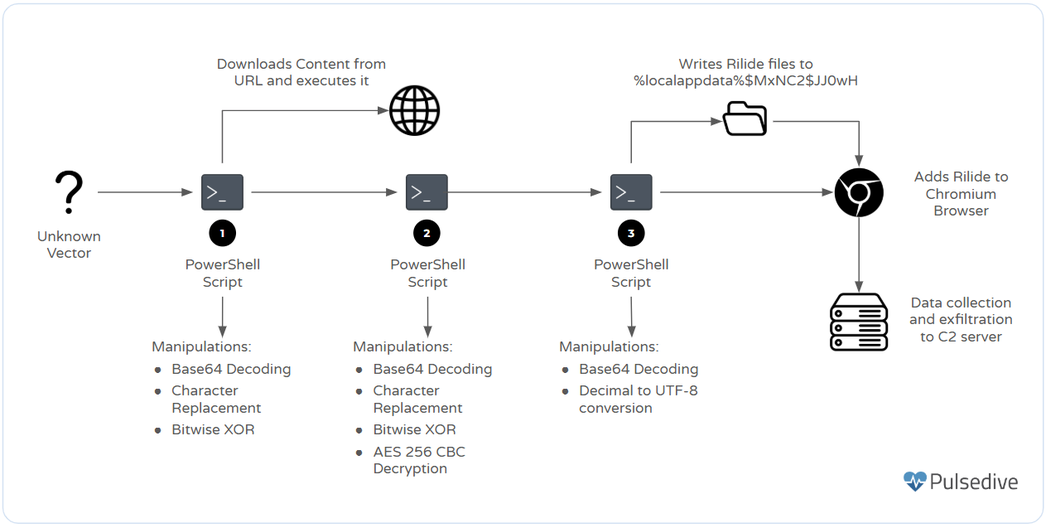
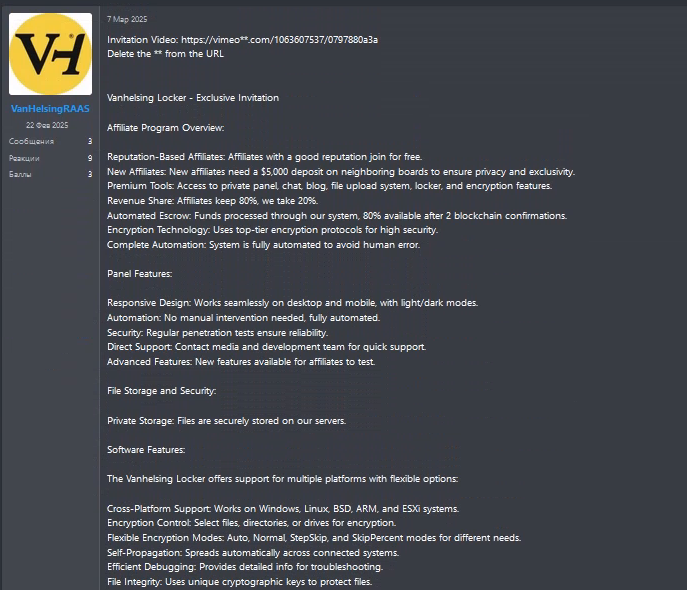
The article discusses the operations of the Wagmi Team, a group involved in NFT scams, which has made over .4 million since June 2023 by targeting victims on platforms like X and Discord. They use phishing tactics to compromise cryptocurrency wallets and deploy malicious applications disguised as web3 projects.…
Read More