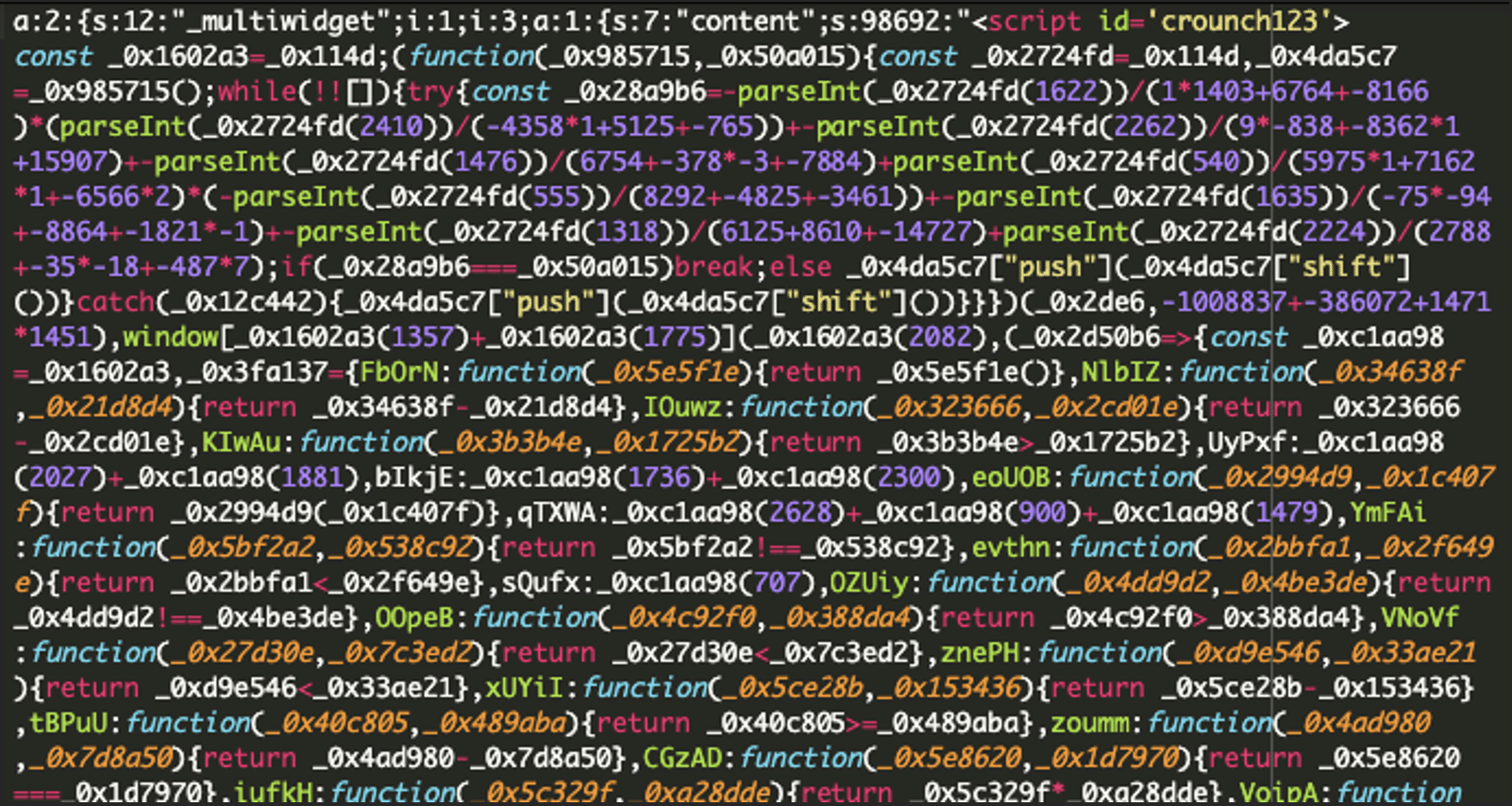
This article discusses a sophisticated credit card skimmer malware targeting WordPress websites, which injects malicious JavaScript into database entries to steal payment information during checkout. The malware operates silently and avoids detection by embedding itself in the WordPress database. Affected: WordPress
Keypoints :
- Credit card skimmer malware targets checkout pages on WordPress sites.
- Malware injects malicious JavaScript into the WordPress database, specifically in the wp_options table.
- It activates on checkout pages, either hijacking existing payment fields or creating fake forms.
- Data is captured in real-time and obfuscated using Base64 encoding and AES-CBC encryption.
- Stolen data is sent to attacker-controlled servers using navigator.sendBeacon.
- Detection is possible through Sucuri’s SiteCheck tool, which flags the malware.
- Regular updates and strong admin account management are crucial for mitigation.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: The malware uses HTTP requests to exfiltrate data to the attacker’s server.
- T1040 – Network Sniffing: The malware captures sensitive payment details from the checkout page.
- T1070.001 – File and Directory Permissions Modification: The malware avoids detection by embedding itself in the database instead of files.
Indicator of Compromise :
- [domain] valhafather[.]xyz
- [domain] fqbe23[.]xyz
- [url] https://publicwww.com/websites/%22script+id%3D%27crounch123%22
- [url] https://www.virustotal.com/gui/domain/valhafather.xyz
- [url] https://www.virustotal.com/gui/domain/fqbe23.xyz
- Check the article for all found IoCs.
Full Research: https://blog.sucuri.net/2025/01/stealthy-credit-card-skimmer-targets-wordpress-checkout-pages-via-database-injection.html