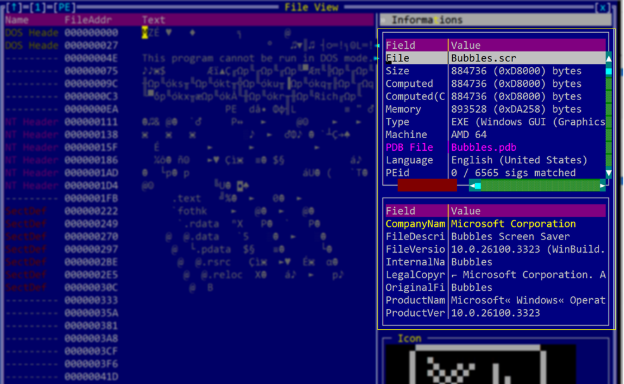
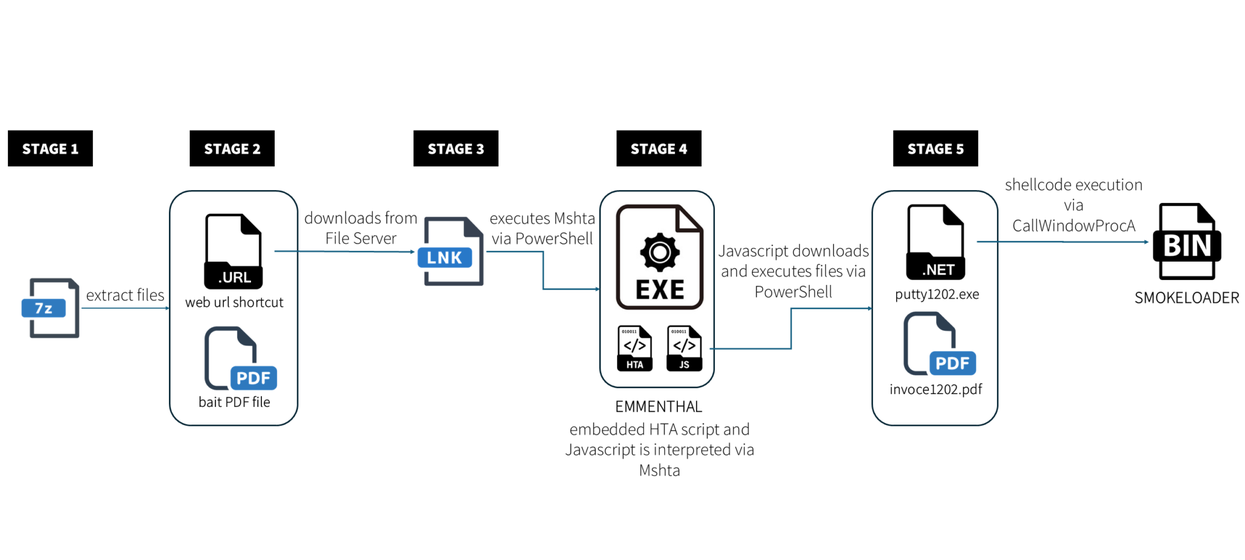
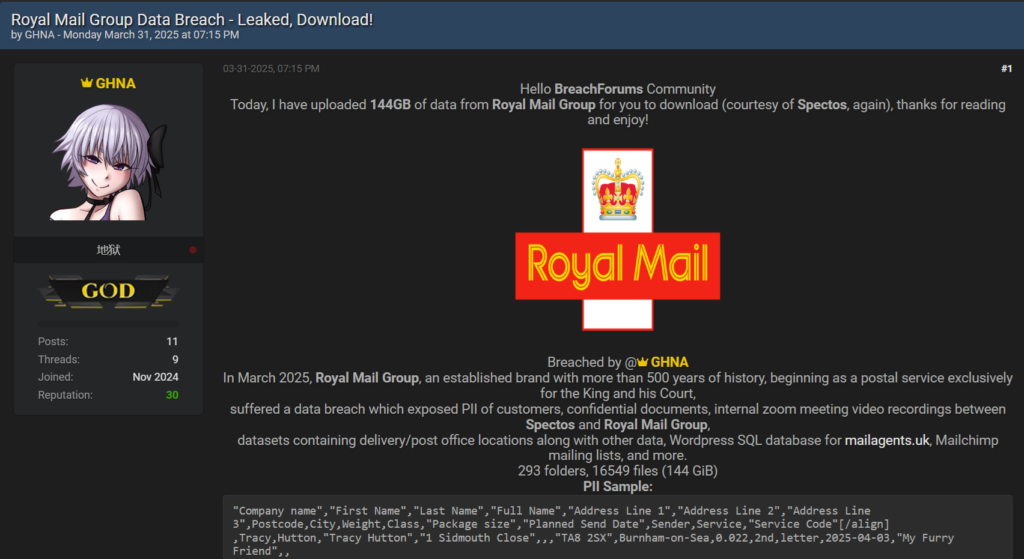
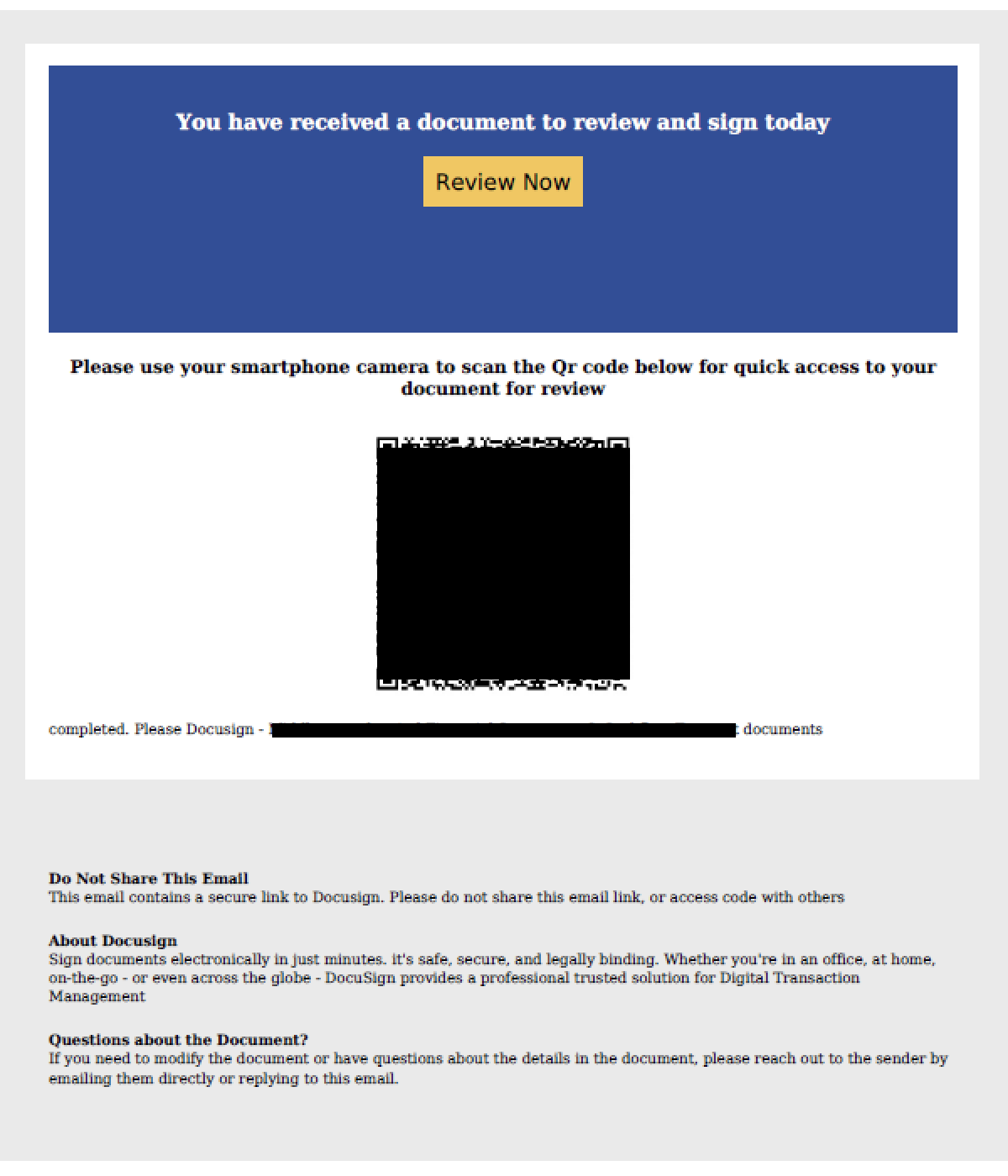
Summary: Microsoft has issued warnings about multiple phishing campaigns utilizing tax-related themes to distribute malware and steal credentials. These campaigns employ sophisticated methods like URL shorteners and QR codes to mask malicious intent while targeting thousands of organizations, especially in the U.S. The attacks often involve a phishing-as-a-service platform, RaccoonO365, and various malware types, including remote access trojans and information stealers.…
Read More