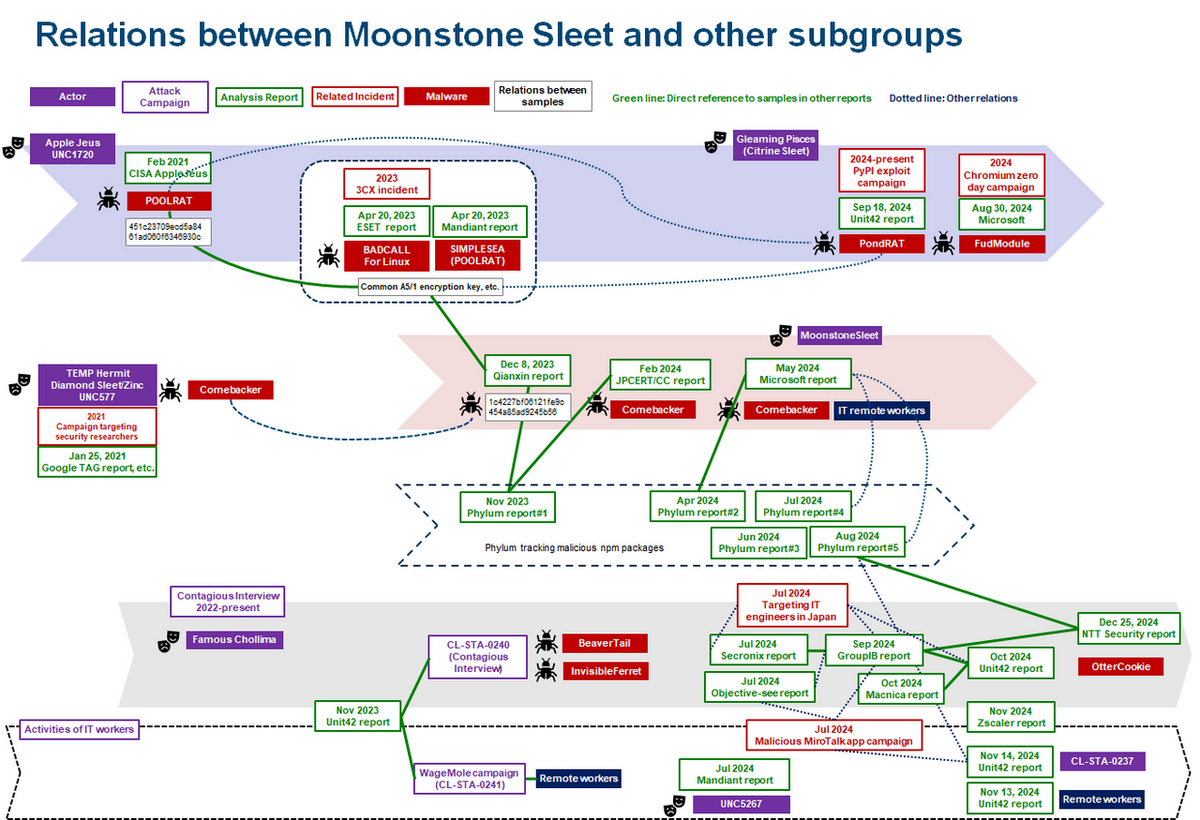
A major telecommunication company in Asia has been targeted by a persistent threat actor identified as Weaver Ant, linked to China. The group has used stealthy techniques like web shells to maintain access and facilitate cyber espionage. This highlights the need for organizations to develop robust defense strategies against state-sponsored threats.…
Read More