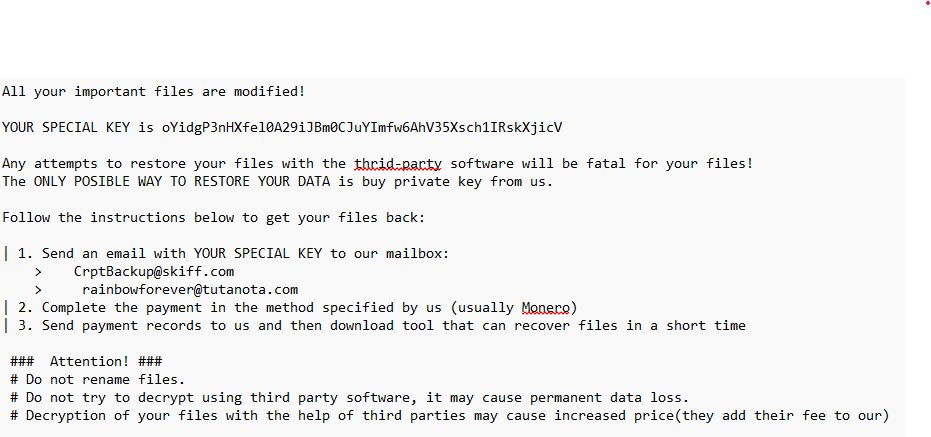
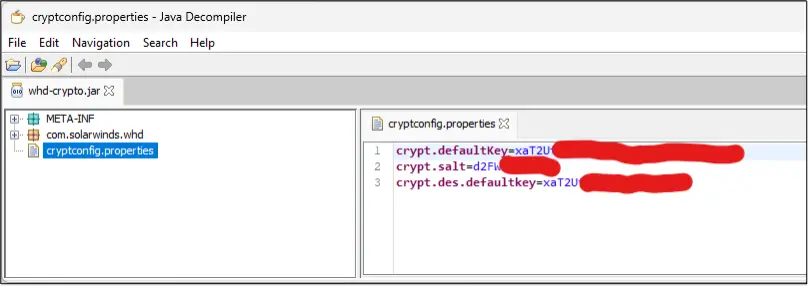
Summary: A new ransomware variant called Elysium, linked to the Ghost ransomware family, targets critical sectors like healthcare and government. The attackers exploit outdated applications to gain access and deploy various tools to execute a multi-stage attack. Elysium disrupts recovery efforts by targeting backups and encrypting files with a specific extension while demanding a ransom in Monero for decryption.…
Read More 





 THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact
THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact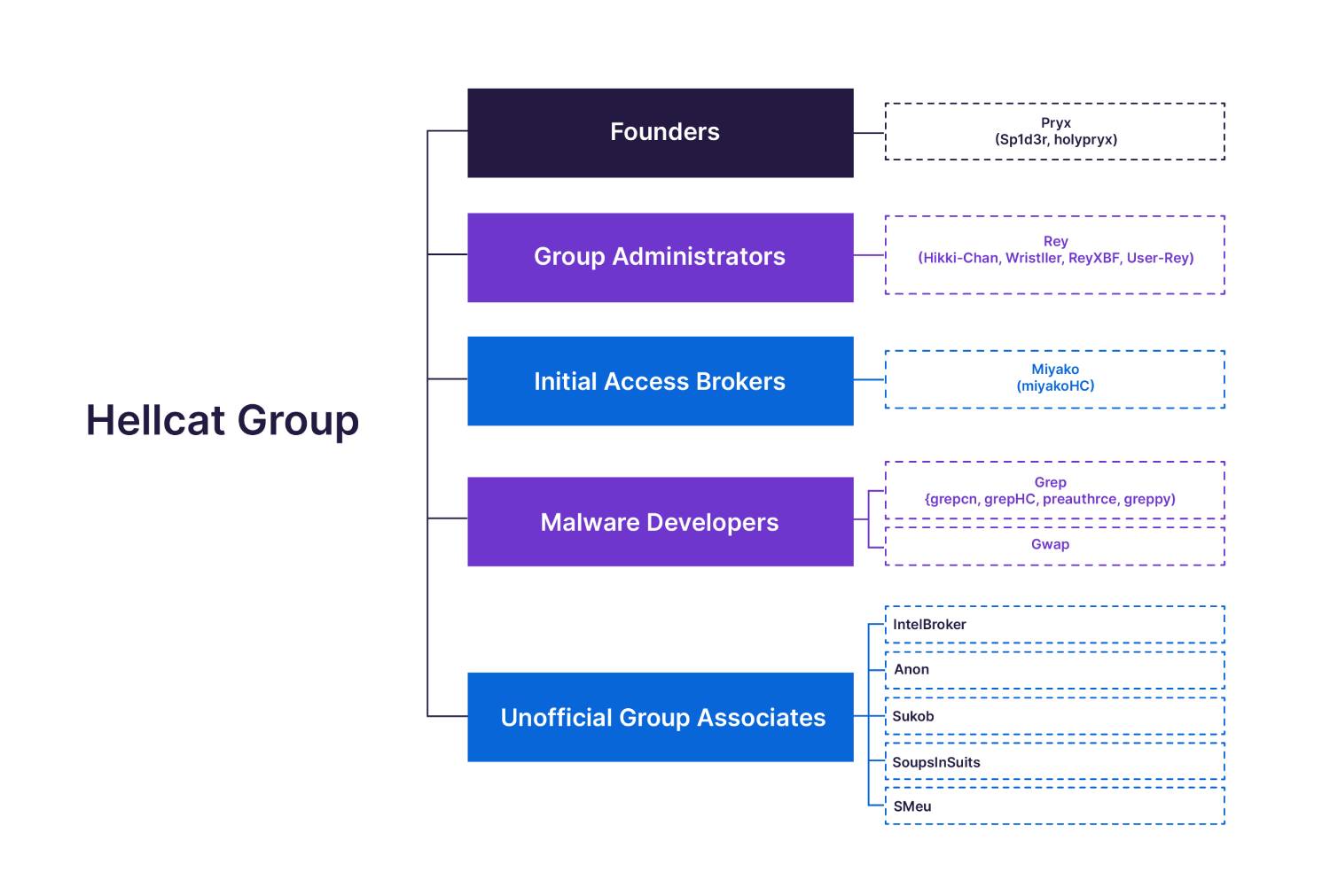



_syahrir_maulana_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)