Summary: Canadian authorities have arrested Alexander “Connor” Moucka, accused of stealing data from hundreds of millions by targeting over 165 organizations using compromised credentials. The attacks exploited a lack of multi-factor authentication on Snowflake accounts, affecting numerous high-profile companies and their customers.
Threat Actor: Alexander “Connor” Moucka | Alexander Moucka
Victim: Snowflake customers | Snowflake customers
Key Point :
- Alexander Moucka was arrested at the request of the United States on a provisional arrest warrant.
- The attacks targeted organizations that did not implement multi-factor authentication, leading to significant data breaches.
- High-profile victims include Mastercard, AT&T, and Ticketmaster, affecting hundreds of millions of individuals.
- Snowflake plans to enforce multi-factor authentication and stronger password requirements starting October 2024.

Canadian authorities have arrested a man suspected of having stolen the data of hundreds of millions after targeting over 165 organizations, all of them customers of cloud storage company Snowflake.
According to Canada’s Department of Justice, Alexander “Connor” Moucka (aka “Waifu” and “Judische”) was taken into custody on Wednesday at the request of the United States and is scheduled to appear in court again today, as first reported by Bloomberg and confirmed by 404 Media.
“Following a request by the United States, Alexander Moucka (a.k.a. Connor Moucka) was arrested on a provisional arrest warrant on Wednesday October 30, 2024,” Ian McLeod, a spokesperson for Canada’s Department of Justice, told BleepingComputer on Tuesday.
“He appeared in court later that afternoon and his case was adjourned to Tuesday November 5, 2024. As extradition requests are considered confidential state-to-state communications, we cannot comment further on this case.”
A joint investigation by SnowFlake, Mandiant, and CrowdStrike found that an attacker (tracked at the time as UNC5537) used customer credentials stolen using infostealer malware to target at least 165 organizations that failed to configure multi-factor authentication (MFA) protection on their SnowFlake accounts.
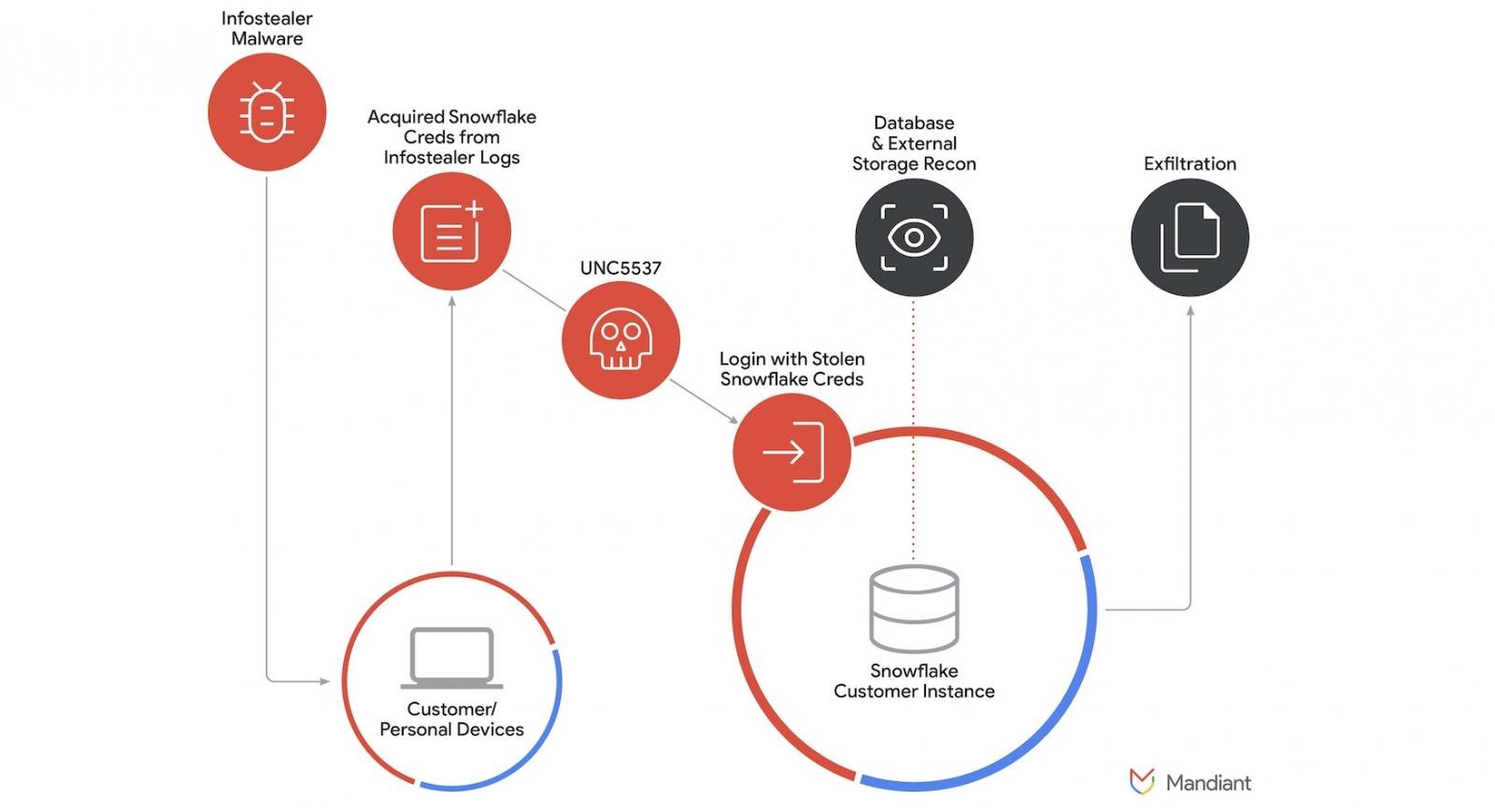
That is just a tiny part of the 9,400 Snowflake customers, with the complete list including some of the largest companies worldwide, such as Mastercard, Micron, NBC Universal, Capital One, Adobe, AT&T, Kraft Heinz, Doordash, HP, Okta, PepsiCo, Siemens, US Foods, Western Union, Yamaha, and many others.
Data breaches linked to these attacks, which started in April 2024, have affected hundreds of millions of individuals using the services of AT&T, Ticketmaster, Santander, Pure Storage, Advance Auto Parts, Los Angeles Unified, QuoteWizard/LendingTree, and Neiman Marcus.
In late May, Ticketmaster confirmed that data was stolen from its Snowflake account after a threat actor known as ShinyHunters began the data of 560 million Ticketmaster customers.
In July, AT&T also warned of a massive data breach after threat actors stole the call logs of approximately 109 million customers (nearly all of its mobile customers) from an online database on the company’s Snowflake account between April 14 and April 25, 2024.
Snowflake has since announced that it will enforce multi-factor authentication (MFA) for accounts created starting in October 2024 and require that all passwords be at least 14 characters long.