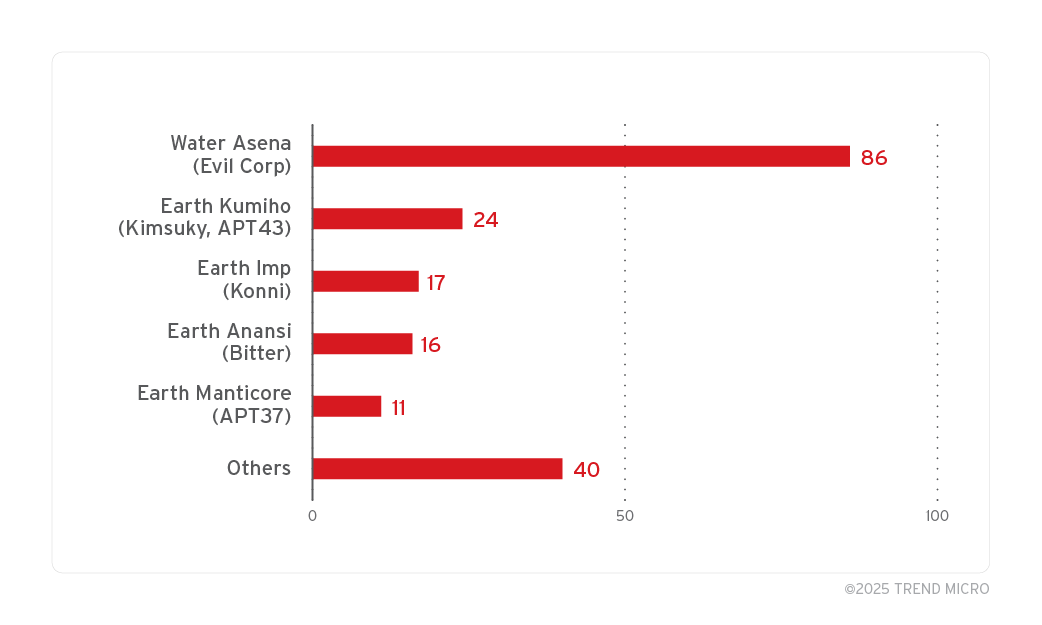
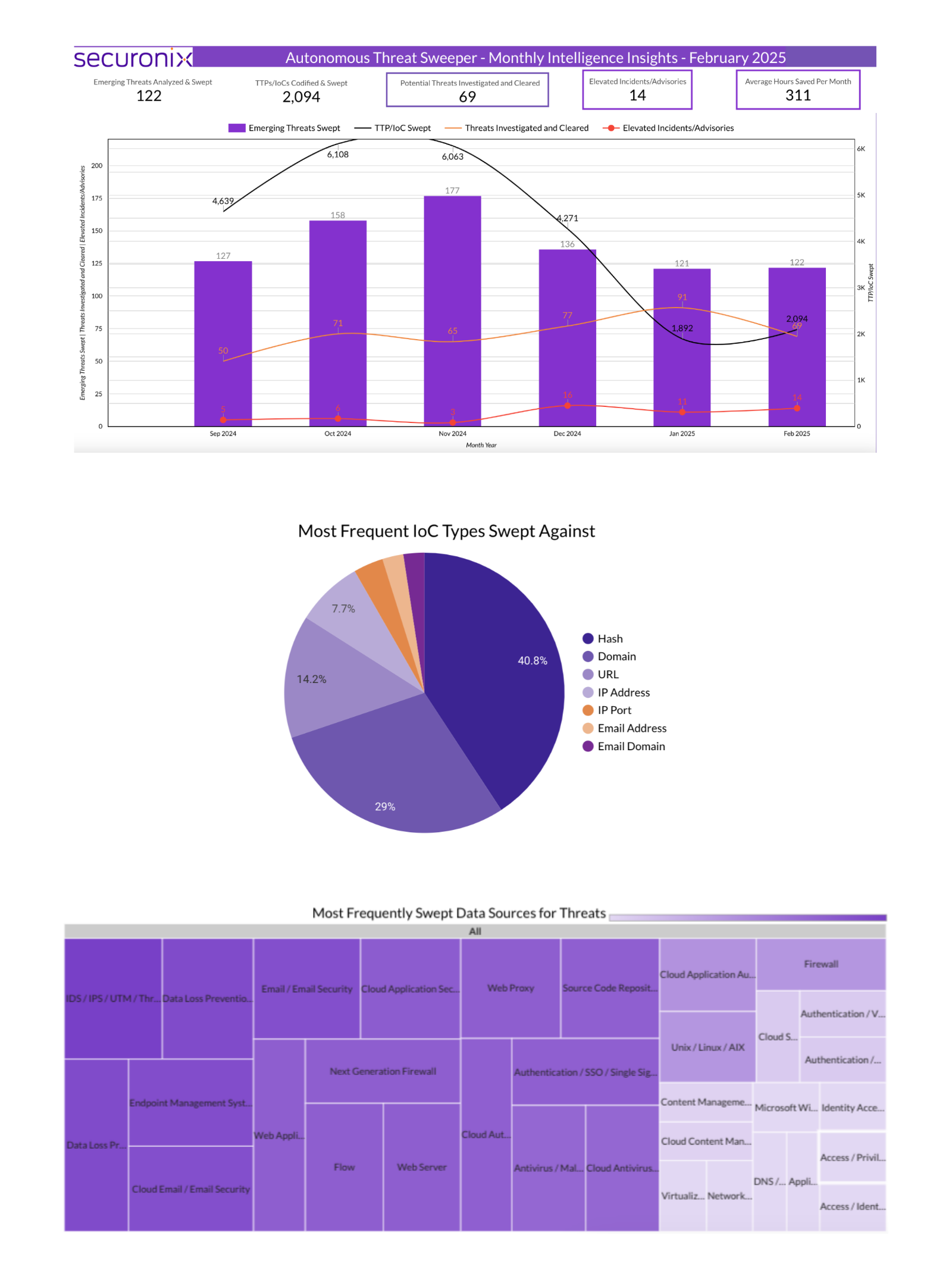
This article explores various threat actors known for their significant cyber attacks, detailing their origins, techniques, and famous hacks. It categorizes these actors by their affiliations, such as state-sponsored and financially motivated groups, providing insight into their behaviors and methodologies. Affected: Government networks, financial institutions, healthcare, energy sector, retail, hospitality, media, technology, and more.…
Read More 


 THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More