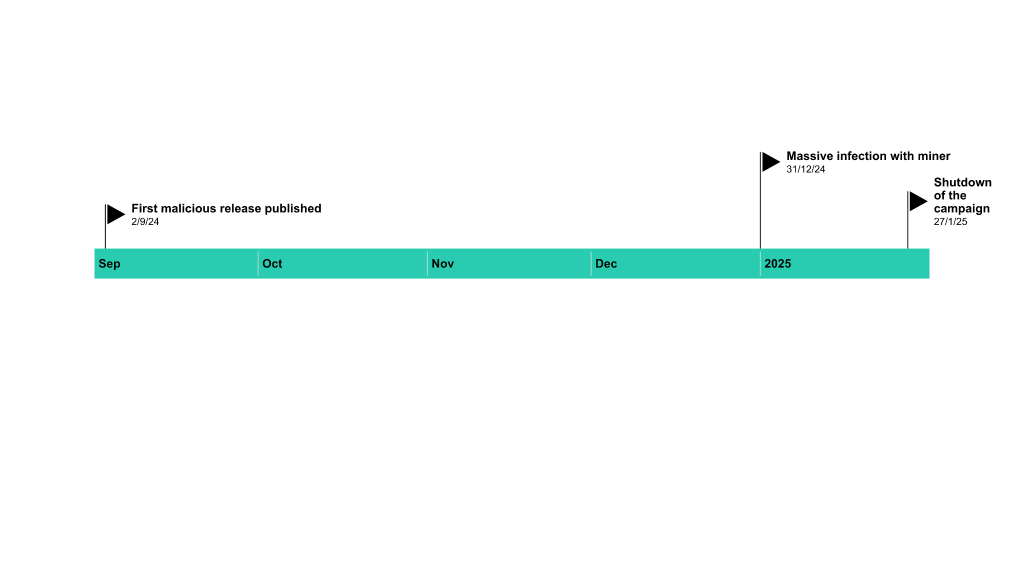
The article discusses a sophisticated cyber attack that began on December 31, where cybercriminals targeted users worldwide by distributing trojanized games via torrent sites to deploy the XMRig cryptominer. The attackers utilized various defense evasion techniques to deliver malicious content while exploiting reduced vigilance during the holiday season. The report highlights how the campaign was detected, the methods used to evade detection, and identifies affected users and organizations. Affected: individuals, businesses, countries (Russia, Brazil, Germany, Belarus, Kazakhstan)
Keypoints :
- Cyberattack launched on December 31, targeting users globally through trojanized games.
- The XMRig cryptominer was the payload spread via popular torrent sites.
- Malicious software utilized a sophisticated execution chain to evade detection.
- Kaspersky products identified the threat as various Trojan and heuristic variants.
- Trojanized games often repacked and uploaded to torrent platforms, gaining significant downloads.
- Initial infection method included checking for debugging environments before proceeding.
- Malware registered itself as a handler for certain file types to hide malicious activity.
- Targeted primarily individuals; some cases noted in corporate infrastructures.
- The campaign shows unique attribution challenges due to its methods and language cues.
- Effective communication obfuscation employed via DNS over HTTPS (DoH).
MITRE Techniques :
- Defense Evasion (T1562): The malware checks for debugging processes and terminates if found.
- Process Injection (T1055): The malware injects code into newly created cmd.exe processes.
- Command and Control (T1071): Utilizes hard-coded domains for communication like hxxps://promouno[.]shop.
- Credential Dumping (T1003): Collects fingerprints of the infected machines for identification purposes.
- Remote File Copy (T1105): Downloads additional malicious files from specific domains.
Indicator of Compromise :
- [Domain] 45.200.149[.]58
- [Domain] hxxps://promouno[.]shop
- [Domain] hxxps://pinokino[.]fun
- [Hash] 15c0396687d4ff36657e0aa680d8ba42461a0e74321706f5c99b0e92548a1986821d29d3140dfd67fc9d1858f685e2ac3c4d0a4dfd53e278b3683679e065627604b881d0a17b3a0b34cbdbf00ac19aa25cac1df1b9477e40992f4ee3cc2b06ed
- [Domain] 45.200.149[.]148
Full Story: https://securelist.com/starydobry-campaign-spreads-xmrig-miner-via-torrents/115509/
Views: 16

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português