Executive Summary
In this post, we share information about how security professionals can take analysis shortcuts to quickly triage and analyze multiple malware samples. Within minutes, we can determine the malware families from a group of samples, parse the embedded configuration and extract the associated network indicators of compromise (IoCs).
For example, earlier this year we quickly responded to requests for information related to cyberattacks against Ukrainian targets that used commercial attack tools like Quasar RAT. From a single sample that one of our industry partners shared, we pivoted to a Bitbucket repository that contained 10 other samples belonging to the same threat actor.
Using malware configuration parsing at scale not only speeds up the analysis process but also reduces the need for manual reverse engineering of individual samples. Malware configuration extractors, available both commercially and in open-source projects, serve as exceptional tools for quickly obtaining answers when time is critical. Our results from Advanced WildFire’s Malware Configuration Extraction (MCE) system indicate this approach is extremely useful to efficiently analyze large volumes of malware.
Palo Alto Networks customers are better protected from the malware discussed in this article through our Network Security solutions and Cortex line of products, including Cortex XDR and XSIAM. Advanced URL Filtering and Advanced DNS Security identify known URLs and domains associated with this activity as malicious.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
Introduction
As malware analysts, we often find ourselves making tough choices related to time management. This is particularly true when protecting our customers in time-critical situations. Cybercriminals create an endless stream of malware with megabytes of irrelevant code and obfuscated payloads intentionally crafted to make our jobs harder and delay countermeasures.
Using MCE, we automated the extraction of configurations from multiple malware families to speed our analysis. These configurations consisted of various IoCs like command and control (C2) addresses, unique identifiers and attack parameters.
Discovering the Malware Repository
In early 2024, Unit 42 observed an increase in attackers using off-the-shelf software for malware against specific targets of interest. During one of these attacks, an industry partner provided us with information on one such malware example.
We analyzed and extracted the C2 server address used by this sample. Pivoting on this information revealed a Bitbucket repository hosting the second stage payloads. Further investigation revealed 10 additional samples hosted and deployed from the same repository.
At the time of the investigation, none of these samples were available on VirusTotal. Figure 1 shows a screenshot of the repository before it was taken offline.
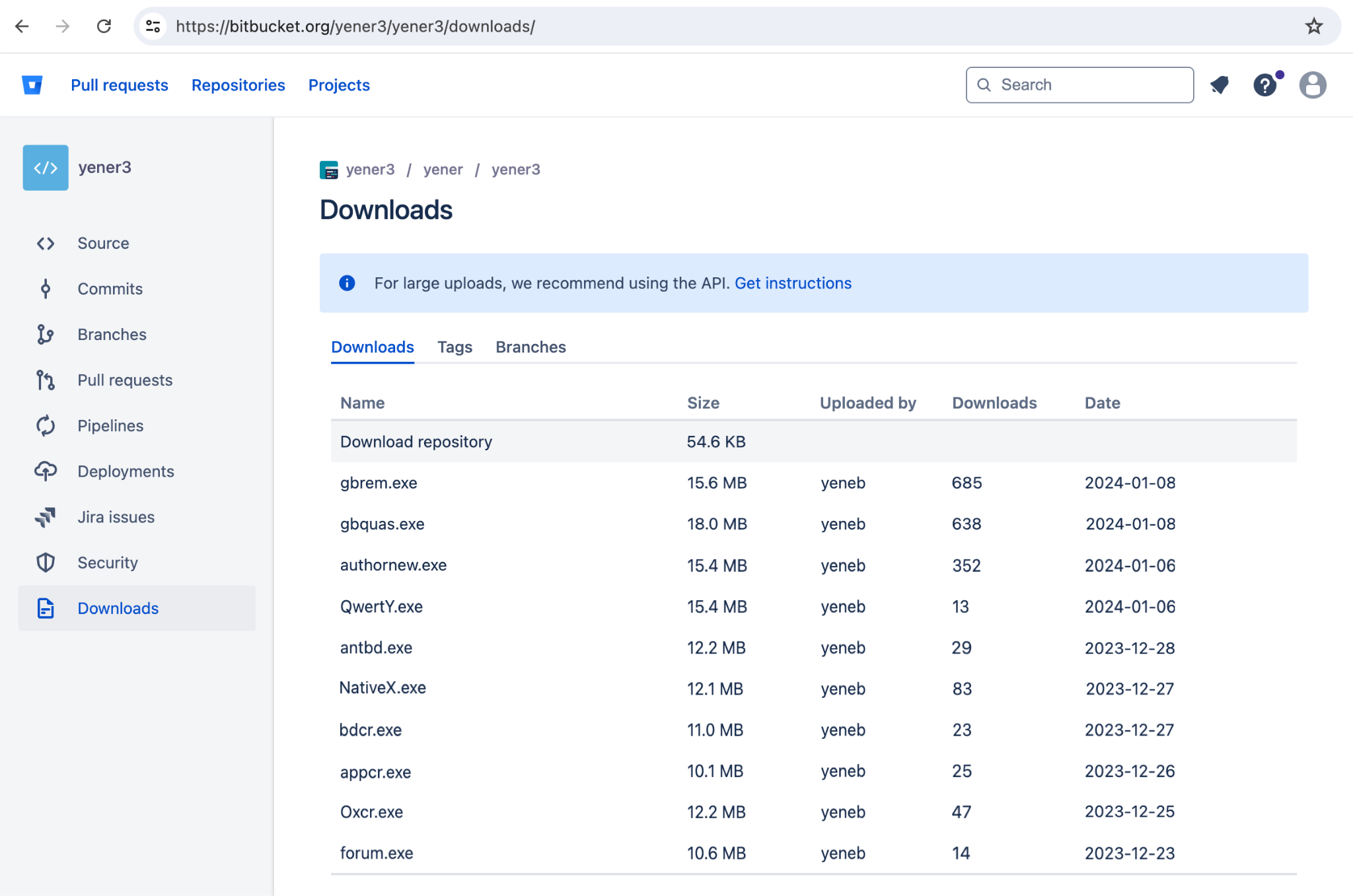
To identify the malware samples and extract their IoCs, we submitted them to Advanced WildFire’s MCE.
Automated Analysis Doing the Heavy Lifting
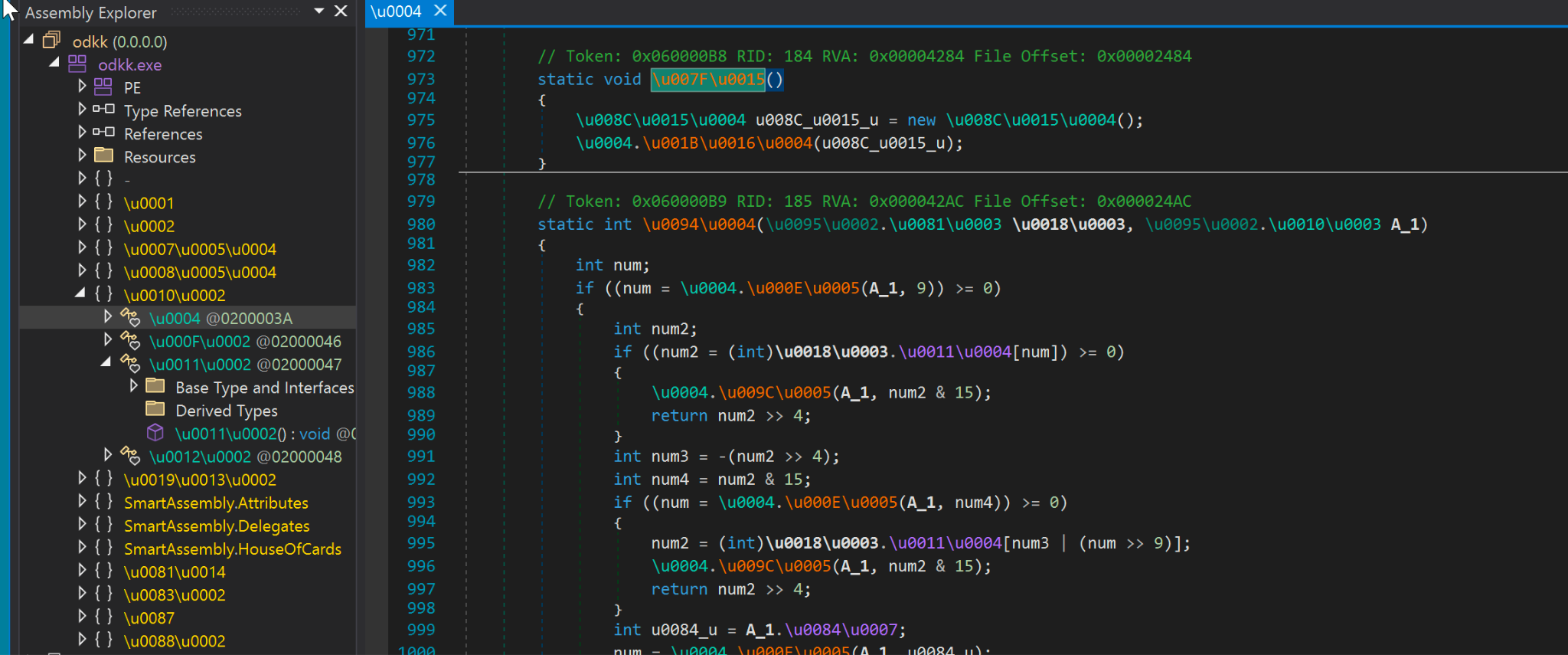
Attempting to extract IoCs from individual samples would have been a challenging task due to the obfuscation present in all the samples. Figure 2 below depicts the obfuscated code of one of the samples, a Windows executable for Lumma Stealer.
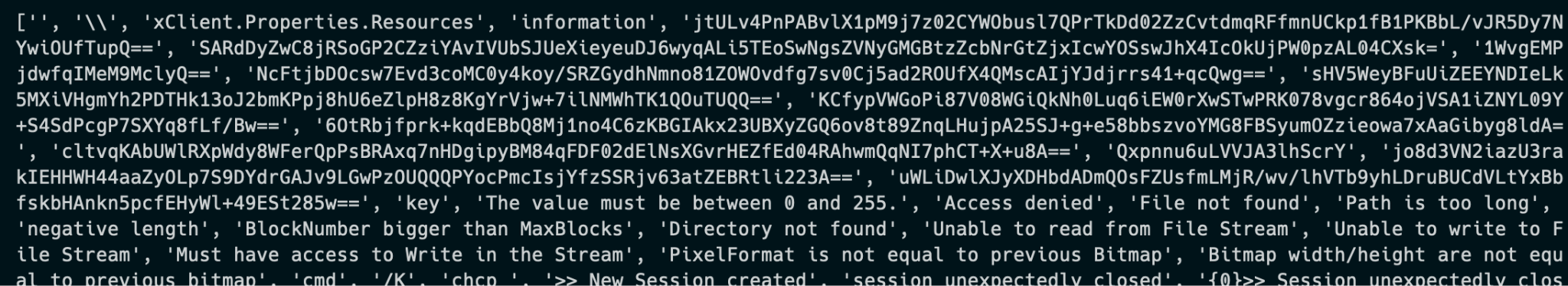
The samples not only have obfuscated code, but their configurations that contain the IoCs are also encrypted. For instance, in the case of Quasar RAT, its configurations are encrypted using AES and then encoded with Base64 as shown below in Figure 3.
With a quick sandbox run that was able to detect and fully parse the configuration from memory, we were able to identify the families of all 10 malware samples and extract their configurations. This revealed the networking IoCs so that we could immediately protect our customers.
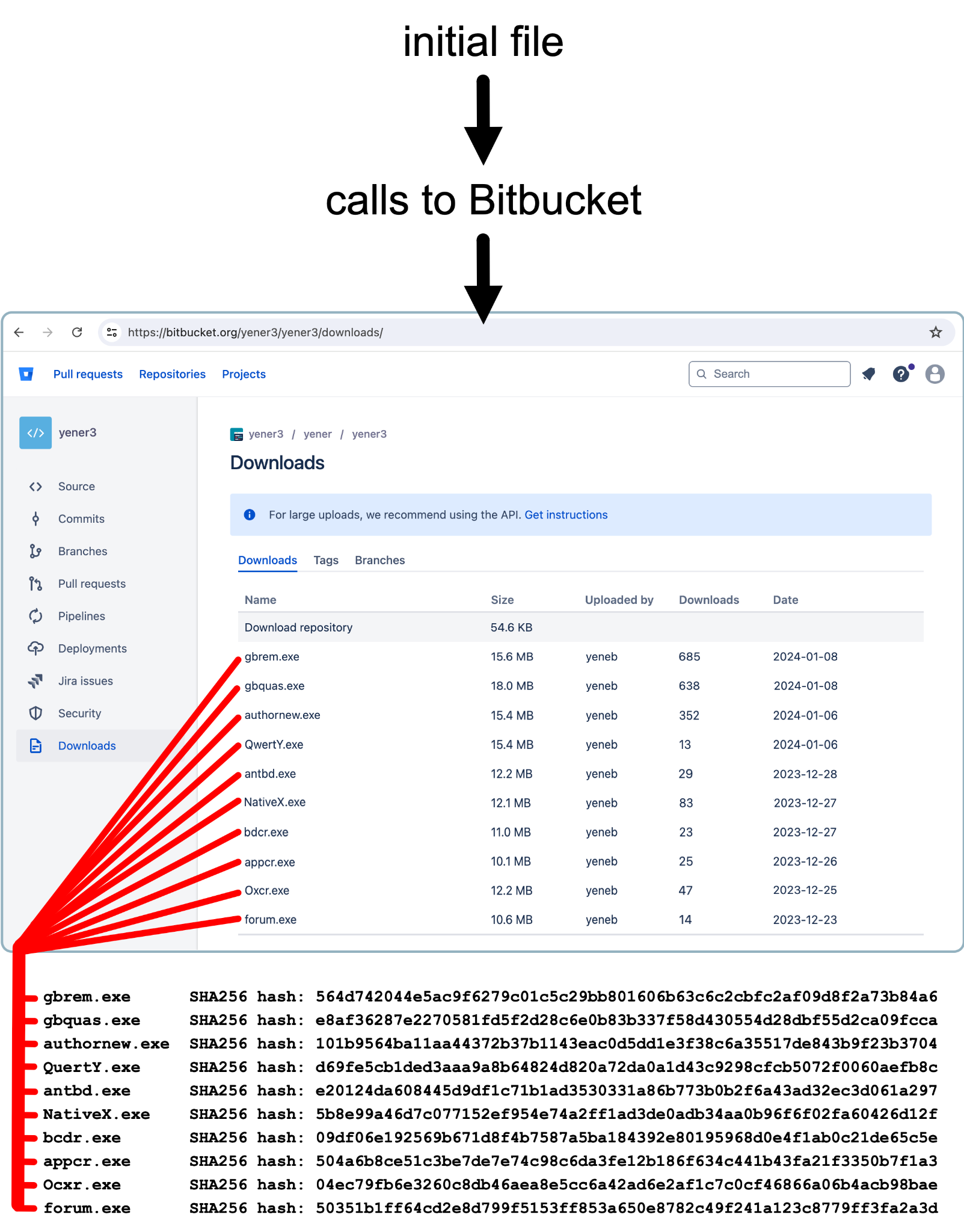
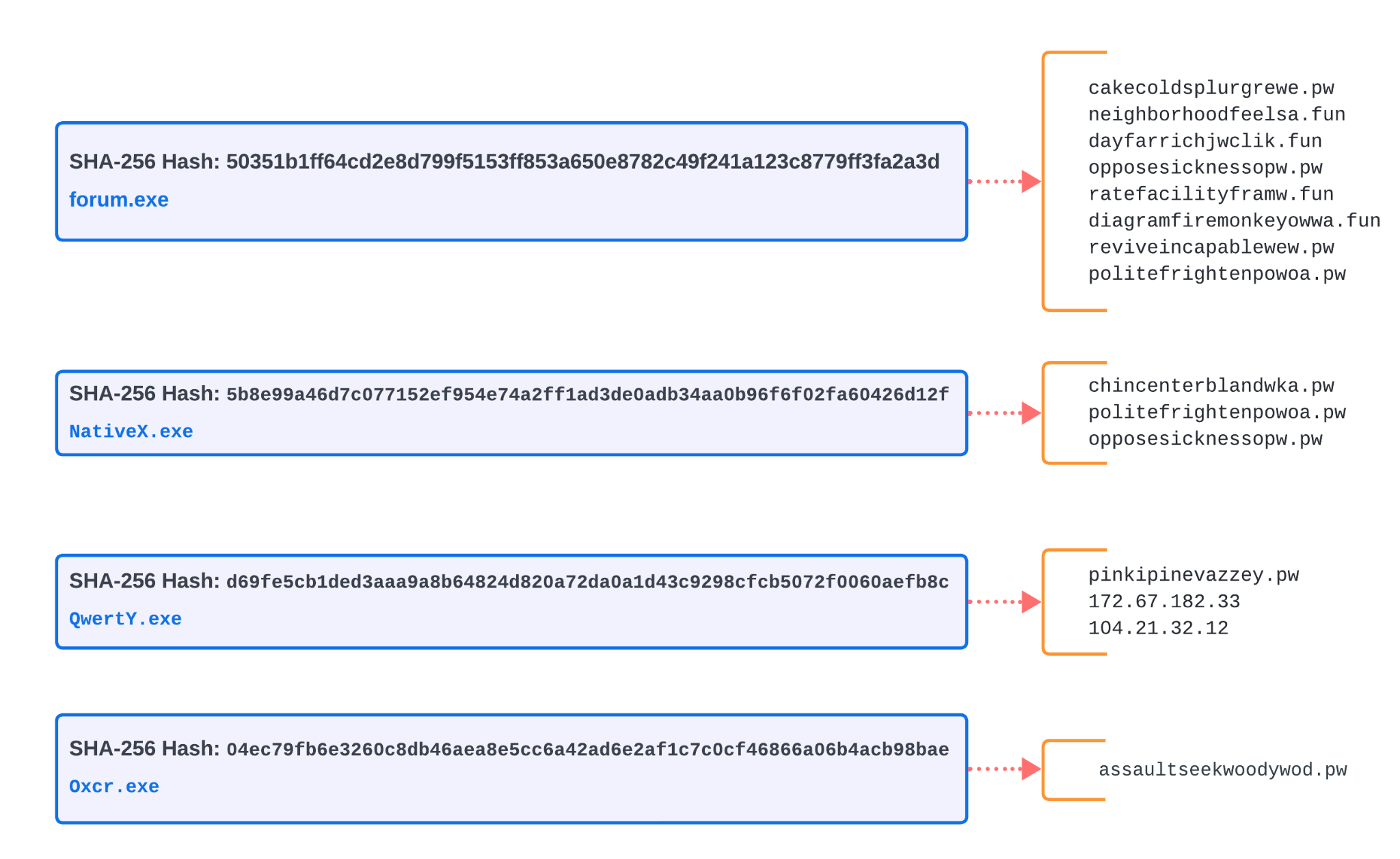
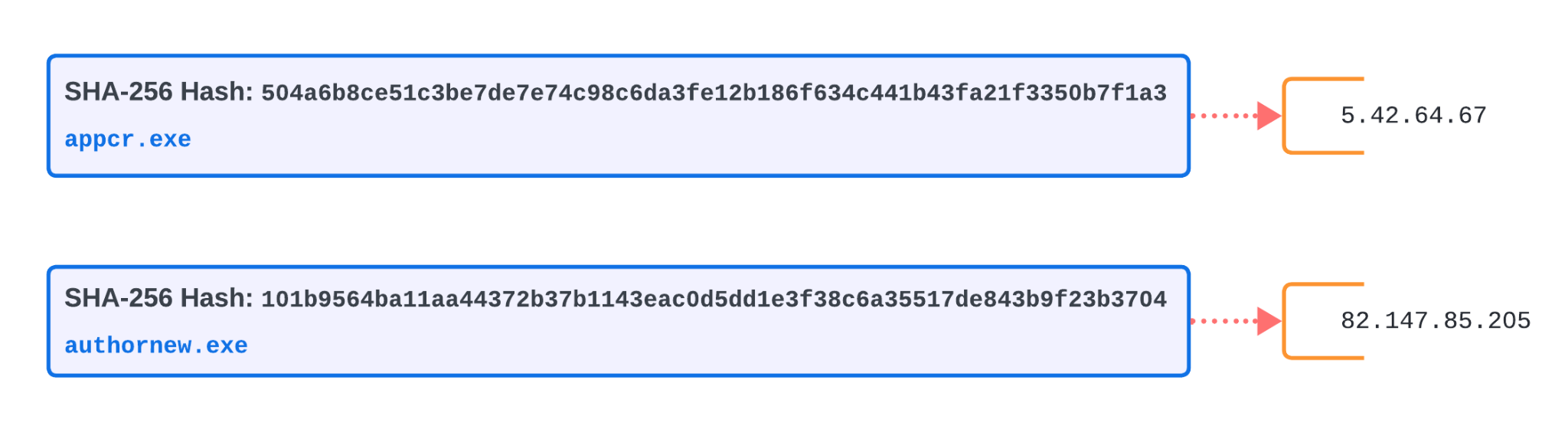
Figure 4 documents the initial step of IoCs extracted via the MCE, showing the relationship between the 10 samples recovered from the Bitbucket repository and their SHA256 hashes.
Configuration data extracted by the MCE reveals some patterns and shared attributes between the samples. Figure 5 shows domains and IP addresses used for C2 server by four samples we subsequently identified as Lumma Stealer. Two .pw C2 domains are shared by the top two examples in Figure 5, while all of them include C2 servers using various .pw domains.
The next two samples are Remcos RAT and Quasar RAT. These threats beacon to the same set of IP addresses for C2 servers, as shown below in Figure 6. Pivoting on that set of shared C2 servers, we discovered several other executables using the same IP addresses listed in Figure 6.
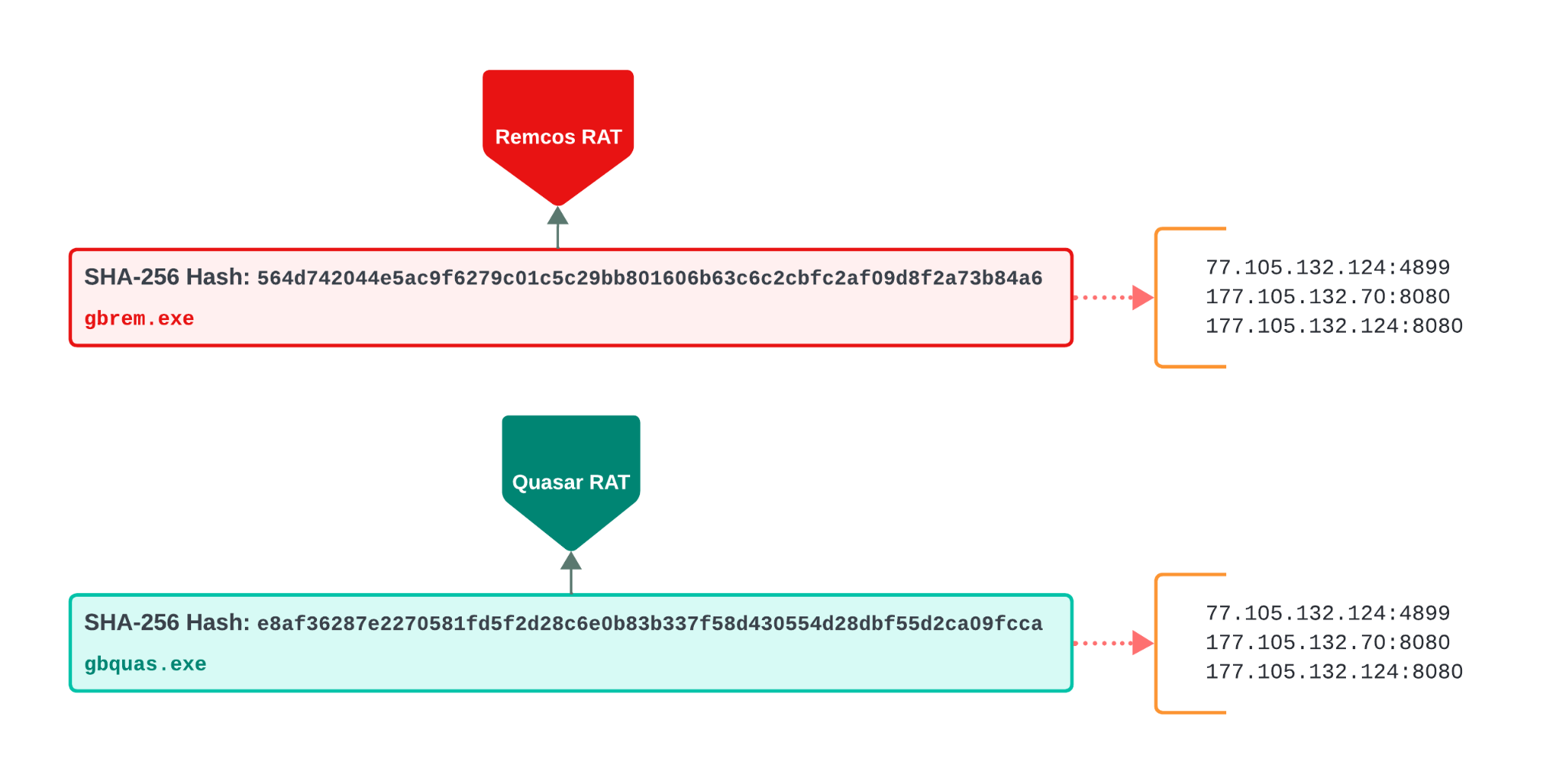
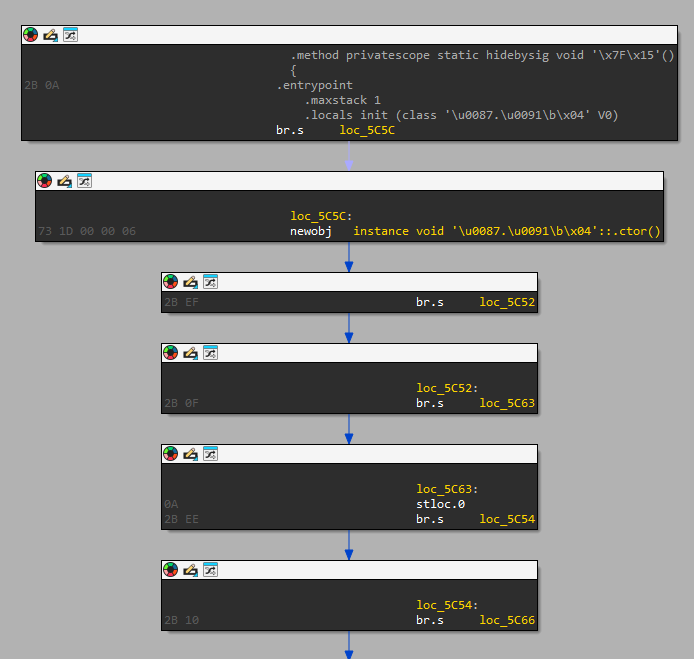
Figure 7 shows the obfuscated code from the Redline Stealer sample revealed by disassembler IDA Pro.
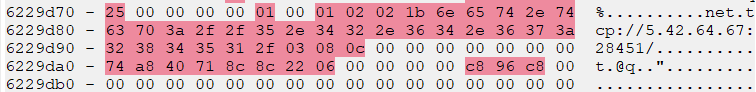
Figures 8 and 9 show the IoCs that we were able to extract from one of the Redline Stealer samples. Using MCE, we could easily identify and extract the C2 domains from memory.
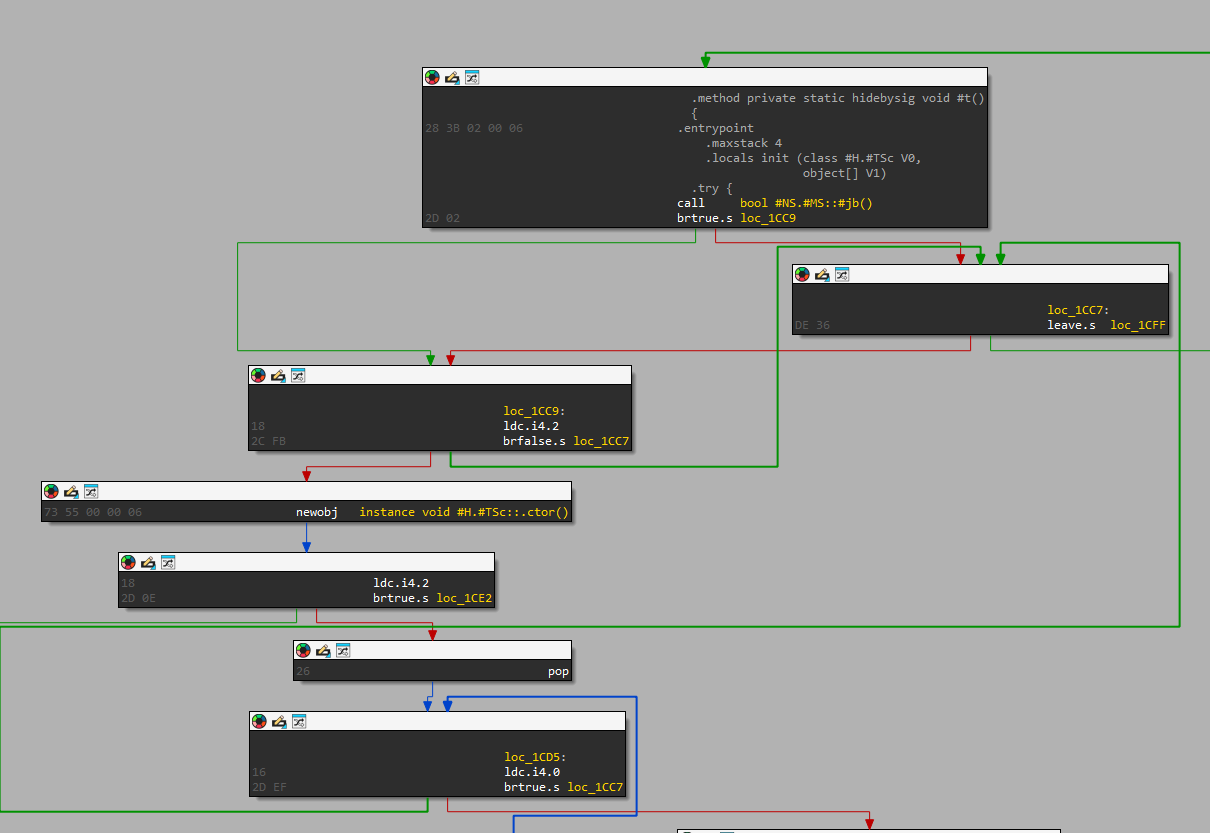
Our automated analysis of the last two binaries hosted on the Bitbucket repository revealed they are Vidar Stealer. Figure 10 shows a flow chart diagram for the configuration unpacking routine.
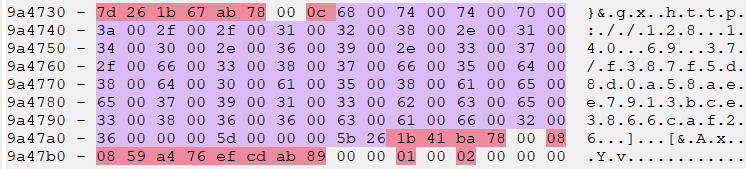
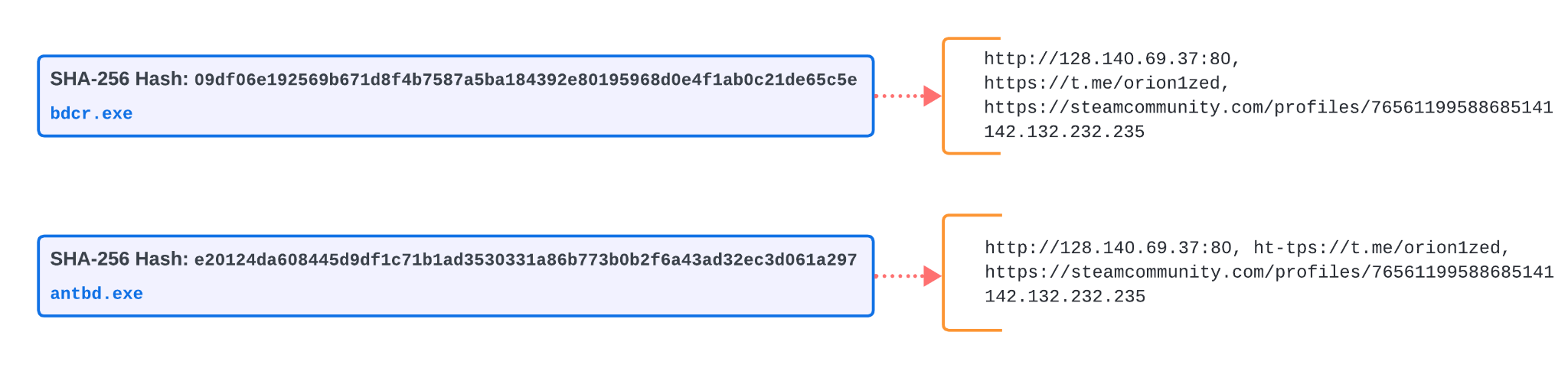
The MCE component of Advanced WildFire was also able to easily identify and extract these embedded C2 server information from memory as well. Figure 11 shows configuration information in a memory snapshot from one of the Vidar Stealer samples, and Figure 12 shows the C2 server information from both Vidar Stealer samples.
Conclusion
This post reveals the importance of accelerating malware analysis, because we often have no time for individual analysis on large groups of malware samples. We encourage readers to use whatever tools you have available to accomplish this. Our examples from this article show how we use the MCE component of Advanced WildFire to save significant analysis time and focus on identifying related IoCs more efficiently.
With the analysis, we could quickly determine the malware families of our newly discovered samples.
Quicker analysis enhances our ability to detect, analyze and develop effective countermeasures against malicious software. Furthermore, by sharing this quickly gained information, we can collectively stay ahead of cybercriminals to help safeguard our digital systems and networks.
Palo Alto Networks customers are better protected from the threats discussed in this article through the following products:
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
SHA256 Hashes of the Second Stage Payloads
- 50351b1ff64cd2e8d799f5153ff853a650e8782c49f241a123c8779ff3fa2a3d
- 5b8e99a46d7c077152ef954e74a2ff1ad3de0adb34aa0b96f6f02fa60426d12f
- d69fe5cb1ded3aaa9a8b64824d820a72da0a1d43c9298cfcb5072f0060aefb8c
- 04ec79fb6e3260c8db46aea8e5cc6a42ad6e2af1c7c0cf46866a06b4acb98bae
- 504a6b8ce51c3be7de7e74c98c6da3fe12b186f634c441b43fa21f3350b7f1a3
- 101b9564ba11aa44372b37b1143eac0d5dd1e3f38c6a35517de843b9f23b3704
- 09df06e192569b671d8f4b7587a5ba184392e80195968d0e4f1ab0c21de65c5e
- e20124da608445d9df1c71b1ad3530331a86b773b0b2f6a43ad32ec3d061a297
- 564d742044e5ac9f6279c01c5c29bb801606b63c6c2cbfc2af09d8f2a73b84a6
- e8af36287e2270581fd5f2d28c6e0b83b337f58d430554d28dbf55d2ca09fcca
Beacon domains/IPs extracted:
- 104.21.32[.]12
- 142.132.232[.]235
- 172.67.182[.]33
- 177.105.132[.]124
- 177.105.132[.]70
- 5.42.64[.]67
- 77.105.132[.]70
- 82.147.85[.]205
- assaultseekwoodywod[.]pw
- cakecoldsplurgrewe[.]pw
- chincenterblandwka[.]pw
- dayfarrichjwclik[.]fun
- diagramfiremonkeyowwa[.]fun
- http[:]//128.140.69[.]37:80
- https[:]//steamcommunity[.]com/profiles/76561199588685141
- neighborhoodfeelsa[.]fun
- opposesicknessopw[.]pw
- opposesicknessopw[.]pw
- pinkipinevazzey[.]pw
- politefrightenpowoa[.]pw
- politefrightenpowoa[.]pw
- ratefacilityframw[.]fun
- reviveincapablewew[.]pw
MITRE ATT&CK TTPs – created by AI
- Malware Analysis – TTP ID: T1203
- Automated extraction of configurations from multiple malware families to speed analysis.
- Utilization of Malware Configuration Extraction (MCE) to identify IoCs quickly.
- Sandbox runs to detect and parse configurations from memory.
- Command and Control – TTP ID: T1071
- Extraction of command and control (C2) addresses from malware samples.
- Identification of shared C2 server IP addresses among different malware samples.
- Obfuscated Files or Information – TTP ID: T1027
- Analysis of obfuscated code in malware samples to extract configurations and IoCs.
- Decryption of encrypted configurations, such as those using AES and Base64 encoding.
- Data from Information Repositories – TTP ID: T1213
- Pivoting on known malware samples to discover additional related samples in repositories.
- Utilization of Bitbucket repositories for hosting malware payloads.
Source: Original Post