
Summary: An unpatched security vulnerability in Microsoft Windows allows 11 state-sponsored groups to execute hidden malicious commands through crafted .LNK files, leading to significant risks of data theft and cyber espionage. Discovered by Trend Micro’s Zero Day Initiative (ZDI), the flaw has been utilized since 2017, targeting various organizations globally.…
Read More 



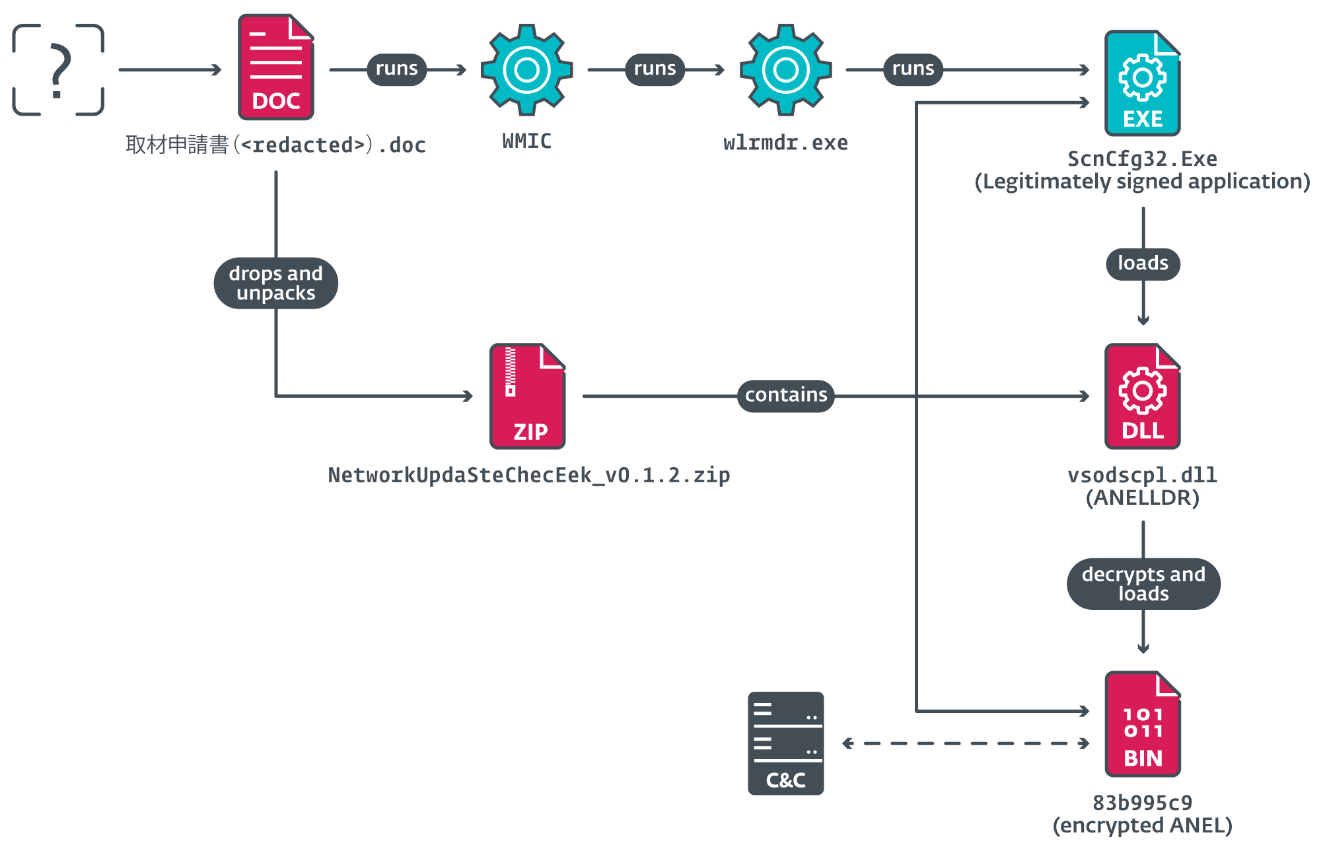
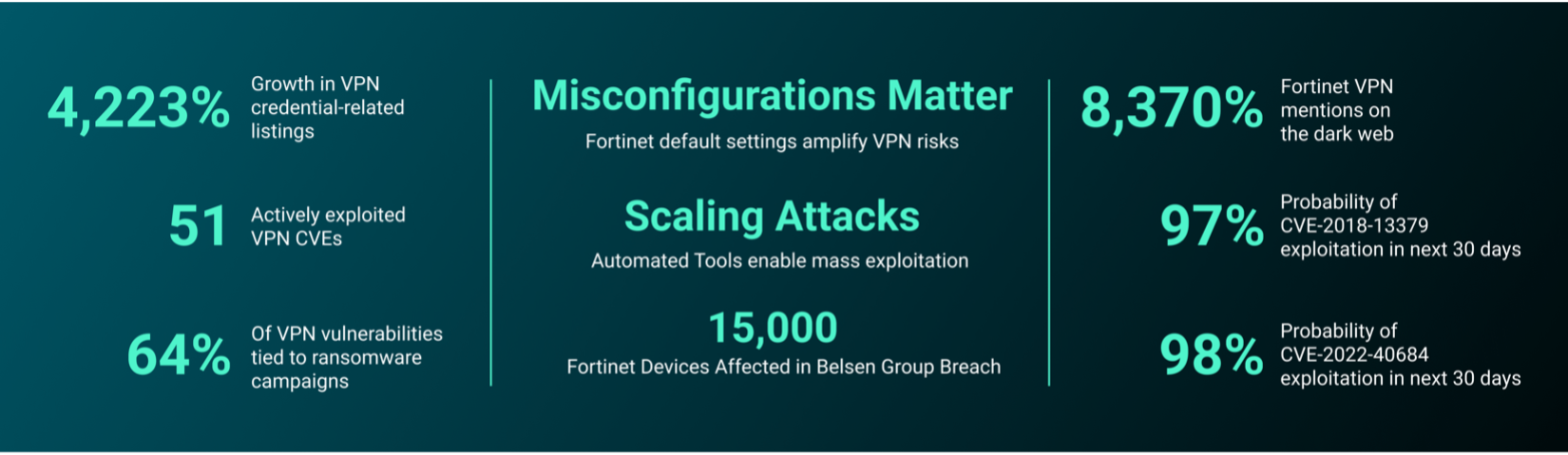




 THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More



