Summary: A sophisticated phishing campaign utilizing Strela Stealer malware has been identified, primarily targeting German and Spanish-speaking regions in Central and Southwestern Europe. The campaign employs advanced techniques, including WebDAV-based execution and heavily obfuscated JavaScript files, to exfiltrate sensitive data from compromised systems.
Threat Actor: Unknown | Strela Stealer
Victim: Individuals and organizations in Central and Southwestern Europe | German and Spanish-speaking regions
Key Point :
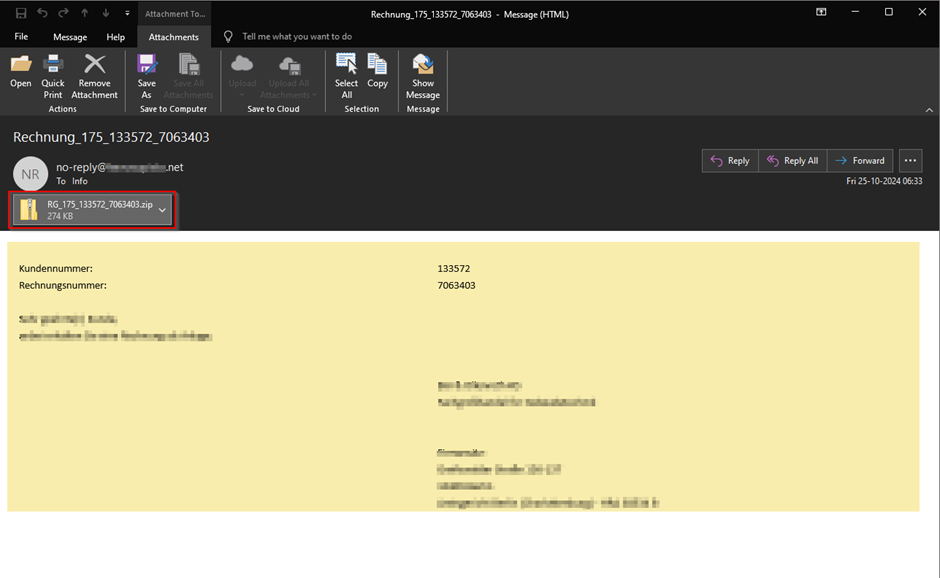
- The phishing campaign uses spear-phishing emails disguised as invoice notifications to deliver ZIP file attachments containing obfuscated JavaScript files.
- Strela Stealer employs WebDAV for malware delivery, allowing it to execute without writing to disk, thus evading detection by security tools.
- The malware targets email credentials from Microsoft Outlook and Mozilla Thunderbird, exfiltrating sensitive information to a command-and-control server.
- Locale-based targeting ensures that the malware only executes on systems set to German, Spanish, or Basque languages, indicating a focused attack strategy.
- The campaign highlights the increasing sophistication of phishing attacks, necessitating enhanced cybersecurity measures to protect against such threats.
A recent report from Cyble Research and Intelligence Labs (CRIL) highlights a sophisticated phishing campaign deploying Strela Stealer, a malware designed to exfiltrate sensitive data from compromised systems. This campaign is focused on Central and Southwestern Europe, with specific targeting aimed at German and Spanish-speaking regions. Strela Stealer has evolved to use advanced techniques, including WebDAV-based execution, to evade detection and enhance data theft capabilities.
The campaign uses spear-phishing emails crafted to look like invoice notifications, enticing victims to open ZIP file attachments. CRIL notes that “the phishing emails carry ZIP file attachments containing heavily obfuscated JavaScript (.js) files,” which are specifically designed to evade detection by common security tools. Once the victim opens the ZIP file, they encounter a JavaScript file that, when executed, decodes a PowerShell command to load the Strela Stealer payload from a remote WebDAV server.
The use of WebDAV for delivering the malware is a key tactic in this campaign. By downloading and executing the malicious DLL payload directly from a WebDAV server, Strela Stealer avoids writing the payload to disk, a technique that effectively bypasses security products. CRIL reports, “This JavaScript code executes a base64-encoded PowerShell command, which executes the final malicious DLL from a WebDAV server using ‘rundll32.exe’”. This approach complicates detection and prevents many endpoint protection solutions from identifying the malware.
Once executed, Strela Stealer focuses on stealing email credentials from Microsoft Outlook and Mozilla Thunderbird, two of the most widely used email clients. It extracts usernames, passwords, and server configurations, sending this information to a command-and-control (C2) server. In the case of Thunderbird, the malware scans for profiles and collects the “logins.json” and “key4.db” files, which store encrypted user credentials. The data is then encrypted using a hardcoded key, “96be98b2-8a00-410d-87da-2482cc8b7793,” before being sent to the C2 server.
In addition to email credentials, Strela Stealer performs reconnaissance by gathering system information through the “systeminfo” command. This data, along with a list of sensitive filenames on the system, is exfiltrated to the C2 server, allowing attackers to map the victim’s file structure for potential further exploitation.
Strela Stealer employs locale-based targeting to refine its focus on specific regions. It checks the victim’s system locale to determine if it matches German (0407), Spanish (0C0A), or Basque (042D) before proceeding with its data theft operations. If the locale does not match these identifiers, the malware halts execution, demonstrating the attackers’ intent to target German and Spanish-speaking regions specifically.
The Strela Stealer campaign exemplifies the growing sophistication of phishing campaigns, using stealthy techniques like WebDAV-based execution and obfuscation to bypass security defenses. As CRIL warns, “the recent iterations of the Strela Stealer campaign reveal a notable advancement in malware delivery techniques,” highlighting the need for vigilant cybersecurity practices to counteract such targeted attacks.