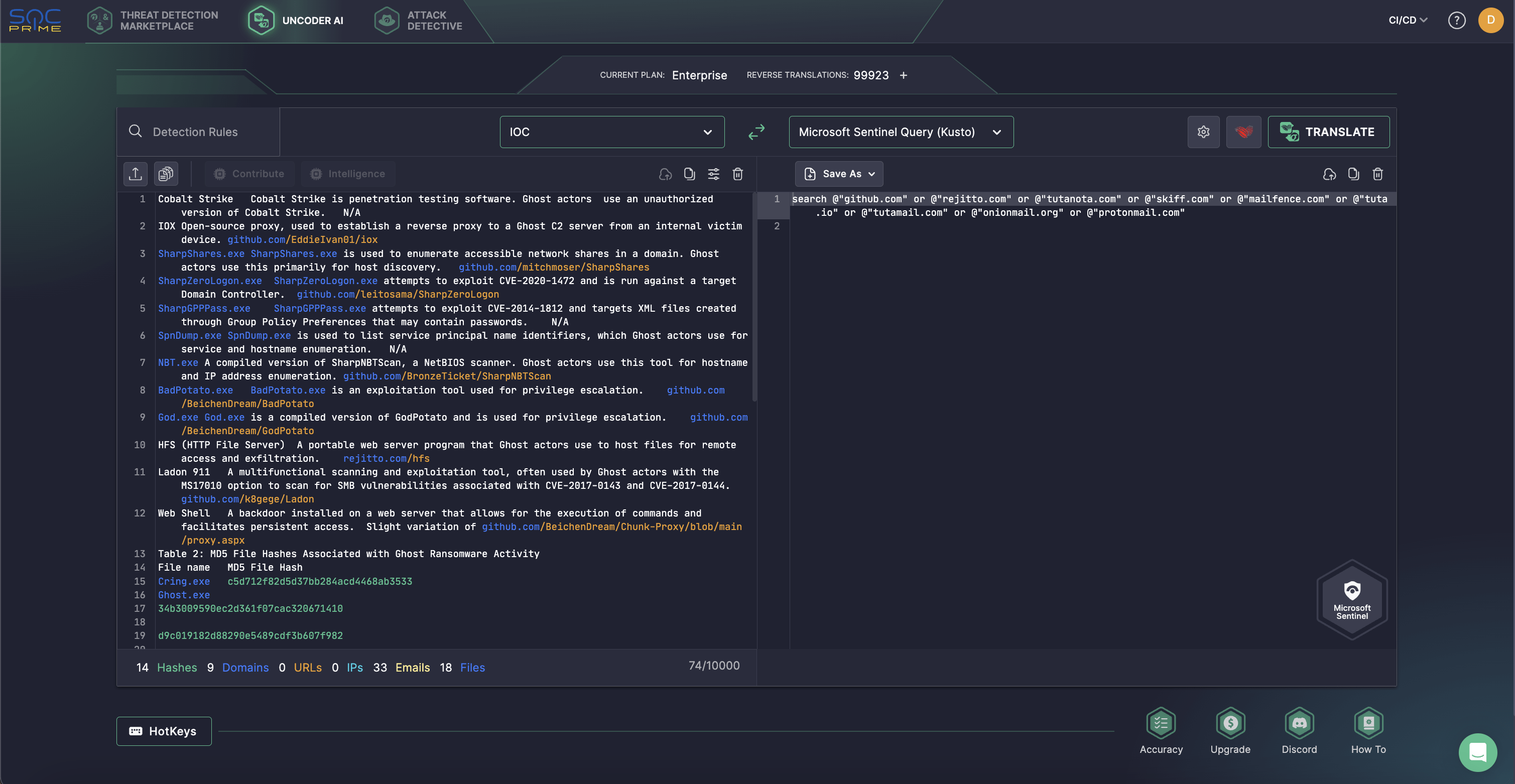
The US authorities, CISA and FBI, have issued warnings about the Chinese ransomware group Ghost, which has been active since 2021 and has targeted vulnerable systems in over 70 countries, including the US. Their operations span various sectors from critical infrastructure to small businesses, predominantly using publicly available exploit code to compromise outdated software and demanding ransoms while threatening data leaks.…
Read More