.png)
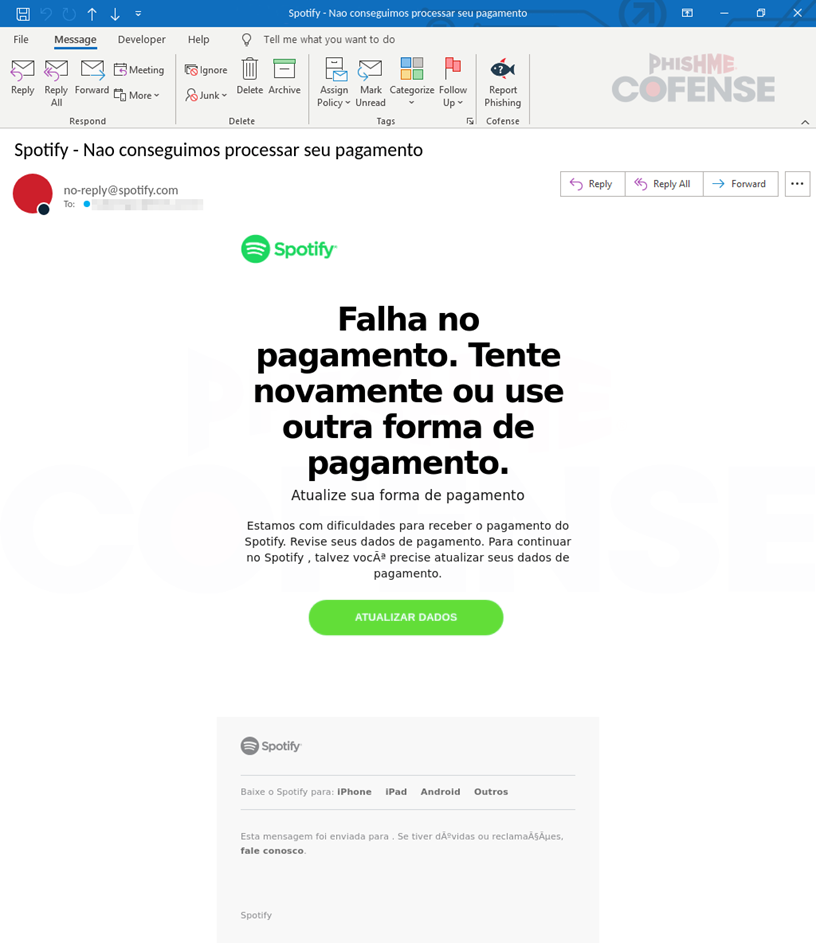
In an alarming trend, attackers are increasingly targeting popular streaming services like Spotify to steal personal and financial information. Cybercriminals exploit users’ trust through phishing emails that impersonate legitimate communications from these platforms. Users are tricked into providing sensitive information by responding to deceptive requests, revealing the importance of vigilance and cybersecurity practices.…
Read More