Date Reported: 2025-02-02
Country: FRA | France
Victim: Mairie d’Ostheim | Ostheim Town Hall
Website: ostheim.fr
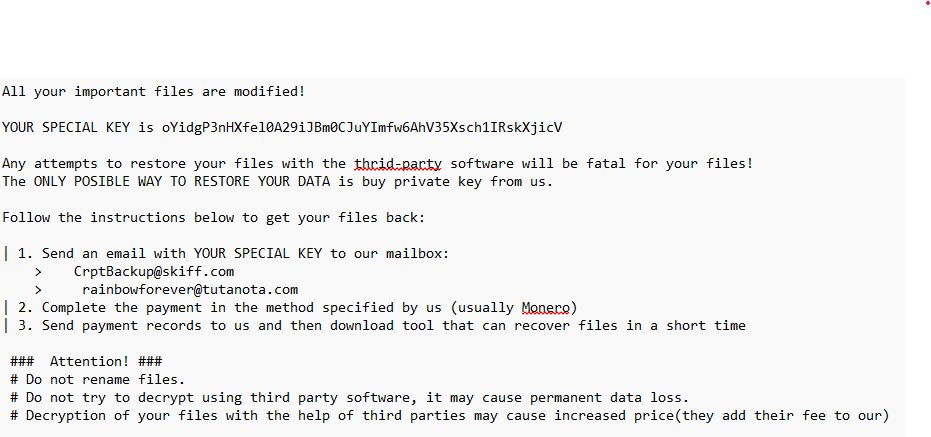
Information :On February 2, 2025, the town hall of Ostheim in Haut-Rhin was targeted by a ransomware cyberattack.
The attack resulted in 95% of the town hall’s data being encrypted.…
Read More 



 THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More