Summary: A new smishing scam is targeting individuals by masquerading as toll providers demanding payment for unpaid tolls through fraudulent text messages. The messages often threaten consequences for non-payment and include suspicious links designed to harvest personal information. Victims are urged to report and delete the messages, and to take protective measures for their sensitive data if they’ve interacted with the scammers.…
Read More 
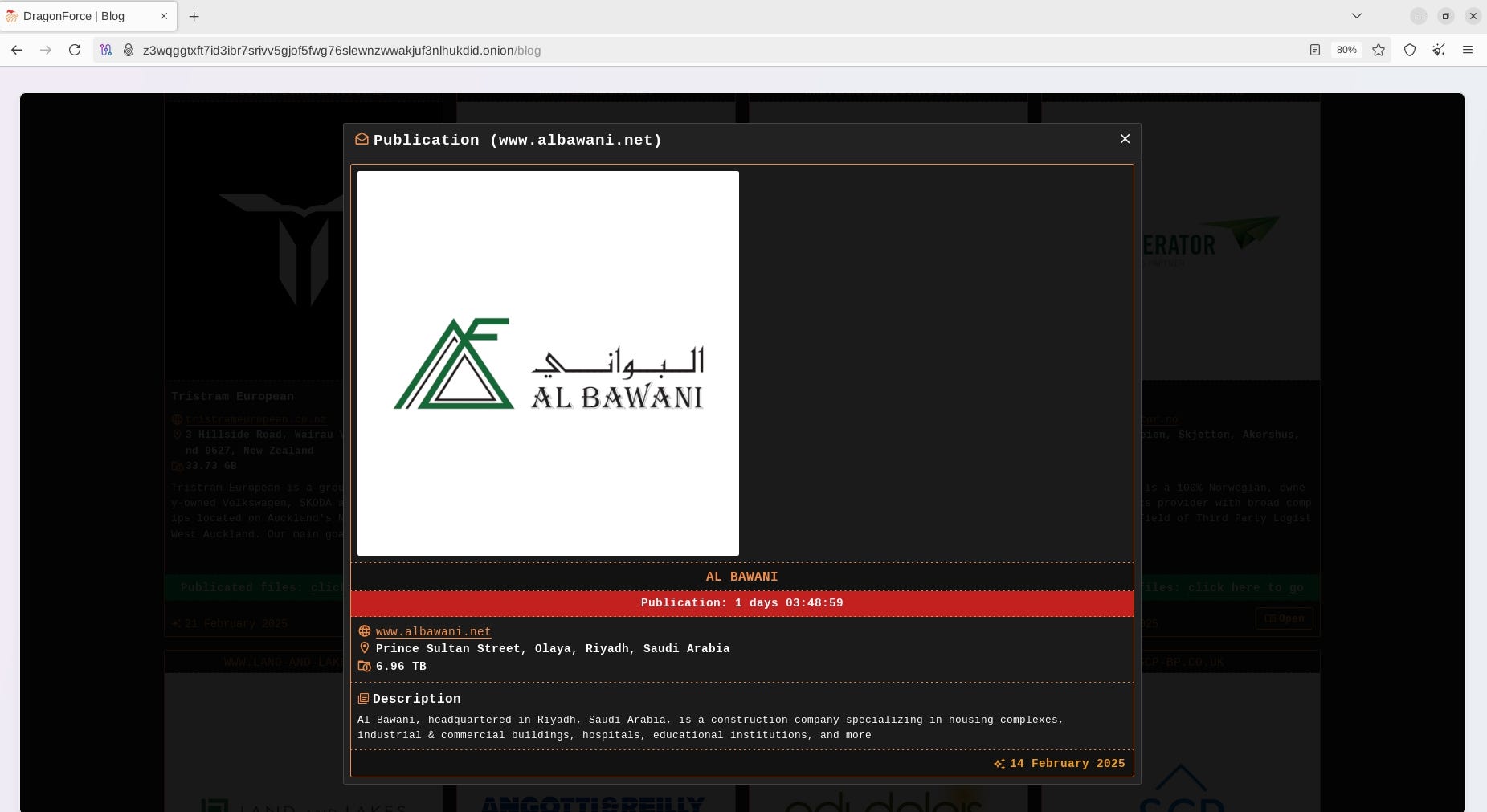




![[Law] Three arrested for hacking hospital CCTV and selling videos of female patients [Law] Three arrested for hacking hospital CCTV and selling videos of female patients](https://www.hendryadrian.com/tweet/image/cybersecuritynews.png)