Summary: The video discusses a double AI interview segment on Business Security Weekly featuring Matt Mueller and Summer Fowler. Matt, the Field CISO at Tines, shares insights on balancing AI opportunities with risks, while Summer, the CISO at Torque Robotics, addresses the challenges of AI in business alongside its implications for cybersecurity.…
Read More Tag: CISO

Summary: The PCI DSS 4.0.1 introduces substantial updates to enhance cybersecurity in the payment industry while remaining user-centric in its design. The standard emphasizes “what” needs to be achieved rather than “how,” fostering a collaborative industry response instead of bureaucratically driven regulations. Recent critiques highlight its strengths and weaknesses, particularly regarding multifactor authentication and compliance with broader regulations like GDPR and the AI Act.…
Read More Summary: The video discusses the lack of clarity surrounding the roles and responsibilities of the Chief Executive Security Officer (CESO) within organizations, highlighting the confusion and risk this creates. It emphasizes the importance of defining accountability and consultation processes for the CESO to prevent liability issues and enhance support.…
Read More 
Summary: The article highlights the dangers of relying on vanity metrics in cybersecurity, which may distort a true understanding of organizational risk and security effectiveness. It argues for the adoption of meaningful metrics that focus on actual risk reduction rather than merely reporting activity. These meaningful metrics are necessary for organizations to improve their security posture and make informed decisions regarding threat exposure and vulnerability management.…
Read More 
Summary: The viral trend of AI-generated art, particularly Ghibli-style portraits, raises significant privacy concerns as users unknowingly share sensitive biometric data. While the transformation of selfies into whimsical anime characters captivates audiences, it also poses risks of data misuse, identity theft, and exploitation by AI algorithms.…
Read More 
Summary: The content discusses the barriers to AI adoption in enterprises, particularly the security, legal, and compliance challenges that stall innovation. It explores the importance of effective AI governance and collaboration among security, compliance, and technical teams to facilitate AI implementation. Practical strategies and insights from industry leaders are provided to bridge the gap between AI innovation and governance challenges.…
Read More 
Summary: A breach at Oracle Health has compromised patient data from multiple US healthcare organizations after a threat actor accessed legacy servers. Oracle Health, formerly Cerner, confirmed the incident but has faced criticism for its lack of transparency and communication. Healthcare organizations are advised to determine their own notification responsibilities regarding potential HIPAA violations due to the breach.…
Read More 
Summary: Colin Ahern, New York state’s first chief cyber officer, reflects on his journey from military intelligence to leading cybersecurity efforts. During his tenure, he has focused on protecting government systems from escalating cyber threats, particularly ransomware. Ahern discusses the collaboration needed between state and local governments, as well as the essential role of education in promoting cybersecurity awareness.…
Read More 
Summary: AI security startup SplxAI has successfully raised million in a seed funding round, increasing its total funding to million. The company aims to enhance its security platform that protects AI agents from various vulnerabilities and attacks. SplxAI also announced the appointment of Sandy Dunn as its new CISO and will utilize the funds to accelerate product development and adoption.…
Read More 
Summary: H&R Block has appointed Phillip Miller as its new Vice President and Chief Information Security Officer (CISO), effective March 31. Miller brings extensive cybersecurity experience, having previously founded Qurple and held senior security roles at NetApp and Brooks Brothers, as well as serving as a Principal Security Advisor at AWS.…
Read More 
Summary: The integration of Generative AI (GenAI) in enterprise environments has surged, paving the way for significant security worries, particularly concerning the sharing of sensitive data. A recent report emphasizes the implications of “shadow AI,” where employees utilize personal accounts for GenAI applications, heightening the risk of data exfiltration.…
Read More 
Summary: The VanHelsing ransomware-as-a-service (RaaS) operation emerged on March 7, 2025, quickly claiming multiple victims through a user-friendly platform that supports a variety of operating systems. The scheme employs double extortion tactics and allows affiliates to profit significantly while only prohibiting attacks on the Commonwealth of Independent States (CIS).…
Read More Summary: The video discusses the importance of maintaining a natural and engaging flow during conversations, especially while presenting. It emphasizes that slowing down can enhance the conversation, making it more interactive and responsive to the audience’s engagement.
Read More Keypoints:
Slowing down can enhance the flow of conversation.…Summary: The video discusses the challenges and advancements in cybersecurity, particularly focusing on the evolving threat landscape and the role of Chief Information Security Officers (CISOs). It emphasizes the importance of creating a tailored security strategy, managing cybersecurity investments wisely, and building strong relationships within organizations.…
Read More 
Summary: Join a live webinar that explores the comprehensive process of ransomware attacks, highlighting the tactics and technologies used by hackers. Led by Joseph Carson, an expert in enterprise security, the session includes a live demonstration of an attack from breach to ransom demand. Attendees will gain valuable insights on identifying vulnerabilities and defending against such threats.…
Read More 
This article provides a thorough analysis of the security vulnerabilities associated with low-code/no-code (LCNC) platforms, exposing architectural flaws and real-world breaches. It outlines case studies involving significant breaches such as Microsoft Power Apps and Airtable, highlighting the negligence of platform providers. A call to action for stronger security practices and vendor accountability concludes the report.…
Read More 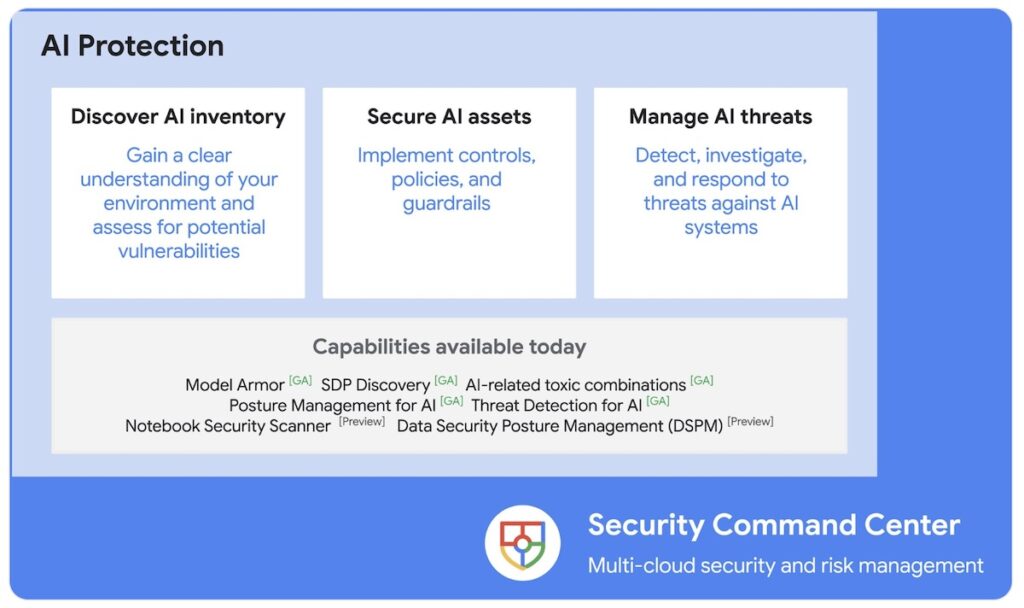
Summary: Google Cloud has introduced AI Protection, a solution aimed at managing risks associated with generative AI through three key capabilities: discovering AI assets, securing them, and managing threats. The integration with Google’s Security Command Center (SCC) allows for comprehensive visibility and management of AI risks in relation to overall cloud security.…
Read More 
Summary: The rising demand for robust cybersecurity is prompting an increase in virtual Chief Information Security Officer (vCISO) services, especially among small and medium-sized businesses (SMBs) that often lack in-house expertise. The vCISO Academy has been established to provide training and resources for Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) to confidently develop their vCISO offerings.…
Read More 
Summary: Mimic, a ransomware defense startup, has raised million in a Series A funding round, bringing its total capital to million. The funding, led by Google Ventures and Menlo Ventures, will support the company’s advanced ransomware detection platform and new capabilities like the Signal Generator. The esteemed appointment of Mandiant founder Kevin Mandia to Mimic’s board highlights the company’s potential in the cybersecurity market.…
Read More _Eyebyte_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)
Summary: The article highlights the growing threat of AI data poisoning, where hackers manipulate training data to compromise AI systems, potentially causing significant harm, especially in sensitive sectors like healthcare. The text argues for heightened awareness and the need for organizations to adapt their cybersecurity strategies accordingly.…
Read More 