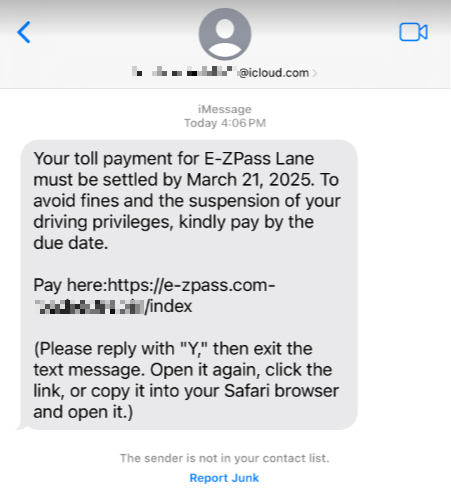
Summary: Cybersecurity researchers have discovered deceptive websites impersonating legitimate app stores to distribute SpyNote malware, which targets Android devices. This malware is linked to known threat actors, including state-sponsored groups, and is capable of extensive data theft and control over infected devices. Additionally, intelligence agencies have issued alerts regarding other malware threats like BadBazaar and MOONSHINE, which target specific communities for surveillance.…
Read More