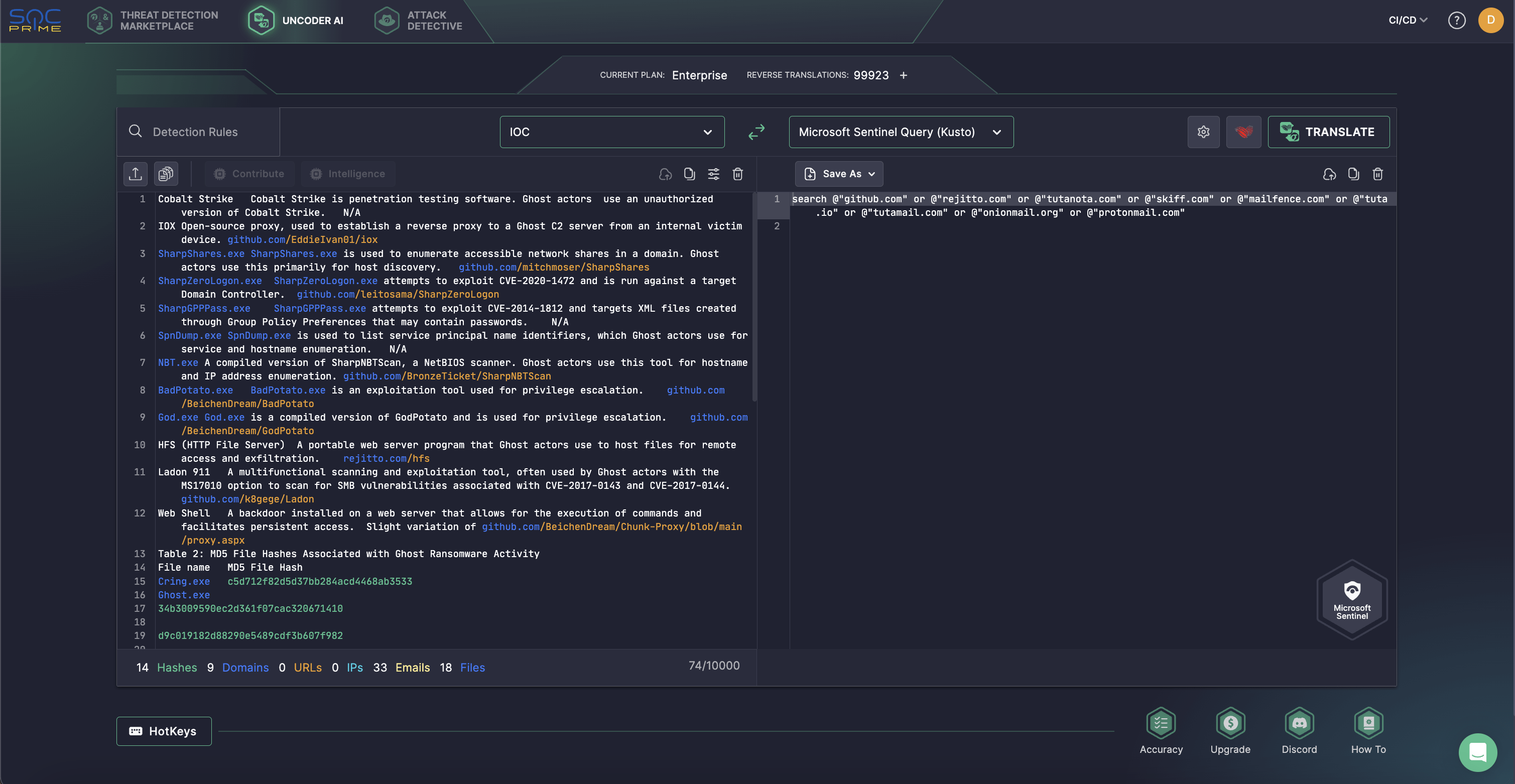
This report discusses the evolving landscape of cybercrime and state-sponsored threats targeting the financial sector, focusing on Initial Access Brokers (IABs), ransomware groups, and Trojan operators. It highlights the roles of various actors and techniques, showcasing the persistent threat posed by these entities through sophisticated malware, exploitation of vulnerabilities, and collaborative tactics.…
Read More