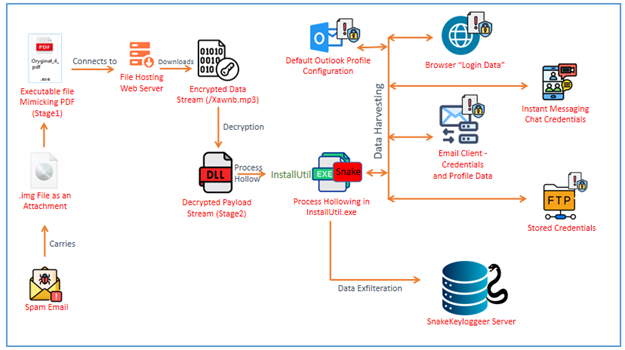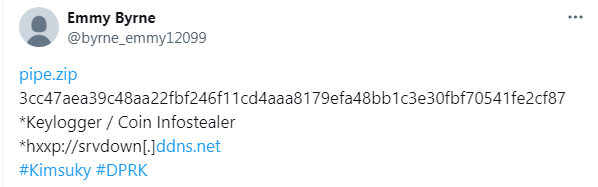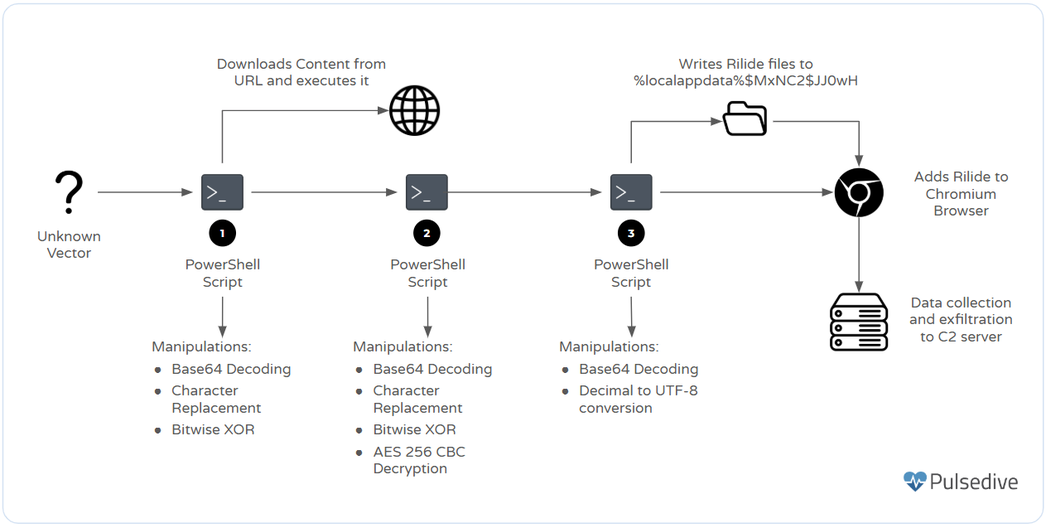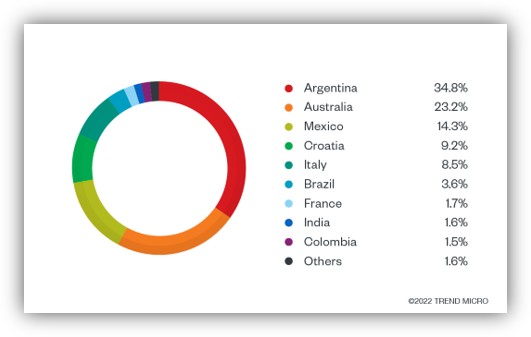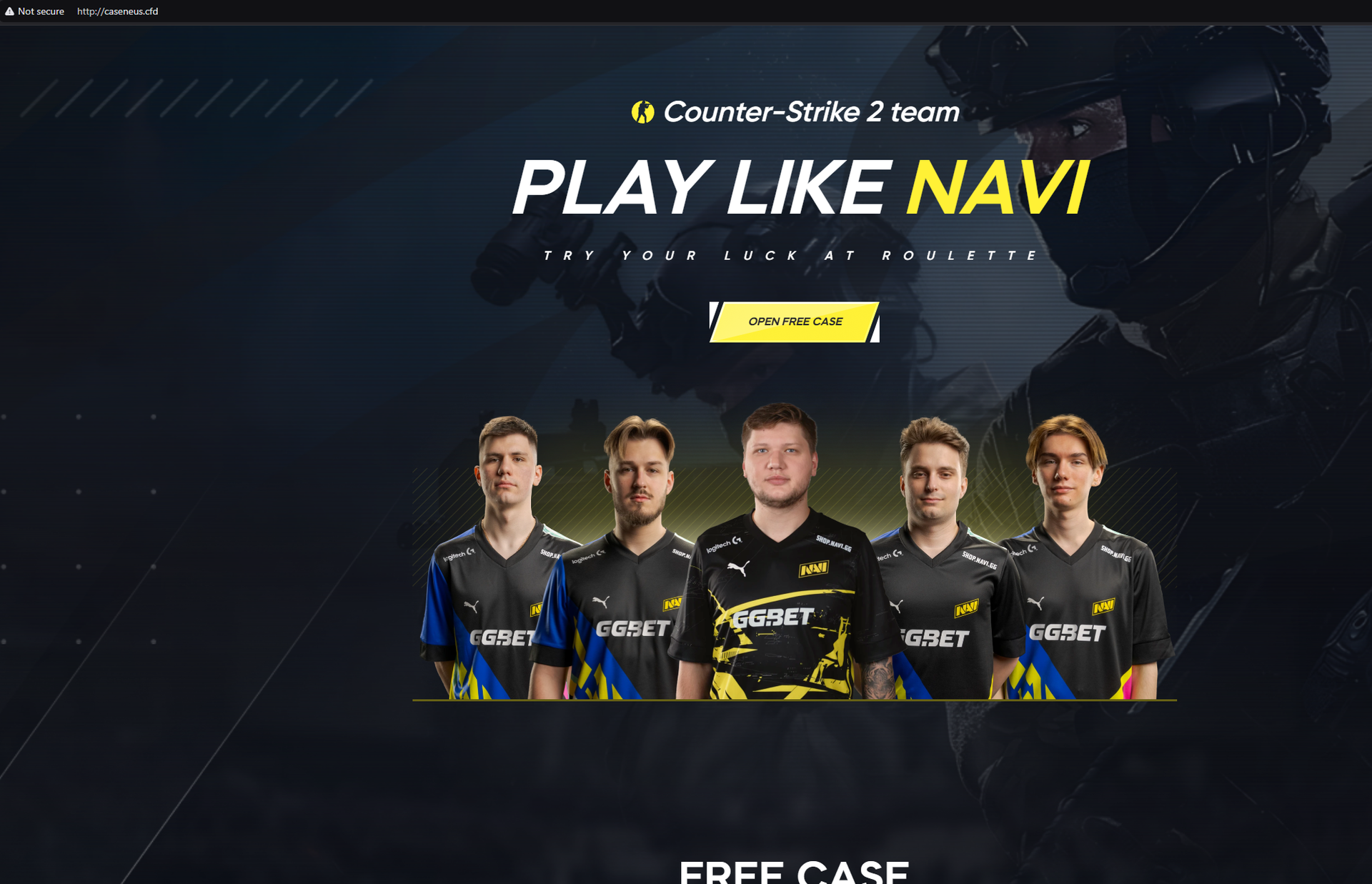
A new phishing campaign targets Counter-Strike 2 players through complex browser-in-the-browser (BitB) phishing attacks using fake pop-up windows that impersonate legitimate sites. The campaign aims to steal Steam credentials, especially affecting fans of the esports team Navi, with potential resale of compromised accounts on various platforms.…
Read More