
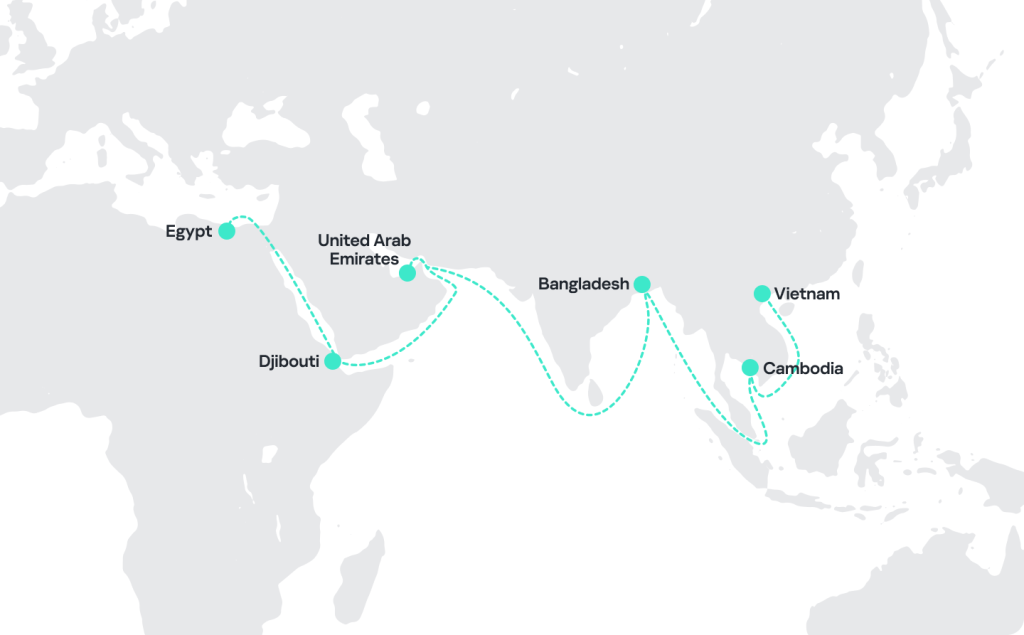
Summary: The SideWinder APT group has intensified its cyber-espionage efforts, specifically targeting maritime and nuclear sectors, while continuously evolving its malware and persistence strategies. Kaspersky Labs highlights notable increases in attacks across South and Southeast Asia, the Middle East, and Africa, as the group demonstrates refined techniques to maintain operational stealth.…
Read More 









 THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact
THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact




