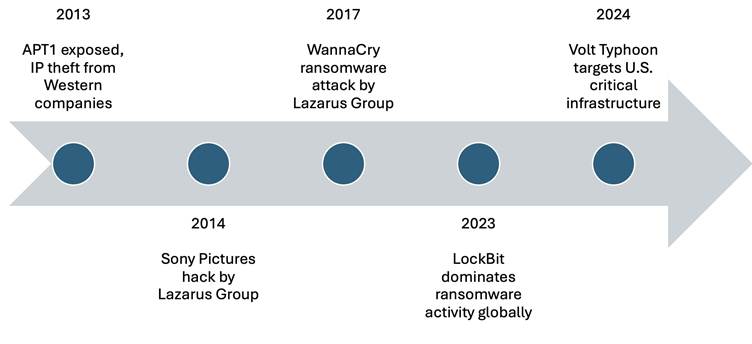
Threat Actor: Criminals exploiting backdoors | criminals exploiting backdoors Victim: Government and academic institutions | government and academic institutions
Key Point :
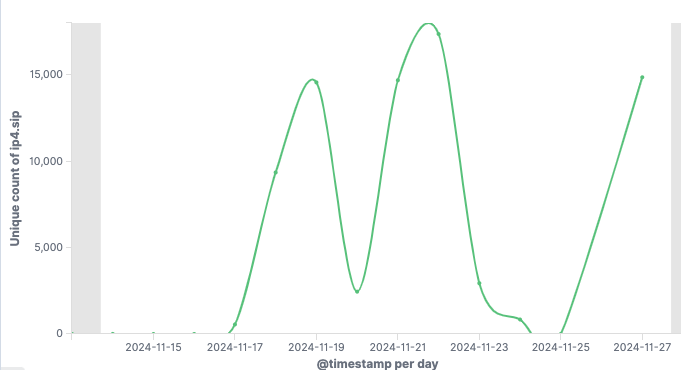
WatchTowr Labs identified over 4,000 compromised systems, including government and educational institutions.…