ensuring data protection against various threats. These initiatives require strong security measures and complex legal frameworks to maintain data sovereignty and manage operations effectively. While promising, the data embassy concept faces challenges such as high costs, regional geopolitics, and evolving legal obstacles.…
Read More 
Summary: Boards of directors are increasingly challenged with managing cyber-risks within operational technology (OT) environments, particularly in high-risk sectors. The article discusses the crucial need for specialized leadership and strategic approaches to improve OT cybersecurity governance and resilience. It emphasizes the importance of collaboration between IT and OT, as well as the development of comprehensive cybersecurity programs tailored to the unique threats faced by OT systems.…
Read More 
Summary: The evolving roles of Chief Information Security Officers (CISOs) at major firms like Deloitte and AuditBoard are discussed, highlighting their unique non-technical backgrounds and perspectives on cybersecurity. The conversation emphasizes the importance of blending technical skills with business acumen, teamwork, and mentorship in addressing compliance and emerging threats.…
Read More 
Summary: Deepwatch has acquired Dassana, a startup specializing in security intelligence solutions, to enhance its cyber resilience platform with AI-powered risk and threat exposure management. The integration will provide real-time insights into security postures, improving tools for automation, compliance reporting, and proactive security management. This acquisition aligns with Deepwatch’s mission to democratize AI capabilities for organizations of all sizes, enabling better protection against cyber threats.…
Read More
Summary: Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) can capitalize on the rising need for cybersecurity by offering virtual Chief Information Security Officer (vCISO) services. However, they face challenges in structuring, pricing, and selling these services effectively, which is addressed in the Ultimate Guide to Structuring and Selling vCISO Services.…
Read More 
Summary: MirrorTab, a San Francisco startup, has raised .5 million in seed funding to enhance its technology that neutralizes web-based attacks at the browser level. This funding round highlights growing interest in “browser isolation” technologies designed to protect users from online threats. The company’s innovative approach sanitizes browser sessions before they reach users’ devices, effectively minimizing potential attack surfaces.…
Read More 
Summary: The evolving nature of cyber threats necessitates a proactive defense strategy like Continuous Threat Exposure Management (CTEM), which builds on existing security frameworks. A new guide details the effectiveness of CTEM compared to traditional Vulnerability Management and Attack Surface Management approaches through real-world scenarios. The report emphasizes CTEM’s ability to continuously monitor and respond to threats while aligning security efforts with business priorities.…
Read More _ronstik_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)
Summary: The founders of Credible Security, an independent security consultancy, highlight the advantages of diverse backgrounds in cybersecurity, emphasizing that leadership qualities like empathy and communication matter more than technical skills. Their varied experiences enhance their approach to developing trust and security strategies for B2B cloud service providers.…
Read More 
Summary: The US, alongside Australia and the UK, has sanctioned Zservers, a Russia-based bulletproof hosting service, for facilitating LockBit ransomware attacks. This action is part of ongoing international efforts to dismantle the LockBit cybercriminal organization and disrupt its operations. The sanctions aim to impede ransomware activities by targeting the infrastructure that enables such attacks.…
Read More 
Summary: Chief Information Security Officers (CISOs) are increasingly engaged with AI teams, but they lack resources to define their roles effectively. The CLEAR framework provides security leaders with a strategic approach to support AI adoption through asset inventory, proactive learning, policy enforcement, application of use cases, and leveraging existing frameworks.…
Read More _Brain_light_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)
Summary: The cybersecurity industry is facing a critical crisis due to the burnout of security analysts and leadership. With an alarming number of professionals contemplating leaving the field, the focus must shift from merely hiring new talent to supporting and empowering existing personnel. To sustain effective cybersecurity defense, organizations must prioritize the welfare of their defenders and harness their expertise alongside technological advancements.…
Read More 
Summary: SolarWinds has announced its acquisition by Turn/River Capital for .4 billion, leading to its status as a privately held company. This comes in the aftermath of the significant cyberattack in 2020, which still influences the cybersecurity landscape. The Securities and Exchange Commission has taken action against SolarWinds for its failures related to the attack, indicating ongoing scrutiny of cybersecurity practices in the industry.…
Read More _Agata_Gładykowska_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)
Summary: This commentary emphasizes the importance of understanding probabilities over predictions in the cybersecurity landscape. It advocates for Bayesian probability models to assess risks and improve resilience against cyber threats. By leveraging insurance data and advanced risk assessments, organizations can enhance their security strategies and better withstand cyberattacks.…
Read More 
Summary: David Kennedy, an accomplished hacker and CEO of TrustedSec, uniquely embodies the hacker ethos, shaped by his ADHD and military experiences. His unconventional learning style emphasizes hands-on problem-solving over traditional methods, leading him to a successful career in cybersecurity. Despite his challenging beginnings, Kennedy maintains a strong ethical compass and believes in the importance of creativity and fun in his work.…
Read More 
Summary: AWS S3 bucket namesquatting is a significant security risk stemming from predictable naming structures that can be exploited by malicious actors. This article outlines the potential consequences of such vulnerabilities, including unauthorized access and traffic redirection, while emphasizing mitigation strategies. Varonis offers solutions to prevent and remediate S3 bucket namesquatting and related security issues in the AWS environment.…
Read More 
Summary: SecurityWeek will organize the second session of the CISO Forum 2025 Outlook webinar on February 5th, focusing on incident response and threat intelligence. The panelists will discuss strategies for aligning cyber resilience plans with business objectives amid evolving cyber threats. Attendees can expect insights on various risks including ransomware, nation-state attacks, and identity-related threats.…
Read More 
Summary: SecurityWeek’s Cyber Insights 2025 highlights the evolving role of the Chief Information Security Officer (CISO) in a complex landscape marked by increasing regulatory demands, the advent of artificial intelligence, and rising social engineering threats. As cyber threats become more sophisticated, the CISO must blend technical expertise with business acumen, improving their communication with both technical teams and executive leadership.…
Read More