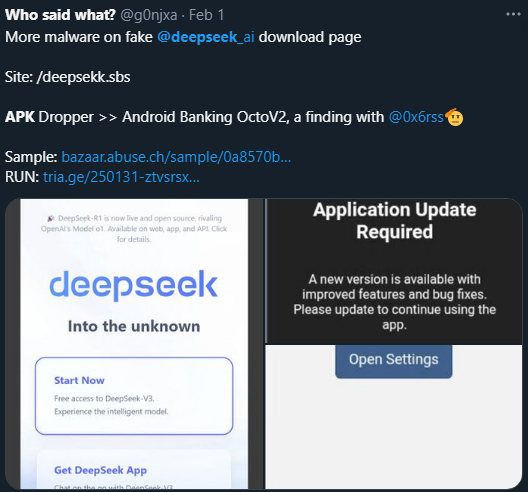
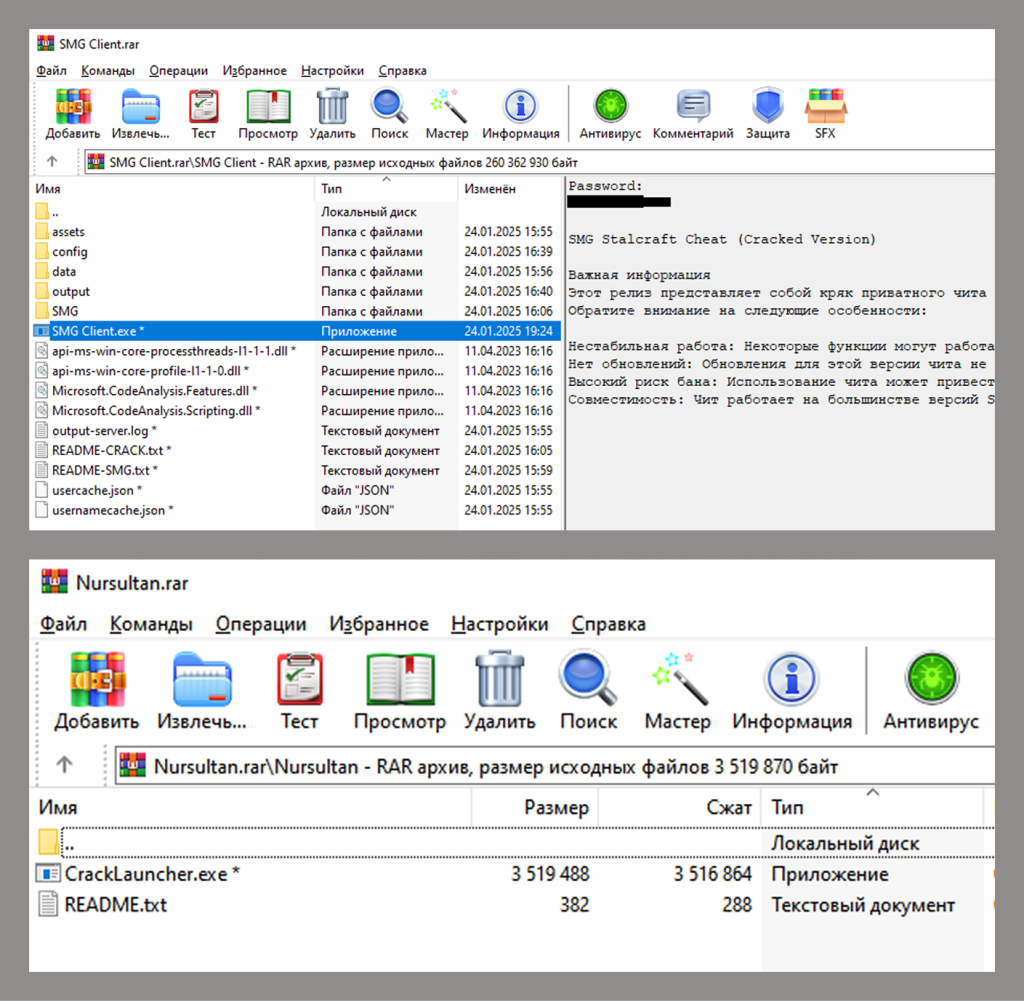
Summary: This week’s cybersecurity report highlights the evolving landscape of cyber threats, including advanced techniques used by threat groups and rising supply chain vulnerabilities. Law enforcement efforts against cybercriminal networks show promise, while new exploits and vulnerabilities demand prompt attention from organizations. The report includes notable incidents, emerging attack methods, and critical vulnerabilities that security teams should prioritize.…
Read More  THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More