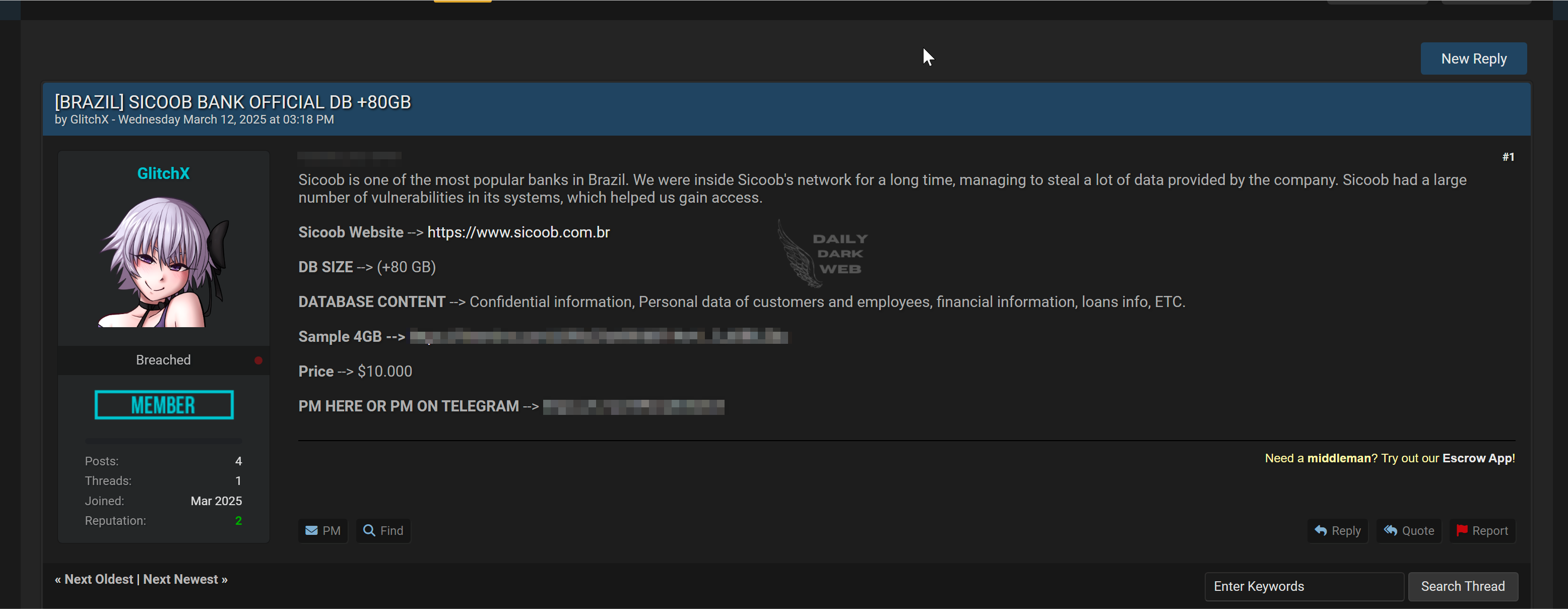
Summary: A threat actor has claimed to have breached the internal network of Sicoob, a leading cooperative bank in Brazil, and reportedly exfiltrated over 80GB of confidential data. The individual has posted their claims on a dark web forum, offering portions of the stolen data for sale.…
Read More 









![[Law] Three arrested for hacking hospital CCTV and selling videos of female patients [Law] Three arrested for hacking hospital CCTV and selling videos of female patients](https://www.hendryadrian.com/tweet/image/cybersecuritynews.png)
